Detecting Running Services
Tenable Vulnerability Management and Tenable Security Center include plugins that detect running services and process information. The information from these plugins can display unregistered software that may be running on the system that is not shown in the registry. The plugins below provide visibility into services that may appear only in running processes rather than in installed software packages. The plugins below provide this valuable information.
- 58452 - Microsoft Windows Startup Software Enumeration
- 70329 - Microsoft Windows Process Information
- 70330 - Microsoft Windows Process Unique Process Name
- 70331 - Microsoft Windows Process Module Information
- 70767 - Reputation of Windows Executables: Known Process(es)
- 70768 - Reputation of Windows Executables: Unknown Process(es)
- 70943 - Reputation of Windows Executables: Never seen process(es)
- 110483 - Unix/Linux Running Processes Information
A filter can also be applied using Plugin Family: Service Detection.
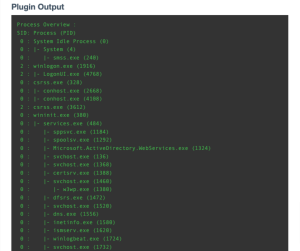
The following displays sample output for plugin 70329 that shows a “w3wp” process that could be suspicious. Output such as this can be taken from this plugin and used in a further investigative search using the text with the Plugin Output (Vulnerability Text) or CPE filter.
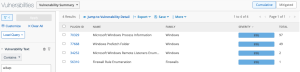
The search can be pivoted from Plugin ID to Vulnerability Text. The following image displays all other scan results that contain w3wp in the plugin output (vulnerability text). This information can now be investigated using the Vulnerability Detail List tool or the Vulnerability List tool in the drop-down menu above the results.