Vulnerabilities by CVSS
The Common Vulnerability Scoring System (CVSS) is a metric from 0 to 10 assigned by the product vendor or the National Vulnerability Database (NVD) to indicate the severity of a vulnerability. CVSS scores are produced by the entity or organization producing and maintaining the product or a third party scoring on their behalf. CVSS Base Scores alone are not a measure of business risk nor do CVSS values account for real-world risk or asset criticality within an organization’s specific environment as scores are not likely to change once published.
Tenable recommends supplementing CVSS Base Scores with another temporal or environmental score to more accurately measure severity and rank threats. Such factors may include the risk of monetary loss due to breach, risks of damage or threat to life or property.
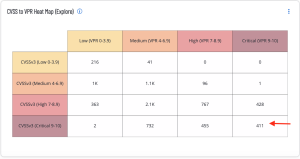
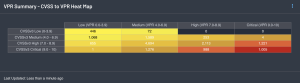
The CVSS to VPR Heat Map (Explore) widget provides a correlation between CVSSv3 scores and Vulnerability Priority Rating (VPR) scoring for the vulnerabilities present in the organization. Each cell consists of a combination of cross-mapping of CVSS and VPR scoring. Using a heat map approach, the filters begin in the left upper corner with vulnerabilities that present least risk. Moving to the right and lower down the matrix the colors change darker from yellow to red as the risk levels increase. Click on the cell in the lower right corner of the widget to drill down into details about the most critical CVSSv3 and VPR vulnerabilities.
Drilling Down in Tenable Vulnerability Management
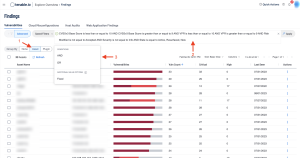
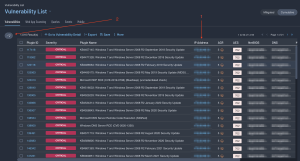
Clicking on any cell displays a Findings page with more details about the vulnerabilities in this category. For this example, the Findings are sorted by Asset (1). The filter used in the search is displayed in the center conditions field (2). Clicking on this field enables users to add additional Conditions (3).
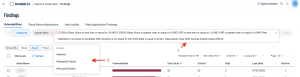
For example, users may want to see if any of the vulnerabilities in this category can be exploited through the Metaploit or Canvas frameworks. As shown in the following image, select the “AND” condition from the Conditions menu (1) and start typing the desired Conditions until they are displayed and can be selected (2). In the following example, the “AND” condition is selected, followed by “Canvas Exploit," then “exists," followed by “Metasploit Exploit.”
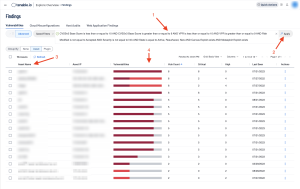
The full search is shown in the following image (1). Click on Apply (2) to search for these conditions. The results are then displayed, sorted by the Asset Name (3) with the greatest number of vulnerabilities (4) that meet the specified conditions in the filter search.
The Tenable Security Center component, as shown below, is similar in layout.
Drilling Down in Tenable Security Center
Clicking on any cell displays a Vulnerability Analysis page with more details about the vulnerabilities in this category. For this example, the Vulnerabilities will be sorted by IP Address (1). The filter used in the search is only displayed in the Filter field (2). Clicking on this field enables users to add additional Filters.
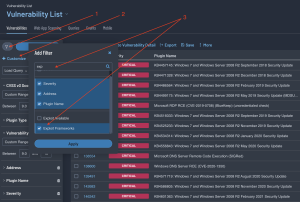
For example, users may want to see if any of the vulnerabilities in this category can be exploited through the Metaploit frameworks. As shown in the image below, select the filter icon (1) and select + Customize (2). In the Add Filter search area type “exp” to identify the Exploit Available Filter and check the box and click Apply (3).
From the filters, find the Exploit Frameworks filter that was just added and change the drop down to “Contains” and type “metasploit” in the text area (4). Click apply (5).
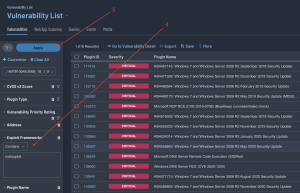
The results that are returned will only include vulnerabilities that include Metasploit in the Exploit Information.