Create Policy Exclusions
If a policy generates events for specific conditions that do not pose a security threat, you can exclude those conditions from the policy (that is, stop generating events for those particular conditions). For example, if you have a policy that detects changes in Controller State that occur during Workday hours, but you determine that for a particular controller it is normal for the state to change during those times, you can exclude that controller from the policy.
You can create exclusions from the Events page, based on events generated by your policies. You can specify which conditions of a particular event you want to exclude from the policy.
To resume generating events for the specified conditions at a later time, you can delete the exclusion, see Policies.
To create a policy exclusion:
-
In the relevant Events page, (Configuration Events, SCADA Events, Network Threats, or Network Events), select the event for which you want to create an exclusion.
-
In the header bar, click Actions or right-click the event).
The Actions menu appears.
-
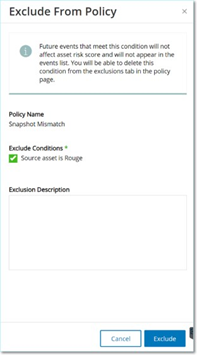
Click Exclude from Policy.
The Exclude from Policy window opens.
-
In the Exclude Condition section, by default all conditions are selected.
This causes events with any of the specified conditions to be excluded from the policy. You can deselect the check box next to each condition for which you want to continue generating events.
Note: For example, in the following window, to exclude the specified source and destination assets and IPs from this policy, but to continue applying this policy to UDP conversations between other assets in the network, then you should deselect “Protocol is UDP”.Note: The set of conditions that can be excluded differ depending on the type of policy, see the following table.
-
(Optional) In the Exclusion Description box, you can add a comment about the exclusion.
-
Click Exclude.
OT Security creates the exclusion.
The following table shows the conditions that can be excluded for each type of event.
Policy Category Event Type Excludable Conditions Controller Activities Configuration Events (Activities) -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
Controller Validation Change in Key State Source asset
Change in Controller State Source asset Change in FW Version Source asset Module Not Seen Source asset Snapshot Mismatch Source asset Network Asset Not Seen Source asset Change in USB Configuration -
Source asset
-
USB Device ID
IP Conflict -
MAC Addresses
-
IP Address
Network Baseline Deviation -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
-
Protocol
Open Port -
Source asset
-
Source IP
-
Port
RDP Connection -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
Unauthorized Conversation -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
-
Protocol
FTP Log In (Failed and Successful) -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
Telnet Log In (Attempt, Failed and Successful) -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
Network Threat Intrusion Detection -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
-
SID
ARP Scan -
Source asset
-
Source IP
Port Scan -
Source asset
-
Source IP
SCADA Modbus Illegal Data Address -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
Modbus Illegal Data Value -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
Modbus Illegal Function -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
Unauthorized Write -
Source asset
-
Destination asset
-
Tag Name
IEC60870-5-104 StartDT
IEC60870-5-104 StopDT
-
Source asset
-
Source IP
-
Destination asset
-
Destination IP
IEC60870-5-104 function code-based events -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
-
COT
DNP3 events -
Source asset
-
Source IP
-
Destination asset
-
Destination IP
-
Source DNP3 address
-
Destination DNP3 address
-