Host Audit Plugin Type
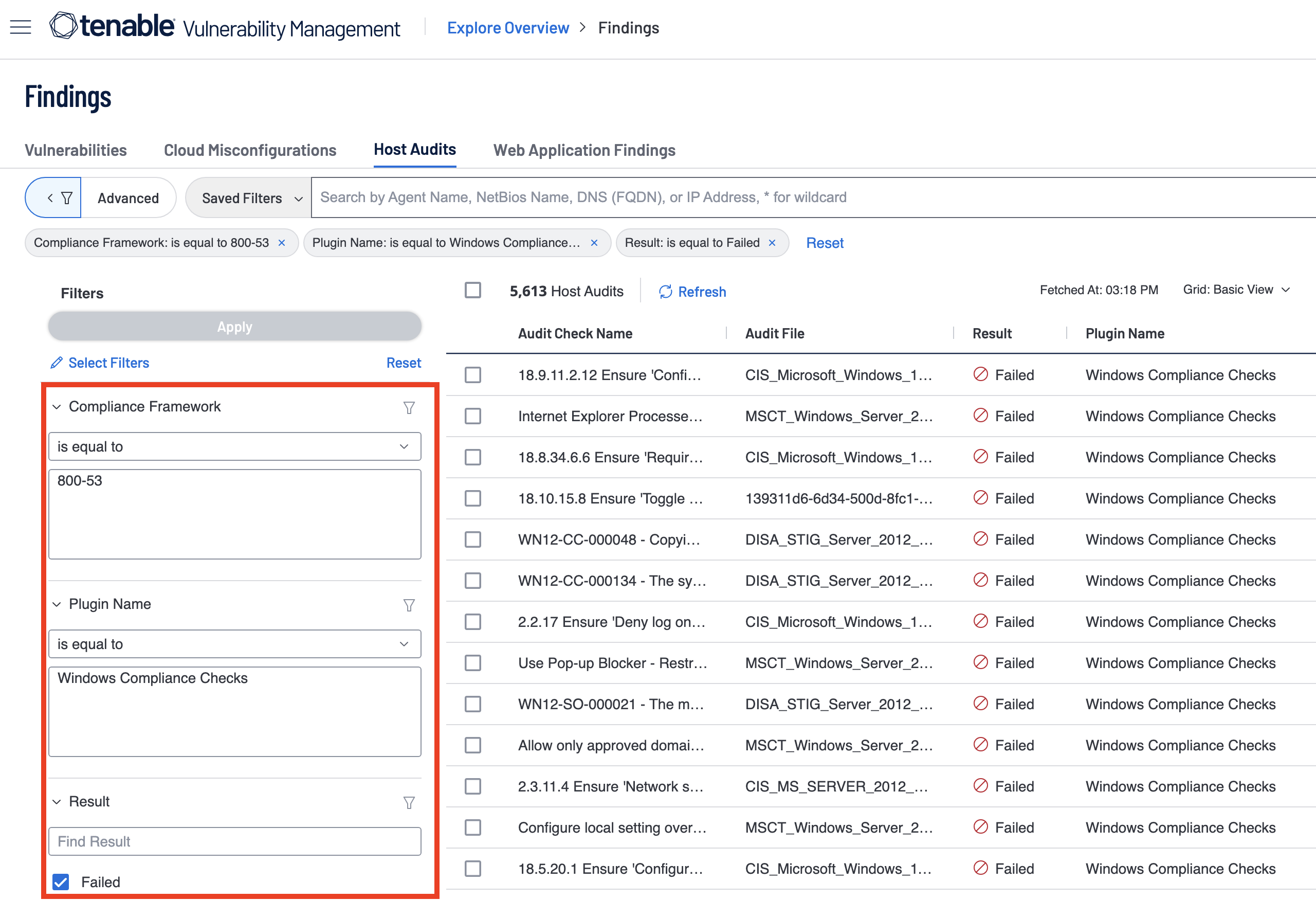
Within Tenable Vulnerability Management the Host Audits Section of the Findings page and inside custom widgets you’re able to search for Host Audit by plugin type. The differences with Tenable Vulnerability Management and Tenable Security Center querying a similar query as the previous is: instead of the Cross References Filter inside of Security Center to single out audit file types we use the Plugin Name Filter: Instead of the Vulnerability Text filter to single out a specific compliance framework, we use the Compliance Framework Filter: and instead of using severity for failed results we simply use the Result Filter.
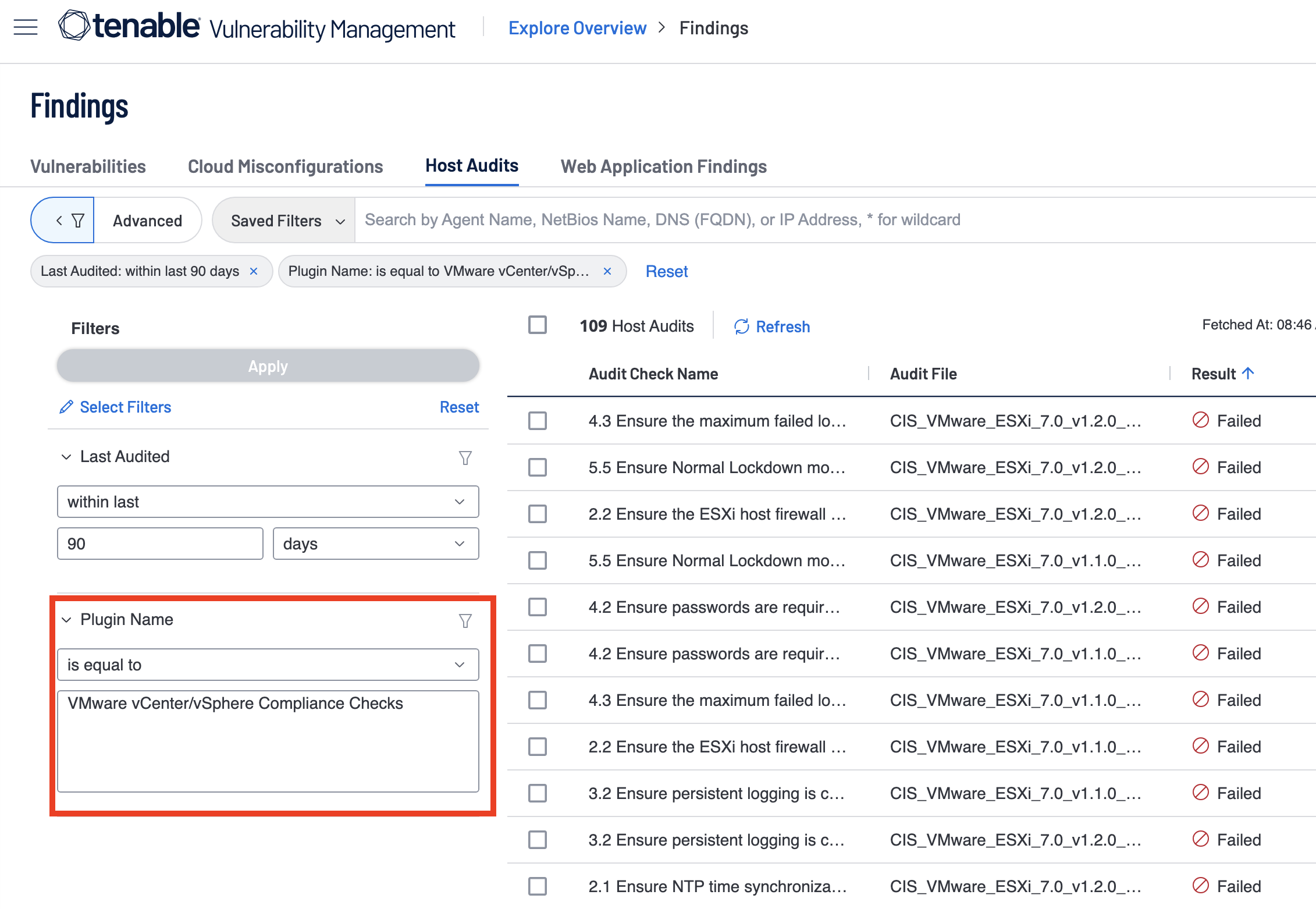
As mentioned, inside Tenable Vulnerability Management you’re able to search for Host Audits by using the Plugin Name Filter within the Host Audits section of the Findings page; this search results in all audit checks that match the plugin name being displayed.
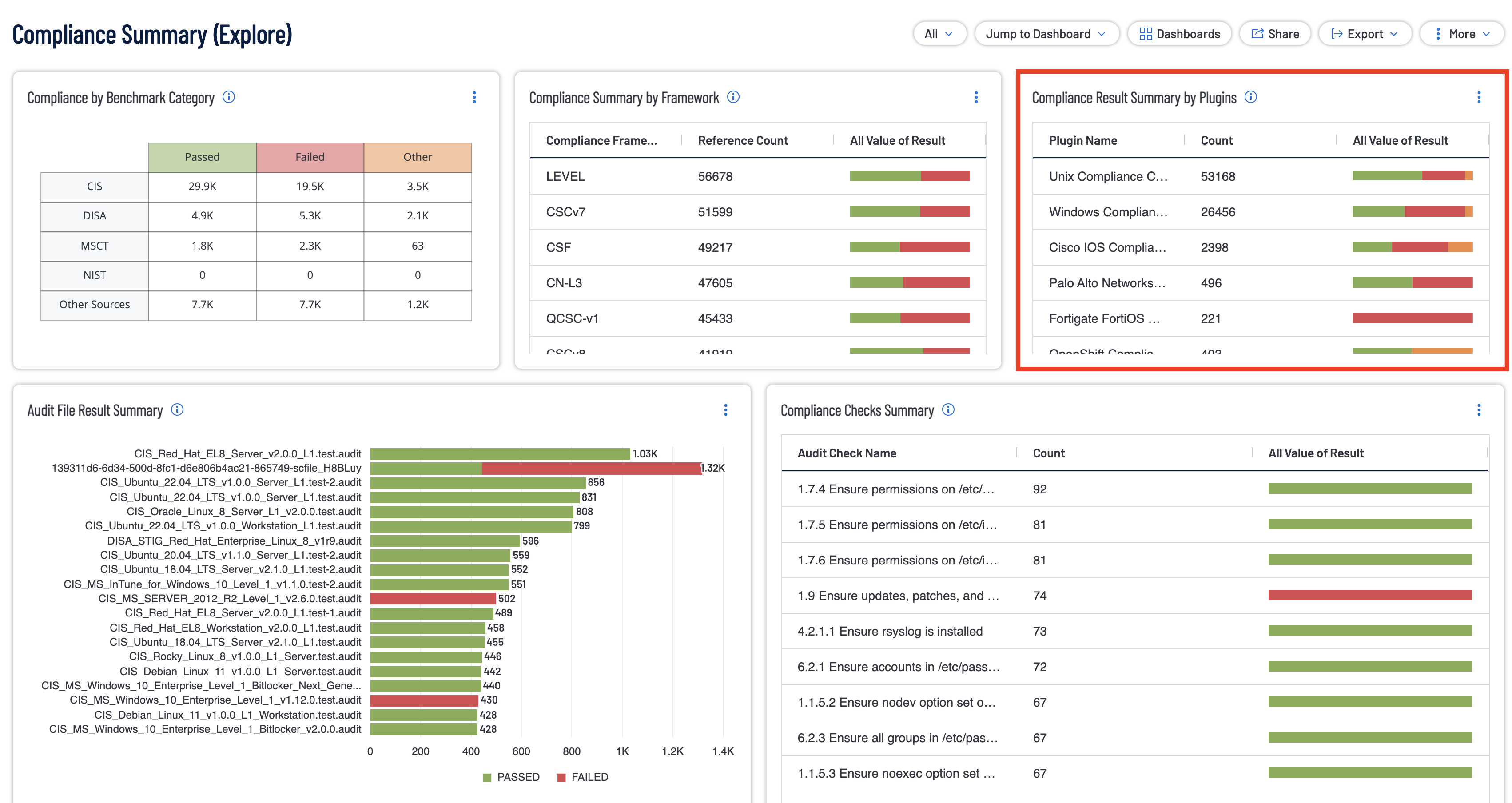
A user can quickly determine which compliance checks have been run by checking the Compliance Result Summary by Plugins widget within the Compliance Summary dashboard. This widget has no filters applied to it and instead is being grouped by plugin name and only host audit plugins. The widget is a quick way to determine which Host audit plugin type has had the most results (represented by the “Count” column) and a quick breakdown of the result types. Hovering over the bar displays the counts of Passed (green), failed (red), and Other (orange) result types.
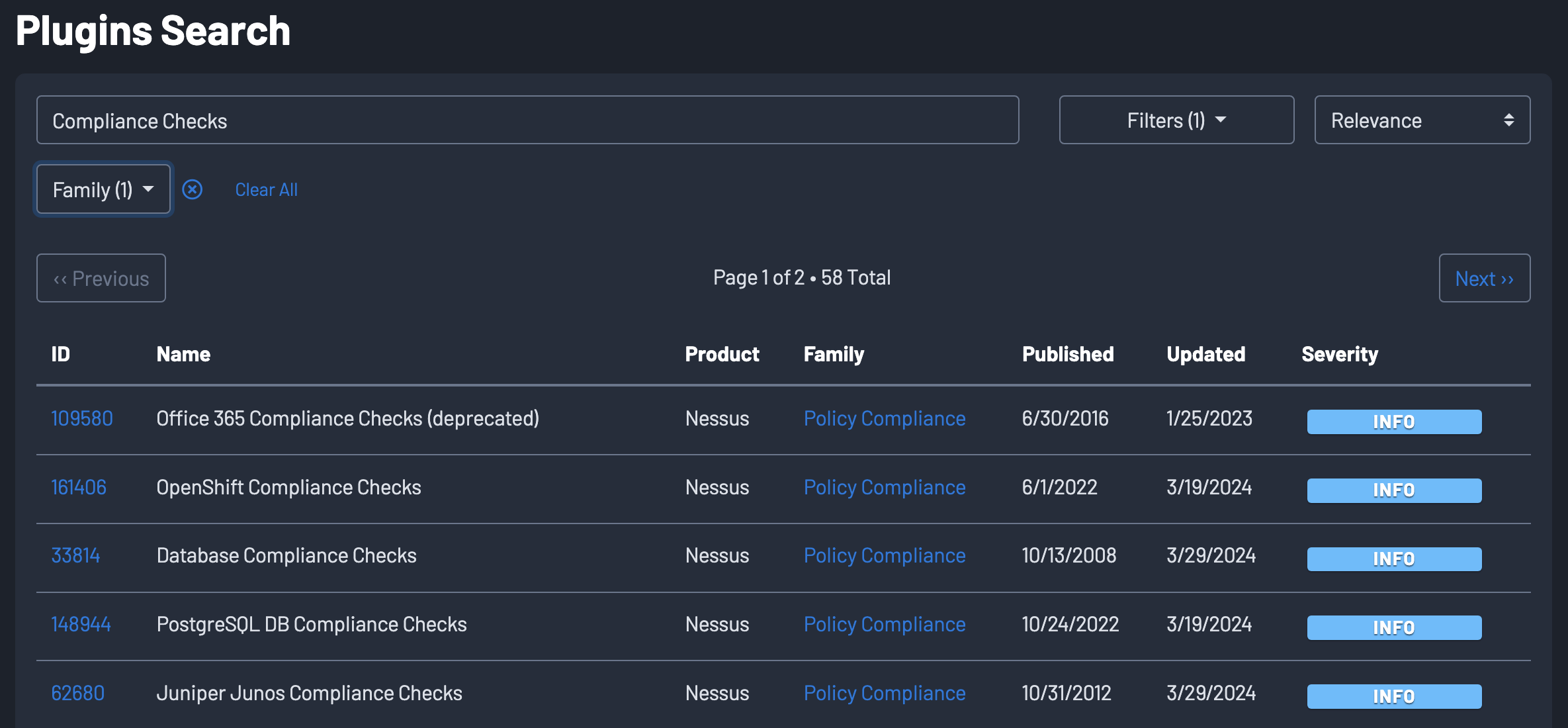
There are 58 available Compliance check plugins. All the possible Compliance check plugins can be seen by using Tenable’s Plugins Search and searching for “Compliance Checks'' and using the “Policy Compliance” Family filter.
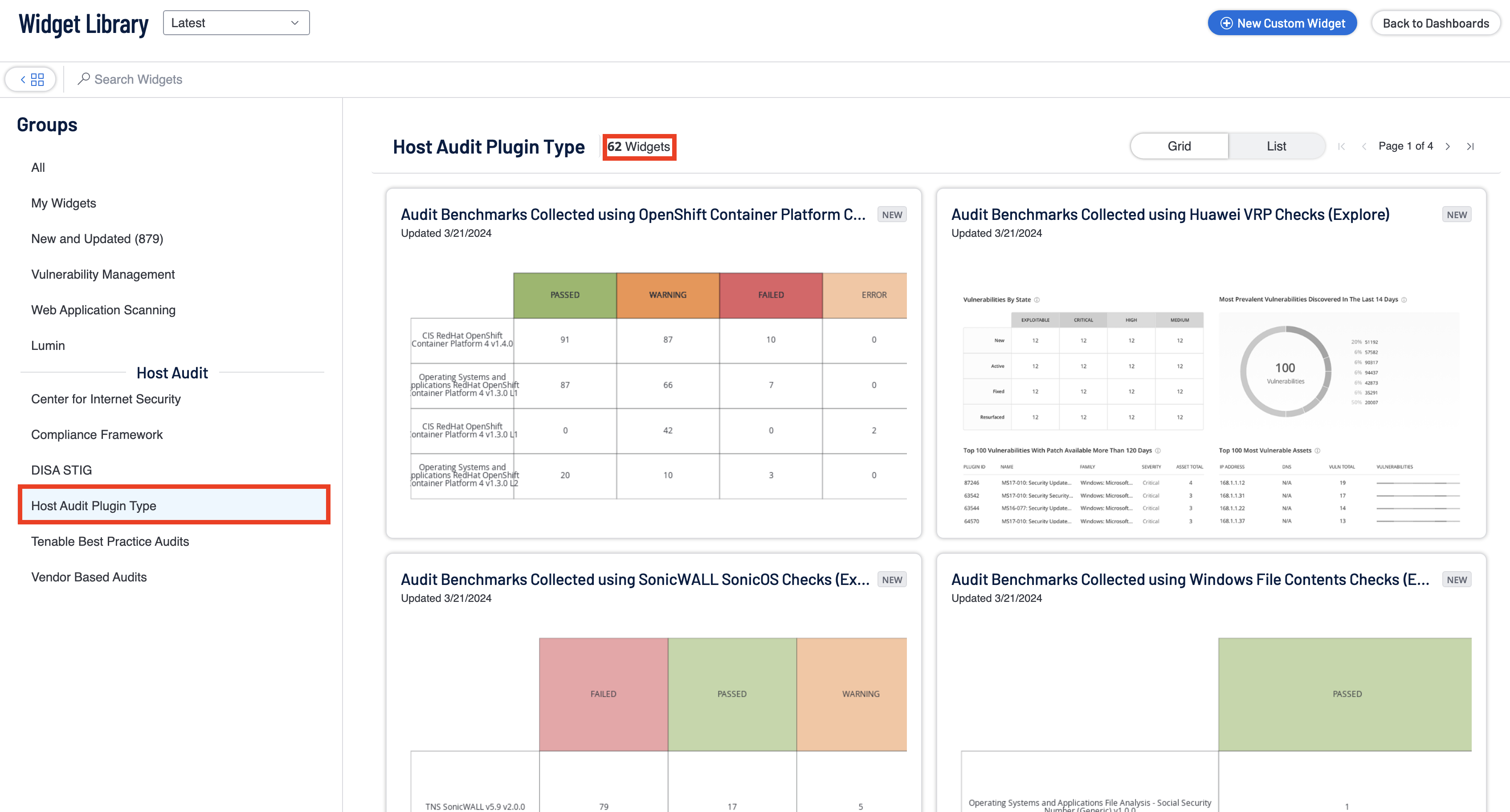
A more detailed breakdown of Host Audit Plugin Types can be seen by navigating to the Widget Library and selecting the Host Audit Plugin Type Group. This action results in currently 62 widgets, four widgets come from the Compliance Summary dashboard and the other 58 widgets represent each of the 58 available compliance check plugins. Each of the 58 Compliance check widgets are laid out as a matrix and display benchmark run on the y-axis labels of the matrix, and the result types on the x axis. The counts inside the matrices represent the count of the specific result type for the benchmark which was selected.
Within Tenable Security Center there are 47 Available Compliance Plugins that can be queried. All the available compliance plugins are below; the text in the parenthesis is the reader-friendly name of the plugin so, for example, when querying the plugin you’ll want to use ‘oracledb’ for Oracle DB.
| adtran (Adtran NetVanta) |
mongodb (MongoDB) |
| alcatel (Alcatel TiMOS) | ms_sqldb (MS SQL DB) |
| amazon_aws (Amazon AWS) | mysqldb (MySQL DB) |
| arista (Arista EOS) | netapp (NetApp Data ONTAP) |
| arubaos (ArubaOS) | netapp_api (Netapp API) |
| as/400 (IBM iSeries) | openshift (OpenShift Container Platform) |
| bluecoat (BlueCoat ProxySG) | oracledb (Oracle DB) |
| brocade (Brocade FabricOS) | ovalUnix (OVAL Unix) |
| checkpoint (Check Point GAiA) | ovalWindows (OVAL Windows) |
| cisco (Cisco IOS) | palo_alto (Palo Alto Networks PAN-OS) |
| cisco_aci (Cisco ACI) | postgresqldb (PostgreSQL DB) |
| cisco_firepower (Cisco Firepower) | rhev (RHEV) |
| citrix_application_delivery (Citrix Application Delivery) | scapLinux (SCAP Linux) |
| database (Database) | scapWindows (SCAP Windows) |
| extreme_extremexos (Extreme ExtremeXOS) | sonicwall (SonicWALL SonicOS) |
| f5 (F5 Networks) | sybasedb (Sybase DB) |
| fortigate (Fortigate FortiOS) | watchguard (WatchGuard) |
| genericssh (Generic SSH) | windows (Windows) |
| hpprocurve (HP ProCurve) | windowsfiles (Windows File Contents) |
| huawei (Huawei VRP) | xenserver (Citrix XenServer) |
| ibm_db2db (IBM DB2 DB) | zte_rosng (ZTE ROSNG) |
| juniper (Juniper Junos) |
When trying to have a specific query unix and 800-53 benchmarks run, one would think utilizing the Cross Reference filter with ‘auditFile|unix, 800-53|*’ would work but this would not. The Cross Reference filter has an implied ‘OR’ operator to it. The above example would result in all unix audit file benchmarks as well as all benchmarks that have 800-53 as a reference including non-unix audit files. In this scenario we want to utilize the two filters;
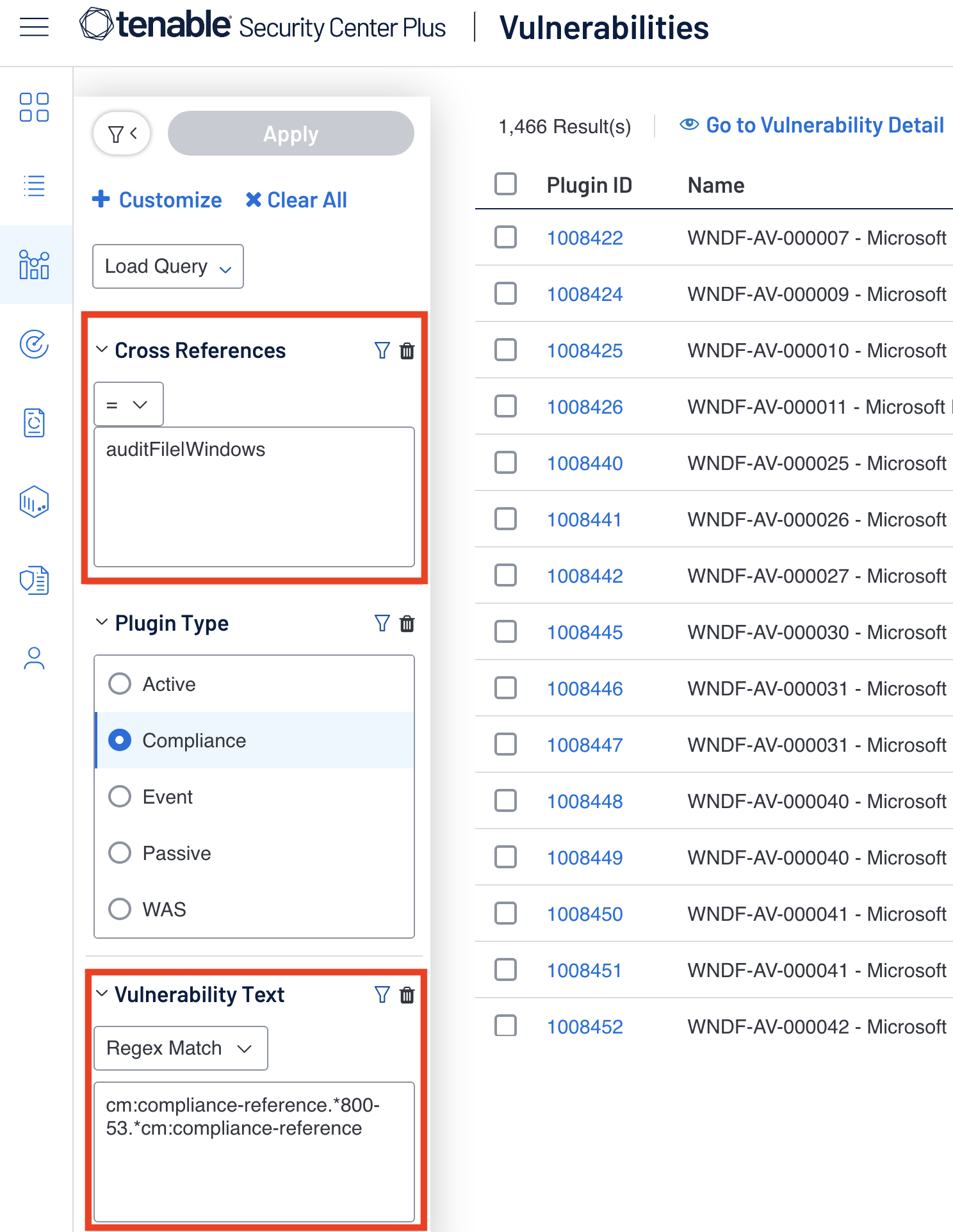
The Cross References Filter and the Vulnerability Text Filter.
Why the Cross References Filter for Windows audit files and not the framework? The Cross References filter is used for the ‘auditFile|Windows’ and a Regex Match paired with Vulnerability Text Filter to look for the tag ‘cm:compliance-reference.*800-53.*cm:compliance-reference.' This query grabs all the Benchmark results that use a Windows Audit file and are related to the framework 800-53. It is important to note that while we can do ‘auditFile|Windows’ in the Cross References Filter and cm:compliance-reference.*800-53.*cm:compliance-reference’ in the Vulnerability Text Filter, we cannot do the inverse; this would look like ‘800-53|*’ in the Cross References Filter and cm:compliance-reference.*auditFile|Windows.*cm:compliance-reference.' The latter query would not result in anything as the plugin text does not include the ‘auditFile’ tag and instead the tag is inside of the ‘xref’ tag within the scan. In the Tenable Security Center Compliance Elements section some of the most common compliance elements are listed for ease of use in any regex query.
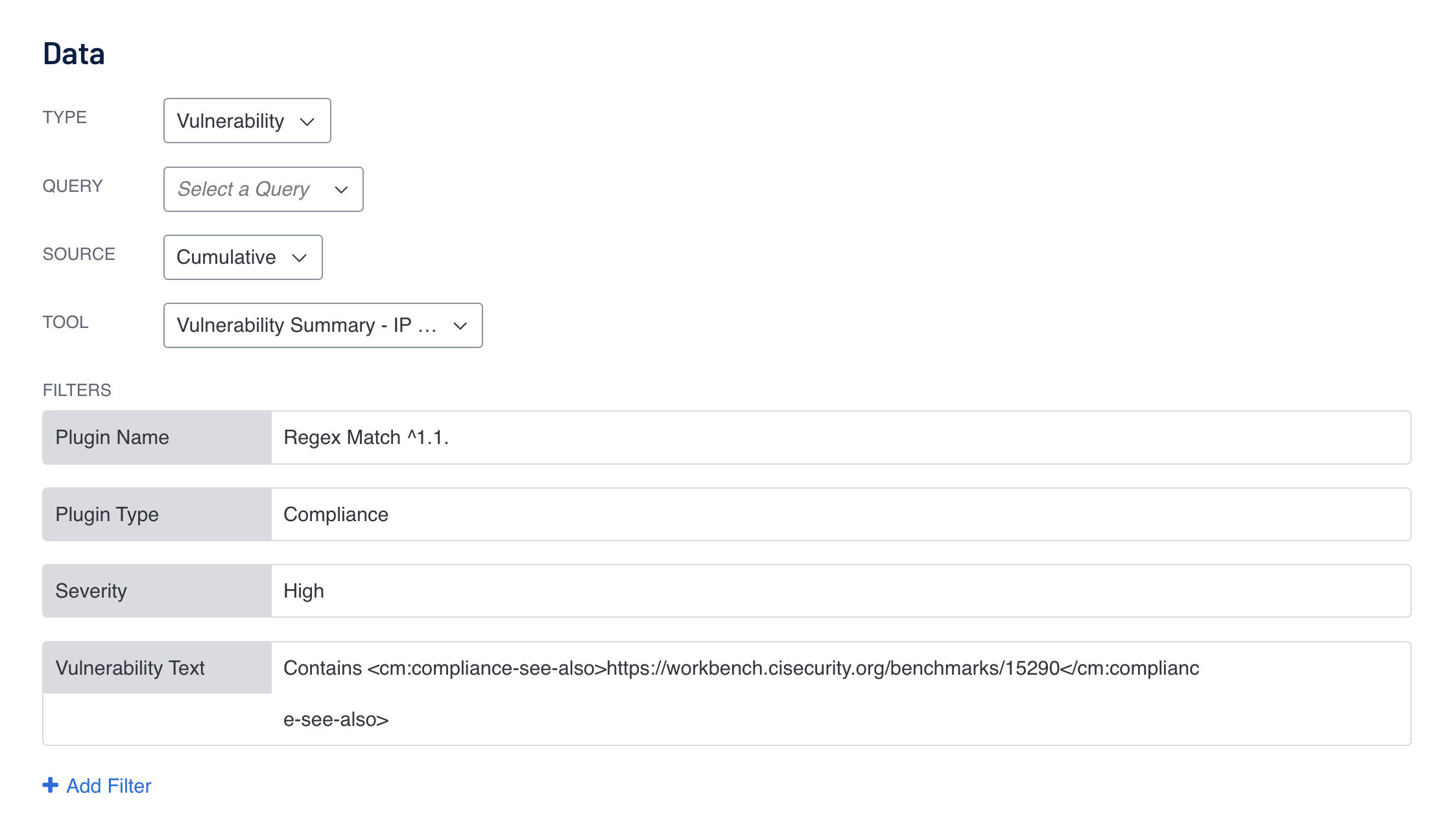
An example of a similar query is present in compliance reports and components. Inside the reports or components, the filters being used consistently are the Plugin Type and Vulnerability Text filters. In the following example, from the CIS Windows Server 2012 v3.0.0 Report template, shows a table which shows results that have names starting with 1.1 (Plugin Name with regex match of ^1.1) that are Compliance Plugin Type, have failed (Severity equal to ‘High’), and looks inside the vulnerability text to determine if the result originates from a CIS Windows Server 2012 v3.0.0 audit (the ‘see_also’ tag is a direct reference to the audit on CIS’ website.