Vendor-Based Audits
Apart from DISA and CIS benchmarks Tenable also offers the support of audits based on vendors. Some of the Vendor Based Audits tenable provides are: VMware, Juniper, IBM, Microsoft Security Compliance Toolkit (MSCT), and more. The creation of these audit files originates from these vendors create guides or best practices based on some of their products. This is evident when opening and looking at the first description lines of the audit files. For example, in the Juniper Hardening Junos Devices audit file the description reads:
# Description: This audit is based on the checklist for the book
# "This Week: Hardening Junos Devices, Second Edition"
# by John Weidley, available at http://www.juniper.net/dayone
The description mentions where the audit checks come from and if available =, the description also provides a link where the user can get more information on the topic.
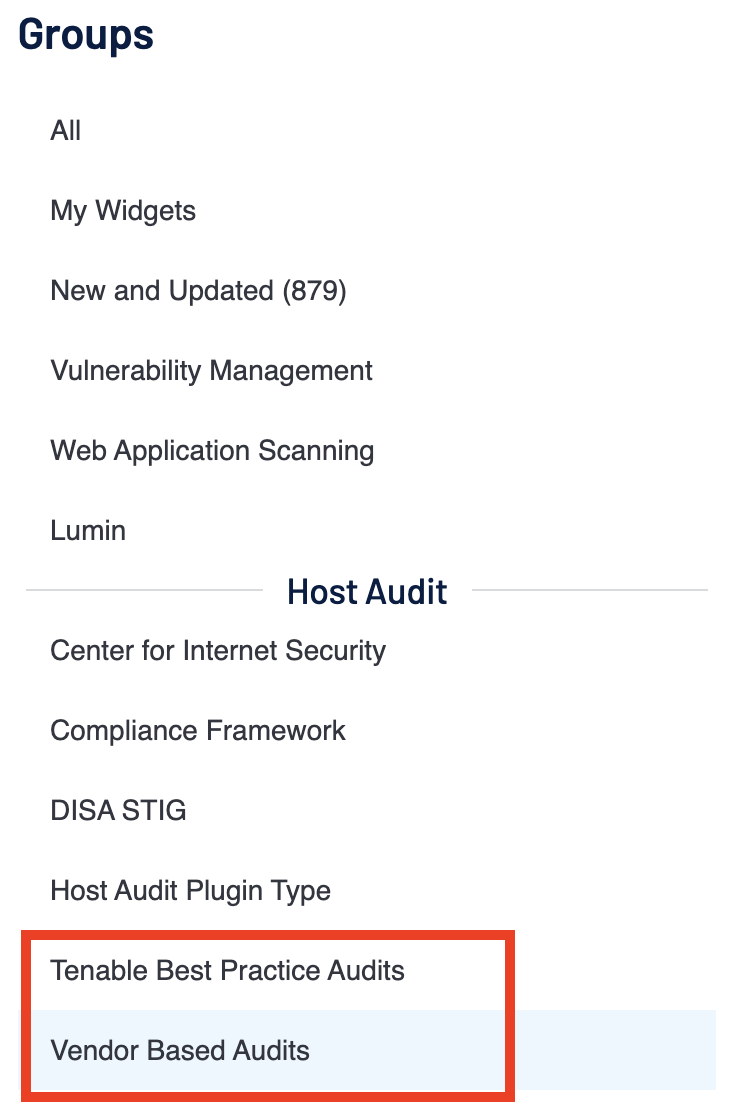
Tenable Vulnerability Management splits the Vendor-Based Audits into two sections in the Template Library.
Tenable Best Practice Audits include those benchmarks which were created by Tenable based on best practice guides of vendors. Within the Vendor-Based Audits section there are templates for benchmarks like the MSCT, which have been created based on baselines set by the vendor.
MSCT is a set of tools that allows enterprise security administrators to download, analyze, test, edit, and store Microsoft-recommended security configuration baselines for Windows and other Microsoft products. Tenable creates MSCT audit files that perform a detailed configuration review for these benchmarks. When scanning assets utilizing the appropriate MSCT audit file, the organization is able to perform detailed configuration checks. Tenable Vulnerability Management is able to perform a wide variety of platform and application audits based on the best practice consensus benchmarks developed by using these audit files. If more information is needed on auditing MSCT Baselines, this blog post provides more MSCT context.
In the other sections the Cross References and Vulnerability Text Filters have been mentioned and shown off to show how one could query their compliance data based on framework, plugin type, and frameworks like CIS or DISA; Vendor-Based Audit and Tenable Best Practice templates utilize the Compliance Benchmark Filter.
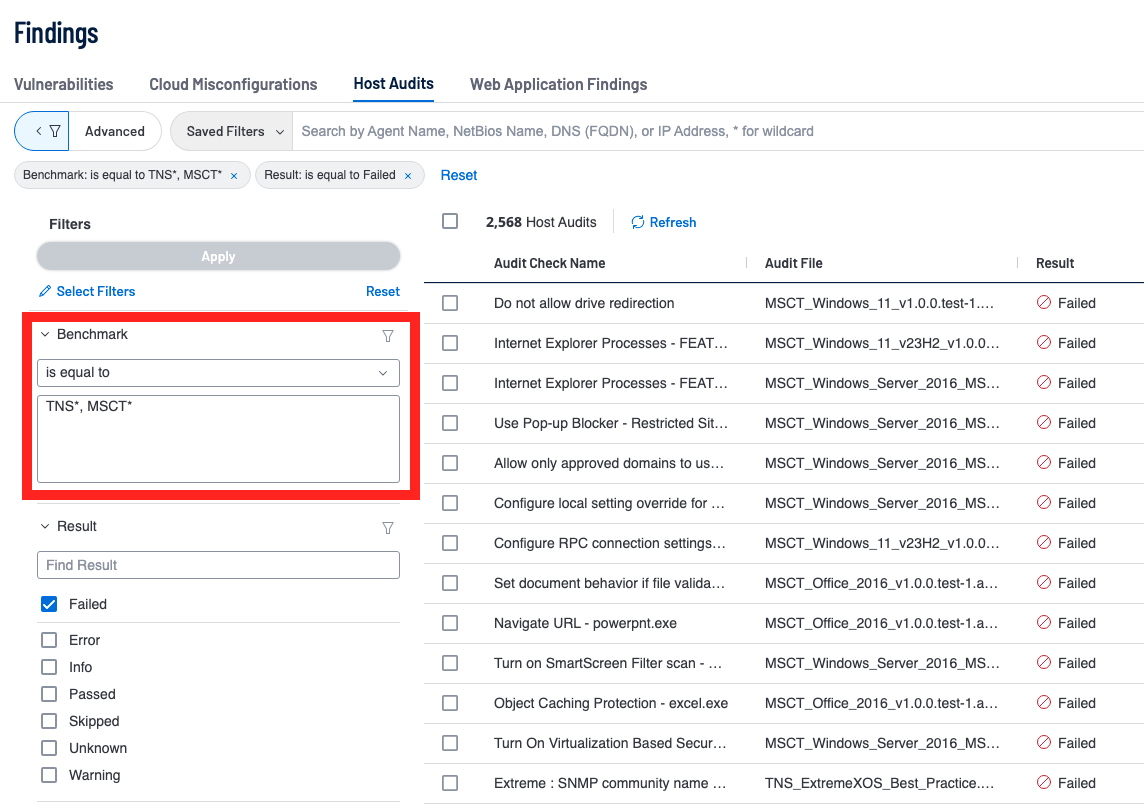
The benchmark filter within the Host Audits section of the Findings page can be used to find any benchmark by entering in the name, though the benchmark filter is also the best way to query all of Vendor Based Audits and/or Tenable Best Practice audits. The filter operator used in the screenshot above is equal too but the filter accepts an asterisk (*) to represent all characters after the given string. For example, “TNS*” would query every Benchmark with “TNS” in the start of the name. This behavior is the same as regular expression, though if you wanted to do multiple searches one would query something similar to the above (“TNS*, MSCT*). The search in the screenshot uses a comma to act as an OR within the query, this behavior results in all benchmarks matching the first value OR the other value coming up in one query search.
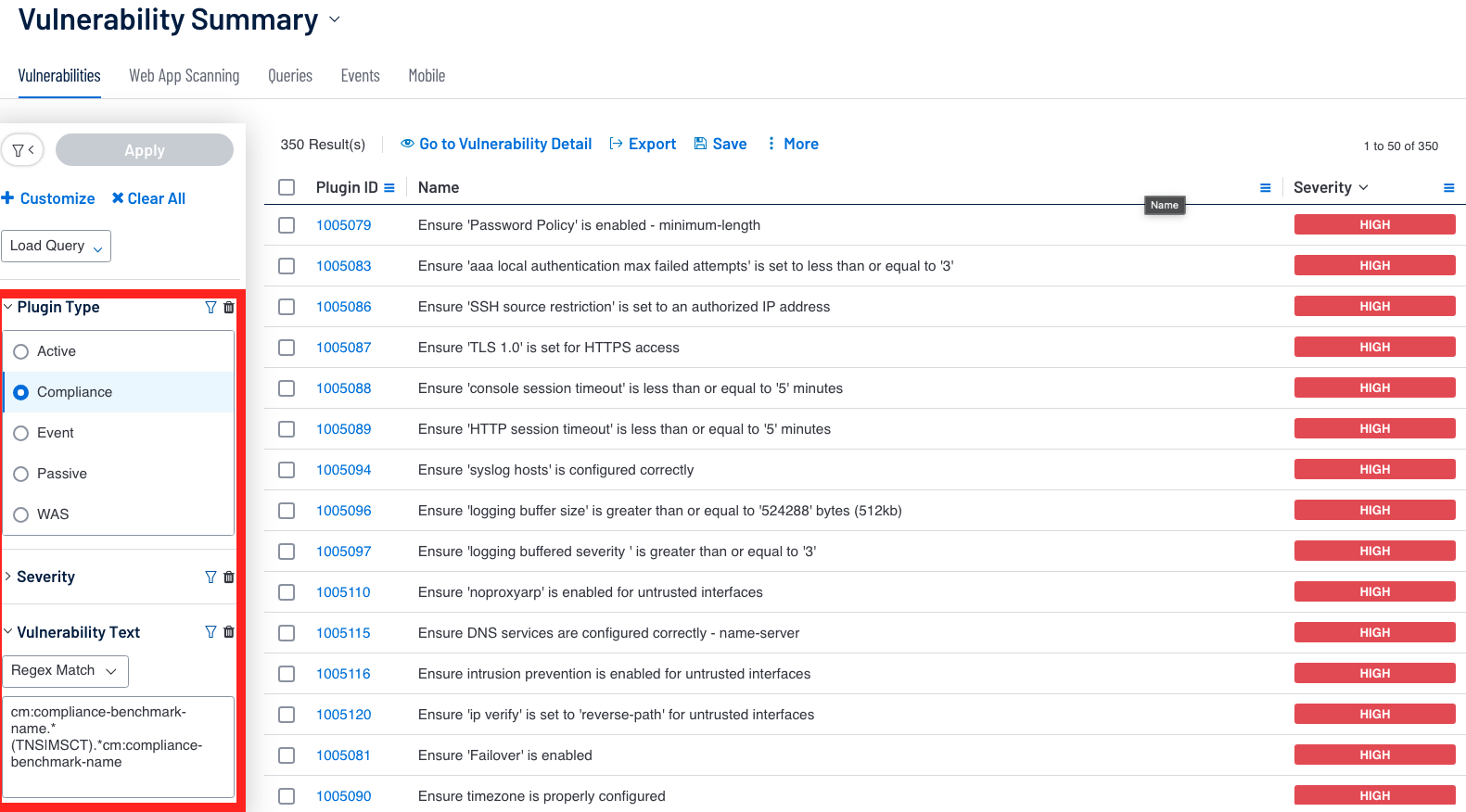
This query is also possible in Tenable Security Center by utilizing the Vulnerability Text Filter with a regular expression, as shown in the Vulnerability Summary Tool example.
In the example above we use a Regex Match with the Vulnerability Text Filter and set the text as cm:compliance-benchmark-name.*(TNS|MSCT).*cm:compliance-benchmark-name. The compliance benchmark name is what we target in the query to determine the name and filter out results. In the example above the text uses a pipe (|) as an OR operator to query any benchmark names with TNS OR MSCT in their name.