Unsupported Software
Identifying assets running End of Life (EOL) applications is an important part of assessing and minimizing organizational risk since patches, updates, and security fixes are no longer available. Many standards state organizations must ensure that only software applications or operating systems that are currently supported and receiving vendor updates are added to the organization’s authorized software inventory. Organizations need to tag all unsupported software in the asset inventory.
Quick identification of unsupported operating systems and applications enables risk managers to see risks associated with EOL software. Identifying exposures provides the operations teams direction to implement, act, and prioritize remediation efforts to mitigate cyber risk. Tenable uses active methods to identify EOL products found in the environment by examining the Microsoft registry, common software installation locations, or using applications utilities such as YUM or APT in Linux systems. Risk managers are able to verify the operation team's activities and identity areas for risk mitigation.
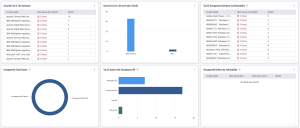
For Tenable Vulnerability Management, the Unsupported Software dashboard provides organizations with a clear and simplified method to identify EOL software and enables security managers to predict where risk will increase to help develop a mitigation plan.
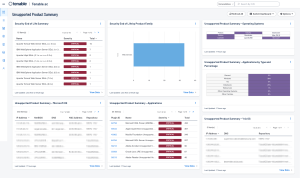
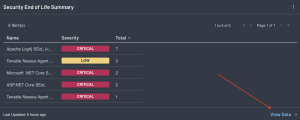
For Tenable Security Center customers, the Unsupported Product Summary displays details of unsupported (end-of-life) products found in the environment.
Security End of Life
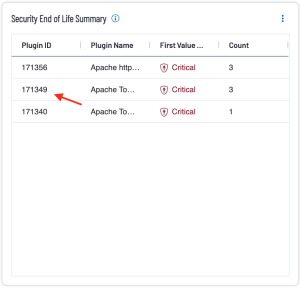
The Security End of Life widget (Tenable Vulnerability Management) and the Security End of Life Summary component (Tenable Security Center) displays information about products that have entered the Security End of Life state of the Security Maintenance Lifecycle. This component utilizes a filter containing the string 'SEoL' (Security End of Life) contained in the plugin name to identify these specific vulnerabilities. These plugins can be identified by looking at the plugin name which will contain the string 'SEoL', such as 'Apache httpd SEoL (2.1.x <= x <= 2.2.x)'. The new plugins provide a structured output and consistent updates to the content
Drill Down for Tenable Vulnerability Management
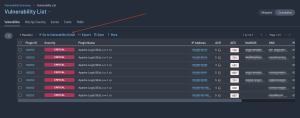
Drilling down into the data presents a vulnerability summary where additional details on each identified SEoL finding can be viewed. Click on a cell to drill into the Findings page for more details and to perform refined searches.
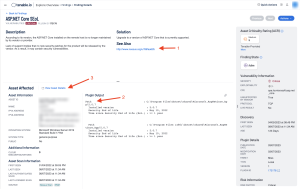
For more details, click on an asset (1) and select See All Details (2).
This page contains a lot of useful information, such as a link to additional resources (1), the path to the out-of-date application (2), and details about the affected asset (3).
Drill Down for Tenable Security Center
Drilling down into the data presents a vulnerability summary where additional details on each identified SEoL finding can be viewed. Click on View Data > to drill into the Findings page for more details and to perform refined searches.
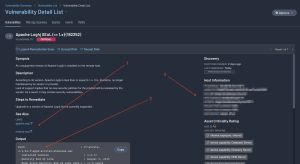
For more details, click on an asset (1) and select Go to Vulnerability Details.
This page contains a lot of useful information, such as a link to additional resources (1), the path to the out-of-date application (2), and details about the affected asset (3).
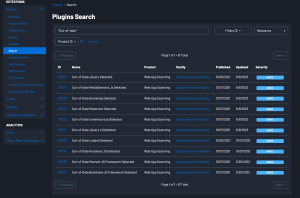
Out-of-Date Libraries
The Tenable Web App Scanner also contains a number of plugins that detect out-of-date libraries.