Detecting Services
Tenable Vulnerability Management and Tenable Security Center include plugins that detect running services and process information. The information from these plugins can display unregistered software running on the system that is not shown in the registry. The following plugins provide visibility into services that may appear only in running processes rather than in installed software packages.
-
58452 - Microsoft Windows Startup Software Enumeration.
-
70329 - Microsoft Windows Process Information.
-
70330 - Microsoft Windows Process Unique Process Name
-
70331 - Microsoft Windows Process Module Information.
-
70767 - Reputation of Windows Executables: Known Process(es).
-
70768 - Reputation of Windows Executables: Unknown Process(es).
-
70943 - Reputation of Windows Executables: Never seen process(es).
-
110483 - Unix/Linux Running Processes Information
A filter can also be applied using Plugin Family: Service Detection.
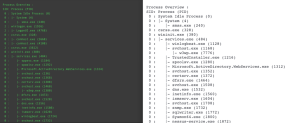
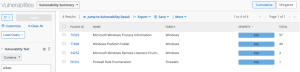
The following displayed sample output for plugin 70329 shows a “w3wp” process that could be suspicious. Output such as this can be taken from this plugin and used in a further investigative search using the text with the Plugin Output (Vulnerability Text) or CPE filter.
Example Plugin Search
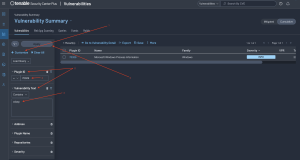
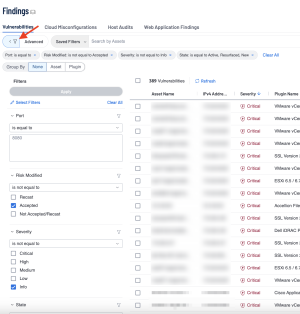
To perform this search in Tenable Vulnerability Management, from the Findings page, click on the Advanced button and then the filter tab, as shown in the following image:
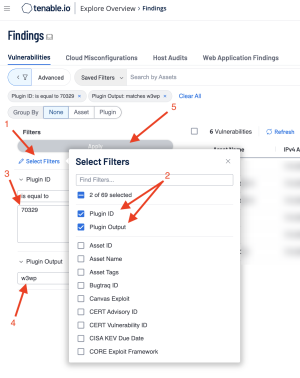
An interface to search based on selected criteria is displayed, as shown in the following image. Click on Select Filters (1) and select the desired filters for the query. In this example, Plugin ID and Plugin Output (2). Deselect any filters, which are not required for the search, by clicking on the check box. Enter the desired Plugin ID for the search (3), in this example 70329. Enter the Plugin Output for the search (4), in this example “w3wp.” Click the Apply button (5) to begin the search.
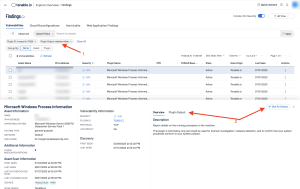
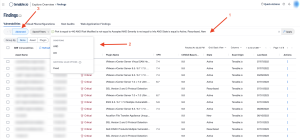
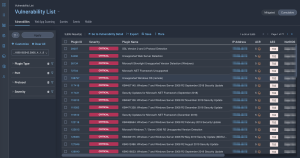
The search results page is displayed showing all assets containing the search query filter. For this example, the Plugin ID and Plugin Output (1) are shown. Clicking on a result displays summary information of the results. More details, including the Plugin Output can be found by clicking on either Plugin Output or the See All Details button (2).
The search can be pivoted from Plugin ID to Vulnerability Text. The following image displays all other scan results containing “w3wp” in the plugin output (vulnerability text). This information can now be investigated using the Vulnerability Detail List tool or the Vulnerability List tool in the drop-down menu above the results.
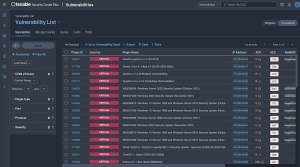
When using Tenable Security Center the process is similar. However, the starting point is from the Analysis tab, Click on Customize (1) and select the desired filters for the query, in this example, Plugin ID and Vulnerability Text (2). Deselect any filters, which are not required for the search, by clicking on the check box. Enter the desired Plugin ID for the search (3), in this example 70329. Enter the Plugin Output for the search (4), in this example “w3wp.” Click the Apply button (5) to begin the search.
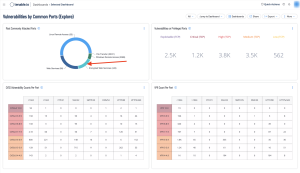
Addressing vulnerable services is a key step in reducing network risk. Vulnerable services may allow malicious actors to infiltrate the network, compromise assets, and exfiltrate information. The Vulnerabilities by Common Ports (available for both Tenable Vulnerability Management and Tenable Security Center) dashboard presents vulnerability information by common TCP ports and services. Clicking on any cell in the dashboard enables users to drill down into details about the assets on vulnerabilities in each category.
Drilling Down in Tenable Vulnerability Management
Additional filtering can be performed from either the Conditions field (1) or the Advanced (3) button. Clicking on the Conditions field opens the Conditions menu (2) to refine the filter search.
In the example shown in the following image, the AND operator was added (1) along with CVSSv3 Base Score (2), then a specification of greater than or equal to (3), the number 7, the AND operator (4), and finally Vulnerability Published (5).
Additional conditions can be added (1) or the filter can be applied by clicking on the Apply (2) button, as shown in the following image:
Another method to filter queries is to click on the filter button next to the Advanced button, which displays a user interface, as shown in the following image:
Drilling Down in Tenable Security Center
Additional filtering can be performed to reduce the number of returned vulnerabilities by clicking into a cell or if you are viewing a table clicking on View Data > will take you to the Vulnerability Analysis page.
In the following example, a filter for CVSS v3 Score (1) along with a custom range specification of between 9, and 7 (2).