Outstanding Remediations
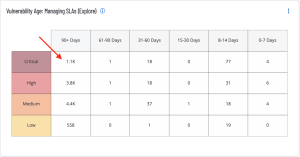
The time between when a vulnerability is discovered and when the vulnerability is typically exploited, or ‘time to exploit’ is rapidly decreasing. The CISA INSIGHTS report titled Remediate Vulnerabilities for Internet-Accessible Systems notes adversaries, on average, are able to exploit a vulnerability within 15 days. This is down from a previous average of over 30 days the previous year. This means that patching must be a priority for organizations to reduce threats as unpatched vulnerabilities over 15 days old begin to present a significant risk.
The Vulnerability Age: Managing SLAs widget provides a view of vulnerabilities based on severity and age. The columns display counts of vulnerabilities, which have been published within the specified time period, and are present in the organization. The rows display the severity level of the vulnerability.
Drilling Down in Tenable Vulnerability Management
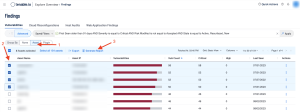
Security analysts can easily generate a report on the assets posing the greatest risk for outstanding remediations by drilling down into the details from this widget. Click on the cell with the most Critical vulnerabilities, which have been outstanding for over 90 days, and select Asset (1). In the following example, select the desired assets (2) and then select Generate Report (3).
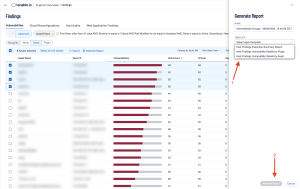
The Generate Report window is displayed, where the type of report, such as “Host Findings Vulnerability Details by Asset” can be selected (1), followed by clicking on the Generate Report button (2).
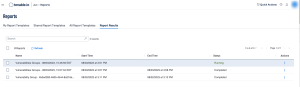
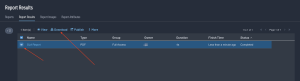
The Report Results page displays the running report, as shown:
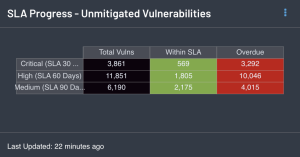
Tenable Security Center does not have a configuration option to define organization specific SLA time-frames. In lieu of that, the SLA Progress - Unmitigated Vulnerabilities component provides a summary of vulnerabilities based on the CVSS score and the SLA of 30, 60, 90 days. The best practice is to mitigate critical vulnerabilities in under 30 days, ~30 days for high, 60 for medium, and 90 for low.
Drilling Down in Tenable Security Center
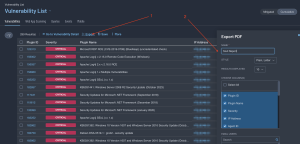
Security analysts can easily generate a report on the assets overdue, or within SLAs by drilling down into the details from this component . Click on the appropriate cell in the component, and from the Vulnerability Analysis page click on Export (1), and select CSV or PDF (in this example PDF was chosen). From the box that open on the right side of the page (2), enter a name for check the appropriate information, finally scroll to the bottom of the box and click submit.
A report will generate and will be available on the Report page. Check the box next to the report and then download the report to view the details.