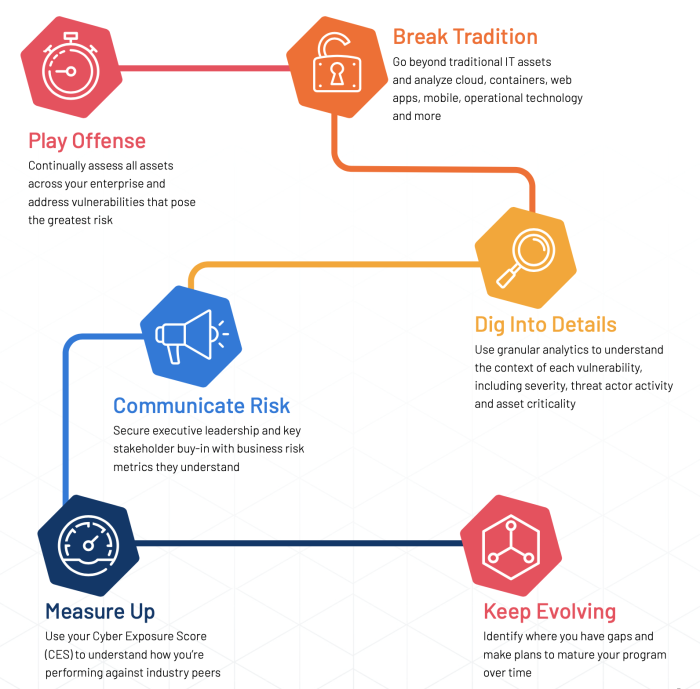
In Closing
Now that you’ve completed measuring your mitigation strategy against the organization's SLAs, you’re able to determine the effectiveness of the organization's risk-based vulnerability management program, including what’s working well and where there are areas for improvement. This is called Continuous Improvement. This knowledge helps you communicate the value of your security program to senior management and other key stakeholders so you can effectively build their confidence in your capabilities, request additional resources, and manage expectations when high-profile cyber attacks draw media attention.
With a specific, quantifiable understanding of how the RBVM program has performed, you’ll also know exactly what adjustments to make in order to optimize your team’s effectiveness and efficiency as you continue to evolve your VM practices to align with a risk-based strategy.
Compliance References
CSF v1.1 References
NIST Special Publication 800-53 Revision 5
NIST Special Publication 800-53 Revision 4
NIST Special Publication 800-171 Revision 2