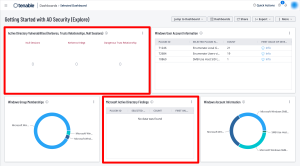
Active Directory Settings
The Getting Started with AD Security Tenable Vulnerability Management dashboard uses output derived from a set of plugins that are part of the Tenable Active Directory Starter Scan Template to help organizations determine the security posture of their Active Directory Servers using the following widgets:
Active Directory Vulnerabilities (Kerberos, Trusts Relationships, Null Sessions) – This widget uses plugins 150488, 150484, and 150486 to list a total count of findings for assets that were identified with the Active Directory vulnerabilities plugins directly related to Kerberos, Trusts Relationships, and Null Sessions.
Microsoft Active Directory Findings – This widget displays a vulnerability summary for assets that contain any vulnerabilities related to Active Directory. The application CPE filter is used to cross reference Tenable plugins that contain “active_directory”, including those from the AD Starter Scan.
These widgets leverage the following Tenable Nessus plugins:
-
150480 AD Starter Scan - Kerberoasting
-
150484 AD Starter Scan - Kerberos Krbtgt
-
150486 AD Starter Scan - Dangerous Trust Relationship
-
150481 AD Starter Scan - Weak Kerberos encryption
-
150488 AD Starter Scan - Null sessions
-
150489 AD Starter Scan - Blank passwords
-
150485 AD Starter Scan - Unconstrained delegation
-
150482 AD Starter Scan - Kerberos Pre-authentication Validation
-
150483 AD Starter Scan - Non-Expiring Account Password
-
150487 AD Starter Scan - Primary Group ID integrity
Domain Controllers
Organizations can leverage the following Nessus plugins in Tenable Vulnerability Management to identify security issues in Domain Controllers:
-
10413 - Microsoft Windows SMB Registry: Remote PDC/BDC Detection
Organizations can leverage the following Nessus plugins in Tenable Security Center to identify security issues in Domain Controllers:
-
44871 - WMI Windows Feature Enumeration With Vuln Text = Active Directory Domain Services
-
10456 - Microsoft Windows SMB Service Enumeration With Vuln Text = Active Directory Domain Services [ NTDS ]
-
44401 - Microsoft Windows SMB Service Config Enumeration With Vuln Text = Display name : Active Directory Domain Services
The following Indicators of Exposure (IoE) in Tenable Identity Exposure can be used to identify exposures in Domain Controllers:
-
Unsecured Configuration of Netlogon Protocol (Critical)
-
Domain Controllers Managed by Illegitimate Users (Critical)
-
Insufficient Hardening Against Ransomware (Medium)
-
Domain without Computer-Hardening GPOs (Medium)
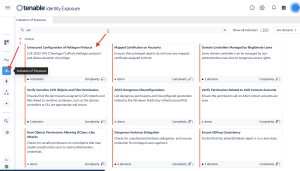
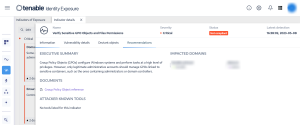
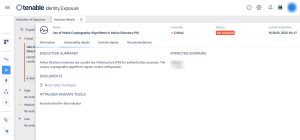
Step 1: From the Indicators of Exposure tab in Identity Management, search for the above listed IoEs in the search field as shown below:
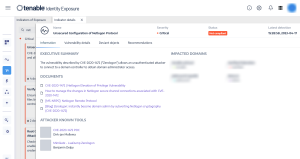
Step 2: Click on one of the displayed tiles to drill down into more details, as shown below:
Group and File Permissions
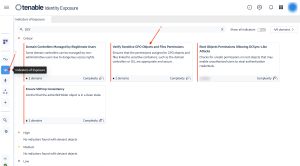
The following Indicators of Exposure (IoE) in Tenable Identity Exposure can be leveraged to determine exposures in group and file permissions:
-
Verify Sensitive GPO Objects and File Permissions (Critical)
-
User Primary Group (Critical)
-
Verify Permissions Related to AAD (Azure Active Directory) Connect Accounts (Critical)
-
Root Objects Permissions Allowing DCSync-Like Attacks (Critical)
-
Users Allowed to Join Computers to the Domain (Medium)
Step 1: From the Indicators of Exposure tab in Identity Management, search for the above listed IoEs in the search field as shown below:
Step 2: Click on one of the displayed tiles to drill down into more details, as shown below:
Cryptographic Controls
Applications and servers often support SSL/TLS key exchanges that are cryptographically weaker than recommended. Key exchanges must be recommended by IANA and provide at least 224 bits of security, which translates to a minimum key size of 2048 bits for Diffie Hellman and RSA key exchanges.Nessus has over 1000 plugins that identify vulnerabilities with SSH/OpenSSH, and other cipher suites.
Tenable Identity Exposure has the following Indicators of Exposure to evaluate cryptographic controls:
-
ADCS (Active Directory Certificate Services) Dangerous Misconfigurations (Critical)
-
Use of Weak Cryptography Algorithms into Active Directory PKI (Critical)
-
Reversible Passwords (Medium)
-
Vulnerable Credential Roaming Related Attributes (Low)
Step 1: From the Indicators of Exposure tab in Identity Management, search for the above listed IoEs in the search field as shown below:
Step 2: Click on one of the displayed tiles to drill down into more details, as shown below: