Search Overview
When scanning for assets to track compliance efforts, Tenable Audit files are used to instruct the scan of specific configuration, file permission, and access control tests to be performed. Knowing the source is important before looking at the audit results. Being familiar with the file structure, key data fields, and how the fields translate into filters in Tenable Vulnerability Management and Tenable Security Center can assist the user in fine-tuning their focus, and query the results that are needed from the audit scan.
Audit Files:
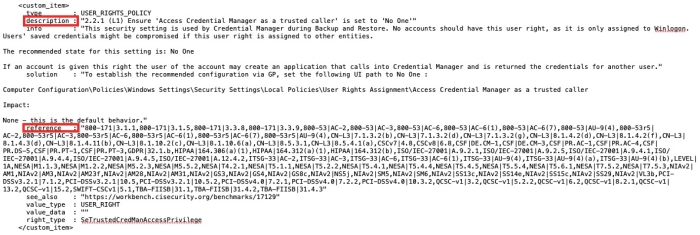
Audit files that can be used in the scans are formatted like an XML. This formatting allows the file to be pretty readable and provides the ability to grep through the audit file to identify key fields that will help determine what the benchmark or specific test is about. Within the audit files there are many elements called <item> or <custom_item>. These items delineate the various checks or tests involved in the audit benchmark. Within these “items” there are two main elements that should be a focus: “description” and “reference."
The “description” field within the “items" element is the name of the actual audit check that will be performed. Within Tenable Vulnerability Management these checks can be searched using the filter “Audit Check Name”, and within Tenable Security Center the description field becomes the plugin name: therefore, the plugin name filter would be used.
The “reference” field is the next important field that is used for compliance-based analysis. The reference field is used to map a variety of compliance frameworks and the associated control identifiers to a specific audit check. After the audit file has been used in a scan, the reference field in the audit file can be searched for in Tenable Vulnerability Management by using the Compliance Framework Filter and the Compliance Control Filter, while in Tenable Security Center the user would need to use the Cross Reference filter.
This study takes a closer look at searching for compliance goals by querying audit checks and cross-references using Tenable Vulnerability Management and Tenable Security Center. Before querying the results in Tenable Vulnerability Management or Tenable Security Center the user may be wondering what the audit file tests or what the audit file attempts to achieve. A user is able to search through the audit files used in the scans to find reference information, or even audit check names, for the related audit checks.
In macOS and Linux systems a simple “grep” command can be used to quickly identify which audit checks may be of interest.
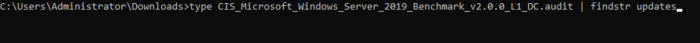
In Windows, a user can use the “type” command along with the “findstr” in the command prompt to look through audit files and find desired audit checks.
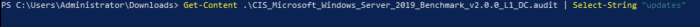
This search is also possible in powershell. One quick way is using the “Get-Content” and “Select-String” commands.
For a more detailed breakdown of the structure of audit files go to refer to the Host Audit Data cyber exposure study.