Verifying Patches
The information that Tenable plugins provide to enumerate software versions can be used to verify that authorized software is updated with the latest patches. The Patch Report (66334) Plugin summarizes a list of patches that need to be installed and enabled on an asset. Use this plugin to track how often a patch assessment is made over time or to extract the data to perform analysis.
The following image is the plugin output from plugin 66334 for a Windows asset:
The following image is the plugin output from plugin 66334 for a Mac OS Asset:
The following image is the plugin output from plugin 66334 for Linux Asset:
Following are some suggested filters to find these instances of patches that are not fully enabled. Note that Plugin Output in Tenable Vulnerability Management is Vulnerability Text in Tenable Security Center.
- SCCM or WSUS report that patch has been applied
- Plugin Output contains SCCM: NOT Vulnerable
- Plugin Output contains SCCM: NOT Vulnerable
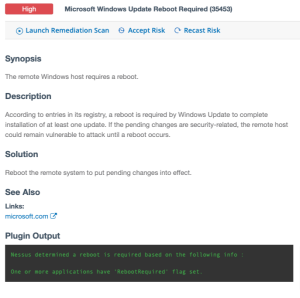
- Reboot required
- Plugin ID equals 35453
- Severity equals High
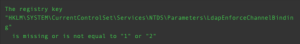
- Registry change required (Tenable Vulnerability Management)
- Severity equals Medium, High, Critical
- Plugin Output contains HKLM
- Plugin Output contains registry
- Registry change required (Tenable Security Center)
- Severity equals Low, Medium, High, Critical
- Only required in Tenable Security Center: Plugin Type equals Active
- Vulnerability Text Regex Match HKLM|HKU|HKCU|Registry