Compliance and Reporting
Compliance and reporting are two concepts within business and regulatory frameworks. Compliance refers to the rules, regulations, standards, and laws set forth by external entities, such as government agencies, industry associations, or internal policies. The NIS 2 Directive (Network and Information Systems Directive 2022/2555) is a legislative framework established by the EU to enhance the cybersecurity and resilience of network and information systems across critical sectors. The NIS 2 builds upon the initial NIS Directive, expanding its scope and requirements for organisations.
The following sections within the NIS 2 may be best suited to fall into the Compliance and Reporting category:
-
Article 21(2) (f): Policies and Procedures for Testing Cybersecurity Risk Management Measures: Policy Definition and Testing
Reporting is the process of documenting and communicating information related to compliance activities. This process involves the submission of accurate, timely, and comprehensive reports to relevant stakeholders. Together compliance and reporting help organisations maintain trust, manage risks, and uphold legal responsibilities.
The NIS 2 Directive imposes specific compliance requirements on in-scope essential and important entities. These requirements are designed to enhance cybersecurity and ensure the resilience of digital and physical assets involved in delivering essential or important services in the European Union. The key compliance requirements include:
Cybersecurity Risk Management Measures: In-scope entities are required to implement ten key measures to manage and mitigate cyber risks effectively. These measures encompass various aspects of cybersecurity risk management, including:
-
Policies on risk analysis and information system security.
-
Incident handling, covering prevention, detection, and response to incidents.
-
Crisis management and business continuity, including backup and recovery management.
-
Supply chain security, addressing relationships with suppliers and service providers.
-
Security in network and information systems acquisition, development, and maintenance, with a focus on vulnerability handling and disclosures.
-
Policies and procedures to assess the effectiveness of cybersecurity risk management.
-
Basic cyber hygiene practices and cybersecurity training.
-
Policies and procedures regarding the use of cryptography and, where appropriate, encryption.
-
Human resources security, access control policies, and asset management.
-
The use of multi-factor authentication or continuous authentication solutions, secured voice, video, and text communications, and secured emergency communication systems.
The penalties for noncompliance with the NIS 2 Directive can be substantial and vary depending on the classification of the entity falling within its scope. The directive prescribes specific penalties for essential and important entities as follows:
-
For Essential Entities: Noncompliance with the NIS 2 Directive by essential entities can result in fines of up to €10,000,000 or at least 2% of the total annual worldwide turnover of the company to which the entity belongs, whichever amount is higher.
-
For Important Entities: Important entities that fail to comply with the NIS 2 Directive may face fines of up to €7,000,000 or at least 1.4% of the total annual worldwide turnover of the company to which the entity belongs, whichever amount is higher.
These penalties are designed to encourage organisations to take cybersecurity and incident reporting seriously, as well as to ensure the security and resilience of essential and important services within the European Union. Noncompliance can have significant financial repercussions for organisations. This makes adhering to NIS 2 compliance requirements and deadlines crucial.
Tenable solutions include reporting features that help organisations demonstrate compliance with a number of cybersecurity regulations. This can be valuable for NIS 2 compliance, as organisations are required to report incidents and maintain proper documentation. Risk management measures can be validated with compliance scanning, providing detailed reports on applications and assets within the organisation.
Tenable has introduced key features and content that give you visualisation of Compliance scan results through the built-in dashboards or custom dashboards using the newly added widgets. Performing a compliance audit scan is not the same as performing a vulnerability scan, although there can be some overlap. A compliance audit determines if a system is configured in accordance with an established policy. A vulnerability scan determines if the system is open to known vulnerabilities. Organisations can deploy and customise audit files to meet their local security policy. Once the audit file is customised, the file can be used with Tenable products to manage and automate the configuration compliance process. Detailed or summarised reports can also be generated in PDF format for the host audit findings. Dashboards and reports exist for a wide variety of existing compliance standards such as:
-
GDPR
-
HIPAA
-
PCI-DSSv4.0
-
ISO/IEC-27001
-
NIST 800-53
-
ITSG-33 (Canada)
-
DISA STIG
-
Center for Internet Security
-
Tenable Best Practice Audits
-
Vendor-Based Audits
Detailed information on all the available Compliance dashboards can be found online by referencing these locations for Tenable Security Center and Tenable Vulnerability Management. For each select the Compliance and Configuration Assessment Category to list the available content and references.
Additional details on Compliance scanning can be found within the Host Audit Data Audit Overview Cyber Exposure Study located here.
Cloud services are an integral part of business operations, offering scalability, flexibility, and accessibility. Cloud environments store vast amounts of sensitive data, including personal information, financial records, intellectual property, and proprietary business data. Ensuring robust security measures protects this information from unauthorised access, breaches, or theft.
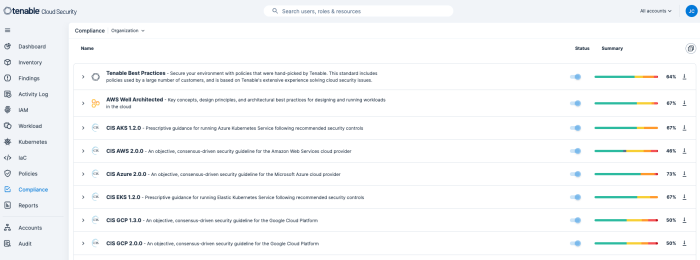
Protecting cloud environments is vital for protecting data, ensuring compliance with regulatory requirements, maintaining operational continuity, managing risks, and optimising business efficiency. Tenable Cloud Security provides out-of-the-box, continuously updated support for all major compliance frameworks, and best practices. Tenable Cloud Security provides the ability to create customised frameworks to meet the exact needs of your organisation. Using customised reports, communicate with stakeholders on internal compliance, external audit and daily security activities.
Compliance reporting is available by navigating to the Compliance tab. On the Compliance dashboard, analysts have the option to select the appropriate compliance benchmark from the list. By default, this dashboard reports compliance details for all Benchmarks combined if no option is selected.
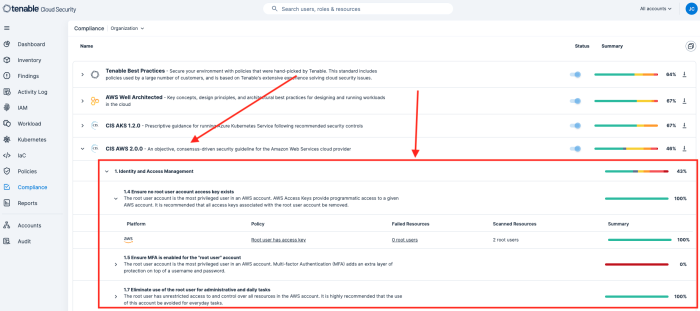
To view details, analysts can drill down into any of the findings. In this example, drilling down into the CIS AWS 2.0.0 item provides details on the root account.
The following cross-reference information is provided to derive a more comprehensive and effective approach to managing information security requirements. NIS 2 Article 21(2) (f) references risk management measures.
Security domains define how information is classified, categorised, or administered. The following Security Domains, Sub-Domains, and Measures are related to NIS 2 Article 21(2) (f), and can assist organisations already using other standards and frameworks to comply with NIS 2.
SECURITY DOMAIN: Defence.
SECURITY SUB-DOMAIN: Computer Security Incident Management.
SECURITY MEASURE: Information system security incident response.
In an effort to foster higher consistency and reliability across multiple frameworks and the NIS 2, Article 21(2) (f) can be associated with the ISO 27001, NIST CSF, and ISA/IEC 62443 utilising the following cross-references for vulnerability handling and disclosure. The following cross-references cover the processes and procedures related to risk management.
CROSS REFERENCES:
The ISO 27001 references sections within Annex A, Information Security Controls Reference, specifically the following sections:
-
ISO 27001(A.16.1.1, A.16.1.4, A.16.1.5, A.16.1.6, A.16.1.7)
The NIST CSF references the following sections within Identify, and Protect.
-
NIST CSF (ID.AM -5, ID.RM-2, 3, PR.IP -7,8, PR.DS -4, ID.BE -5)
The ISA/IEC 62443 references the following sections within System Integrity and Data Confidentiality.
-
ISA/IEC 62443 (SR 3.4, SR 4.1)