Vulnerability Management
Exploitability data for various exploit frameworks, including attack vectors, are presented in this section. Exploits leveraged in attacks are imported into various tools and services when the attack is made public. A license to use common exploit frameworks is easy to obtain and is used by security researchers and malicious attackers alike. The primary difference is that some tools require a considerable initial licensing cost to be useful, and others, such as Metasploit, may be freely available to the general public. This section describes risks associated with vulnerabilities that are included in exploit frameworks.
Exploitation frameworks, such as Metasploit, Canvas, and others, are designed to detect and exploit software and hardware vulnerabilities in target systems. These frameworks are powerful tools that enable penetration testers to probe and test devices for flaws and vulnerabilities. Often, these tools are used by those with malicious intent to easily compromise a target asset. Exploit frameworks do not require a high degree of technical knowledge to use. Open Source frameworks, such as Metasploit, are freely available and have the potential to carry more risk than a closed source costly alternative framework since they are readily available to download. Exploits in the frameworks that require significant initial cost, such as Canvas or Core, have the potential to carry less risk than the same number of exploits available with Metasploit.
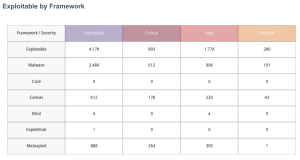
Exploitability by Framework
The Exploitability by Framework widget provides a summary of exploitable vulnerabilities by framework. This widget determines risks that may require prioritization over other vulnerabilities, by displaying vulnerabilities that can be exploited by a specific framework.
Each row in the widget focuses on a specific framework, except for the first two rows. The first row of the widget includes all exploit frameworks. However the “Exploitability Ease” property can be set to any plugin that is known to be exploitable, even when a framework is not used to exploit the vulnerability. The "Malware" property is set when there are vulnerabilities known to be exploited by malware in the wild. The frameworks will often be duplicated, meaning a vulnerability that is exploitable by Metasploit may also be exploitable using Core or Canvas. This is important to understand and recognize that the Exploitable row is not a sum of all the subsequent rows in count, but the plugins covered in the Exploitable row will be covered in the subsequent rows.
Each of the columns in the matrix focus on severity levels using the previously mentioned CVSSv3 ranges, with the exception of the Exploitable column. The Exploitable column is the sum of all severity levels, including the plugins with a CVSSv3 score less than 3.9, where the other columns focus on respective score ranges. Overall the metrics provided in this matrix enable organizations to understand the immediate threat of the vulnerability being present in the network. Should these metrics be present on a large percentage of assets, then the organization has a less mature vulnerability management program.
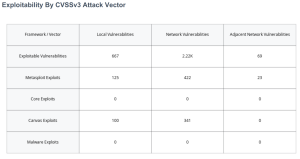
Exploitability by CVSSv3 Attack Vector
The Exploitability by CVSSv3 Attack Vector widget expands on the previous data by adding Attack Vector information to the exploit frameworks. Attack Vectors are part of the Base Metric group related to CVSS scoring and reflect an intrinsic characteristic that does not change over time. Local (AV:L), Network (AV:N), and Adjacent Network (AV:A vectors are displayed, which determine if the vulnerability is locally or remotely exploitable. Exploits that are available to the Network can be exploited remotely from the public internet. These exploits are the most serious threat since the attack vector is the entire internet. Exploits that are Adjacent have a smaller attack vector, since they must be launched from the shared physical or logical network or administrative domain. Exploits that are Local require access from an authorized, non-privileged user. Exploits that require local access are more difficult to carry out since the attacker must first gain access to an authorized account, or trick the authorized user into executing the exploit code.