Tagging and Dynamic Asset Lists
Before getting started an important first step is to understand tagging (Tenable Vulnerability Management) and Dynamic Asset Lists (Security Center). By an organisation classifying assets, Tenable can assist the organisation better focus their dashboards, reports and queries. When dealing with operating systems, risk managers need to understand which assets are internet facing and which are non-internet facing. Then, when dealing with applications the risk managers need to determine if the application is an online service, a high risk application or a low risk application. The organisation can make use of Asset Tagging in Tenable Vulnerability Management or Dynamic Lists in Tenable Security Center to ensure assets data can be grouped appropriately and be better prioritised.
An asset tag (Tenable Vulnerability Management) is primarily composed of a Category:Value pair. For example, if you want to group your assets by their connection to the internet, create a new category with the value internet facing. You can then manually apply the tag to individual assets, or you can add rules to the tag that enable Tenable Vulnerability Management to apply the tag automatically to matching assets. For more information on creating a tag visit Tenable’s Tagging documentation.
In all queries used in Tenable Vulnerability Management and/or Tenable Security Center, using tags or asset lists will enable the user to focus their scan data and results to give them more relevance to the Essential Eight. The ACSC wants organizations to differentiate between Internet-facing and non internet-facing assets to determine different Service Level Agreement (SLA) timelines. For example, internet facing applications should be patched within 48 hours as opposed to non internet-facing applications should be patched within two weeks. These SLA differences are useful to identify and group together the detected assets based on whether they’re internet facing or not.
To identify internet-facing assets in Tenable Vulnerability Management and/or Tenable Security Center, you can create tags that focus on key characteristics of these assets. These tags can be applied manually or automatically using filtering rules, such as identifying assets with public IP ranges, open ports (e.g., 80 or 443), externally accessible vulnerabilities, or cloud metadata indicating public accessibility.
To create a tag in Tenable Vulnerability Management, first click on the setting gear in the top right and then select the Tagging icon.
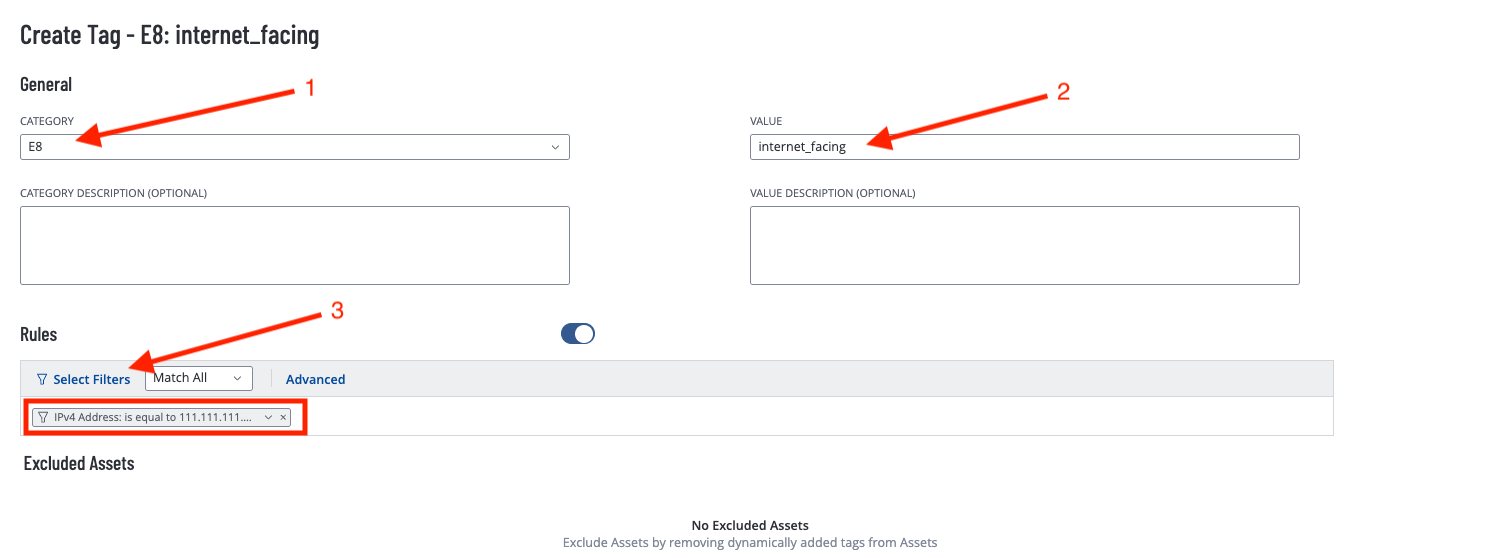
Within the tagging menu, you will be presented with all the previously created tags. Click the Create Tag icon in the top right corner to create a new tag. From the Create Tag screen, create a new tag by first selecting the Tag Category (in this example E8), then entering a value (in this example internet_facing). Then under Rules, select the Select Filters drop down and create a set of rules based on the organisations classification of assets (in this example, IPv4 Assess is equal to 111.111.111.111)
Multiple rules can be applied, and previously created Tags can be used as a filter. For example, a follow up rule in a new tag could be Tags: is not equal to E8: internet_facing for the ASD Essential 8: Other Assets dashboard, which would exclude assets tagged as internet facing from being displayed within widgets.
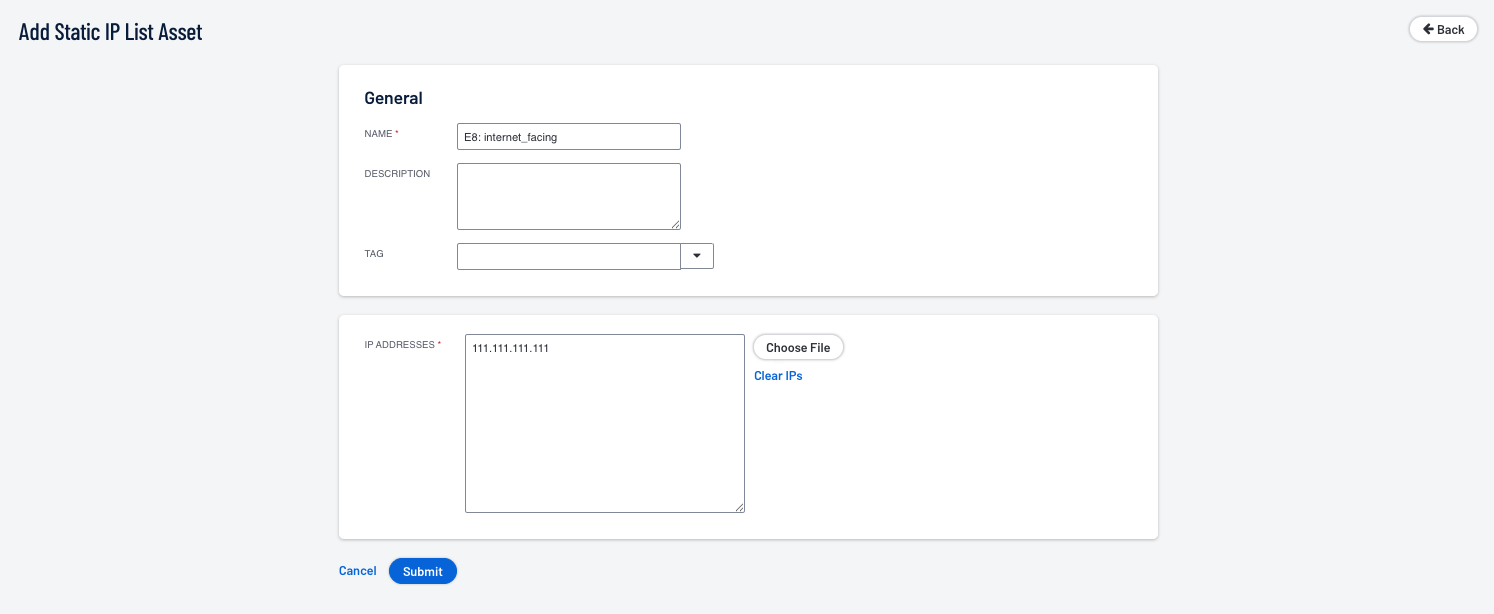
To create a Dynamic Asset in Security Center navigate to Assets and select the option Add to display the Asset templates page. From the Templates page select the appropriate option. For this example we will follow a similar procedure as the method shown with Tenable Vulnerability Management by selecting the Static IP List template.
Once the template is chosen complete the required fields.
If you would like to add additional rules to the template, in addition to a static IP address, select the Dynamic template. The Dynamic template allows additional rule and rule groups to be applied.
Grouping assets by their roles, such as application servers or customer-facing portals, can further enhance visibility. Setting up dynamic tagging ensures that these tags are applied automatically to new assets meeting the criteria, making monitoring and managing internet-facing systems effectively easier. One filter that can also be considered when creating rule based asset tags is "Public." The Public filter specifies whether the asset is available on a public network. A public asset is within the public IP space and identified by the `is_public` attribute in the Tenable Vulnerability Management query namespace. An exhaustive list of possible Asset filters can be found here.