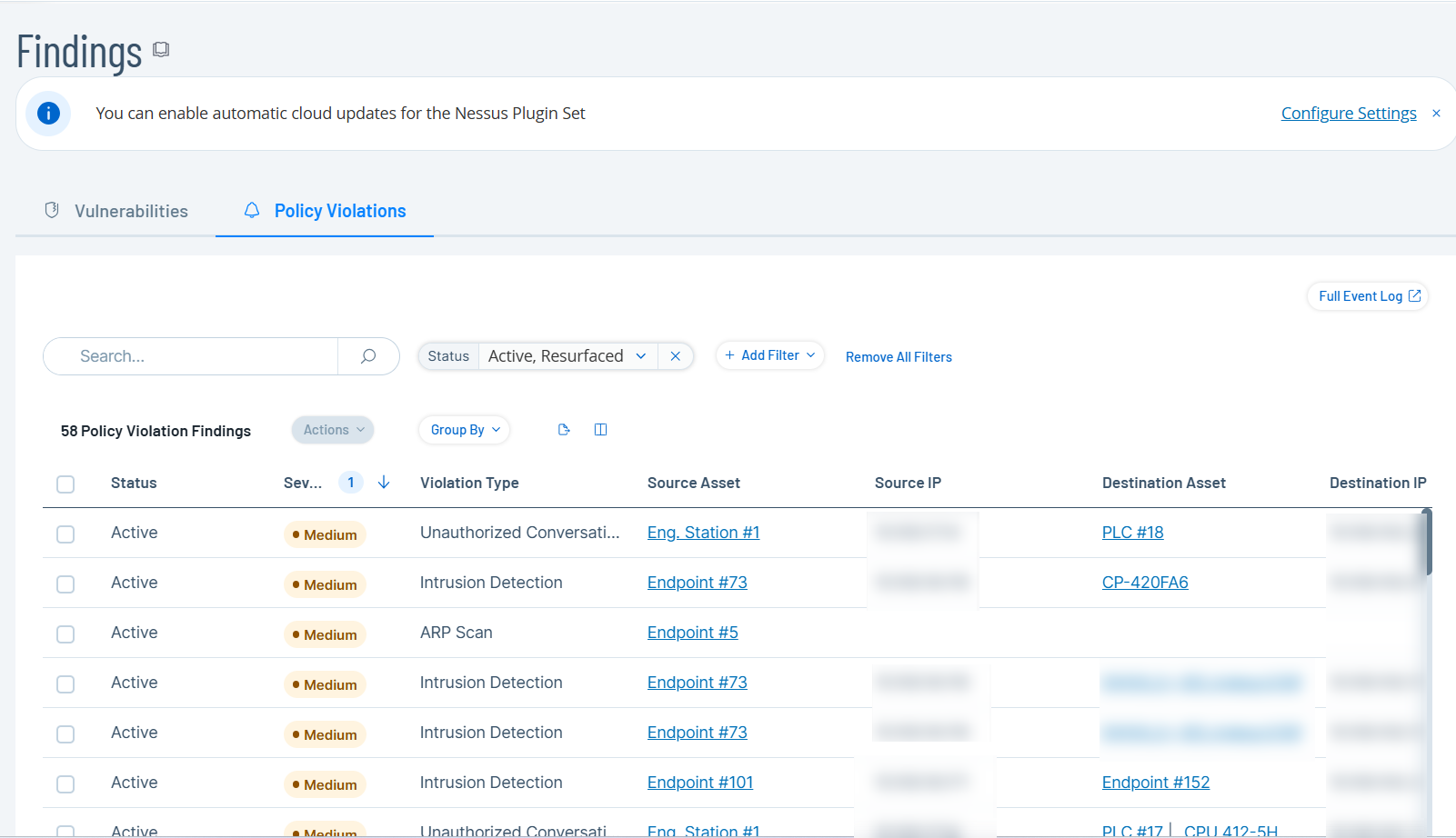
Policy Violations
Use the Policy Violations page to view all the events associated with the same policy, source, and destination. Each finding on the page is an aggregation of multiple events resulting from the same policy hits sharing the same source and destination.
To access the Policy Violations page:
-
In the left navigation menu, click Risks > Findings.
The Findings page appears.
-
Click the Policy Violations tab.
The Policy Violations page appears with the list of events.
The Policy Violations tab includes the following details:
Column Description ID The ID of the violation. Status The status of the violation: Active, Resurfaced, or Resolved. Severity The severity of the violation: High, Medium, or Low. Violation Type The type of violation. For example, Unauthorized Conversation and Intrusion Detection. Violation Category The category that the violation type belongs to. Policy The policy that caused the violation. Plugin Name The plugins associated with the violation. Mitre ICS Tactics The reason or "why" behind a specific Mitre Attack technique for Industrial Control Systems (ICS). Mitre ICS Techniques The method or the "how" an adversary achieves a tactical goal. Source Asset The asset where the violation originated. Source IP The IP address of the source asset. Destination Asset The asset where the violation terminated. Destination IP The IP address of the destination asset. Protocol The protocol associated with the violation. First Hit The time when the violation was first detected. Last Hit The time when the violation was last detected. Active Hits The number of events resulting in the violation. Asset Type The type of asset where the violation was detected. Asset Critical The criticality of the asset. Asset Vendor The vendor associated with the asset. Asset Family The family that the asset belongs to. Asset Tags The tags associated with the asset. Purdue Level The purdue level of the asset. Asset Location The region where the asset is located. Resolved On The date when the violation was resolved. Resolved By The user who resolved the violation. Comment The comments added by the user when resolving the violation. -
(Optional) You can do the following on the Violations page:
-
Customize columns as described in Customize Tables.
-
Filter the findings table. See Filter tables.
-
Export the data in the CSV format.
-
Actions menu
Resolve a finding
-
To resolve a finding:
-
Select the row of the finding and click Actions > Resolve.
The Resolve panel appears.
-
Type a comment for resolving the finding.
-
Click Save.
OT Security resolves the finding and the Plugin Details panel shows the status as Resolved.
Note: If the event reoccurs, OT Security reopens the finding and status appears as Resurfaced.
-
Exclude from policy
-
To exclude the finding from a policy:
-
Select the row of the finding and click Actions > Exclude from Policy.
The Exclude from Policy panel appears.
-
Select the Exclude Conditions.
Note: The exclude conditions are based on the last and most recent event. -
Provide the Exclusion Description.
-
Click Save.
OT Security excludes the most recent event from the policy.
-
Download last capture file
-
To download the last capture file:
-
Select the row of the finding and click Actions > Download Last Capture File.
OT Security downloads the capture file for the most recent event.
-
Plugin Details
To view the details of the plugin for the finding:
-
In the Policy Violations tab, click the row of the finding to view its plugin details.
The plugin details panel appears with the violation details from the OT Security plugin page.
The panel shows the details of the violation in four separate tabs: Details, Source, Destinations, and Policy.
Search for Events
To search for specific events that caused the violation:
-
To find the events for a specific finding, click
 Copy Finding ID.
Copy Finding ID. -
To go to the Events page, click the Full Event Log
 link.
link.The All Events page appears.
-
In the Search box, paste the Finding ID that you copied earlier.
OT Security lists the events for the specific finding.