Software Supply Chain
The software supply chain is a major source of risk, especially since so many modern devices run some form of software. The COVID-19 pandemic accelerated migration to remote work and cloud computing, which made network devices an attractive target for attackers. For example, Secure Socket Layer Virtual Private Networks (SSL VPNs) were heavily targeted in 2021 even though the vulnerabilities were published in 2020 or earlier. VPN vulnerabilities have been very popular with ransomware groups, since they provide an entry point for attackers to gain access to the network. Ransomware groups leveraged legacy VPN vulnerabilities in Citrix, Fortinet, and Pulse Secure. In addition to these legacy flaws, attackers used zero-days in SonicWall and Kaseya to gain entry into targeted networks to deploy ransomware, or in the case of the Accellion flaws, to exfiltrate sensitive files.
Organizations were faced with higher risks from interdependencies of software libraries. Attacks on the software supply chain caused major disruption in the form of breaches and ransomware attacks. Third party software libraries that are embedded in applications can put an organization at risk. The more pervasive the library, the more likely there will be attempts to exploit it. Tenable’s 2021 Threat Landscape Retrospective provides valuable lessons learned as attackers relentlessly exploited the software supply chain. Software supply chain attacks were a key feature of the report. Open source libraries and repositories were compromised. Vulnerabilities in Log4j, a Java logging library used by hundreds of applications and services, is a prime example of how much impact one library can have.
The log4shell - High Risk Vulnerabilities: Apache, Log4j, and Java and log4shell - Log4j Concerns widgets shown below display how Tenable examined the software supply chain by using CPEs for an explicitly known problem. Tenable used the CPE strings in the widget template queries, since initial reports about the vulnerabilities contained information about certain Java Development Kits (JDKs) and other issues related to Log4j.
Tenable has provided the log4shell Critical Vulnerability dashboard template in Tenable Vulnerability Management. The Log4Shell, Log4Shell Remote Checks, and Log4Shell Vulnerability Ecosystem tactical scan templates are also available. A list of Tenable plugins to identify these vulnerabilities can be found on the Tenable Plugins Page.
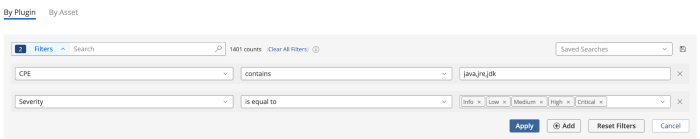
The CPE filter can be used to create custom widgets or workbench searches for critical software that is part of your organization’s supply chain. The log4Shell - Log4j Concerns widget uses the following filters for the Java Detection (JRE/JDK) Vulnerabilities Identified cell.
-
CPE contains java, jre, jdk
-
Severity is equal to Info, Low, Medium, High, Critical
Note: There are many Info severity plugins that contain useful information. The Info severity filter must be used to display plugins with an Info severity in dashboards and widgets. The filter used in the following image displays results for all severities, including Info.
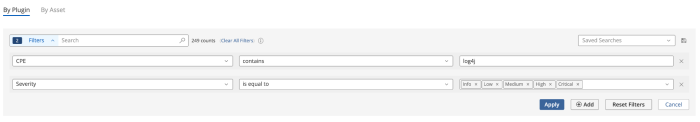
The log4Shell - Log4j Concerns widget uses the following filters for the Log4j (Installed) Vulnerabilities Identified cell.
-
CPE contains log4j
-
Severity is equal to Info, Low, Medium, High, Critical