Application Server Hardening
Application server hardening is the process of securing and fortifying an application server to reduce the device's exposure to potential threats and vulnerabilities. Even if an application is written following the best application security practices, the application can still be vulnerable if the server the application is running on is not secure. Multiple layers of defense must be addressed, including those not just limited to the application itself, but also to the host and operating system. Hardening involves implementing various security measures and established standards to enhance the device's resilience against attacks and unauthorized access. The primary goal is to reduce the attack surface and ensure the server and the applications remain available.
Application and server hardening comprises many of the aspects discussed in this guide, such as: configuring minimal privileges, disabling unnecessary services, keeping software up-to-date, secure communications, protection against common web application vulnerabilities, and periodic vulnerability scans. Application hardening is an ongoing process. Regularly assess the device’s security posture, stay informed about the latest threats and vulnerabilities, and update hardening measures accordingly. Compliance scanning is a great place to start the process.
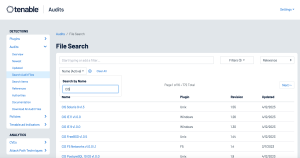
Compliance scanning is accomplished by conducting compliance checks using specific audit files and privileged credentials added to the scan policy. Use the Tenable Audit Search page with the Name filter to search for system hardening audits, such as the CIS Benchmarks, as shown in the following image for Tenable Vulnerability Management:
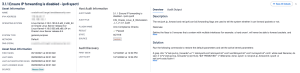
Host audit findings details can be found on the Findings page within Tenable Vulnerability Management. Click on a host audit finding to preview the details in the panel.
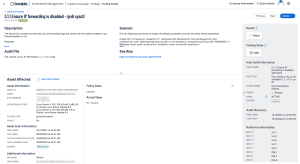
Select See All Details to open the details page. Details also contain the name of the audit file used.
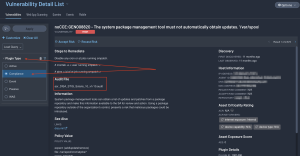
For Tenable Security Center, compliance results can be displayed by using the Plugin Type filter, and selecting the compliance radio button as shown below. Viewing the detailed information is similar to Tenable VM, and the audit file used will also be displayed in the detailed results as shown in the following image: