Syslog and Email Alert Details
When you enable Syslog or email alerts, Tenable Identity Exposure sends out notifications when it detects a deviance, an attack, or a change.
Alert Header
Syslog alert headers (RFC-3164) use the Common Event Format (CEF), a common format in solutions that integrate Security Information and Event Management (SIEM).
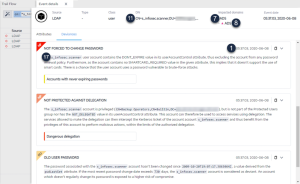
Example of an alert for an Indicator of Exposure (IoE)
IoE Alert Header
<116>Jan 9 09:24:42 qradar.alsid.app AlsidForAD[4]: "0" "1" "Alsid Forest" "emea.corp" "C-PASSWORD-DONT-EXPIRE" "medium" "CN=Gustavo Fring,OU=Los_Pollos_Hermanos,OU=Emea,DC=emea,DC=corp" "28" "1" "R-DONT-EXPIRE-SET" "2434" "TrusteeCn"="Gustavo Fring"Example of an alert for an Indicator of Attack (IoA)
IoA Alert Header
<116>Jan 9 09:24:42 qradar.alsid.app AlsidForAD[4]: "2" "1337" "Alsid Forest" "emea.corp" "DC Sync" "medium" "yoda.alsid.corp" "10.0.0.1" "antoinex1x.alsid.corp" "10.1.0.1" "user"="Gustavo Fring" "dc_name"="MyDC"Alert Information
Generic Elements
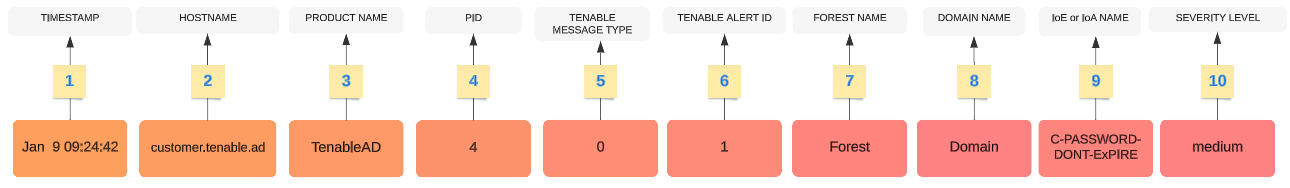
The header structure includes the following parts, as described in the table.
| Part | Description |
|---|---|
| 1 |
Time Stamp— The date of the detection. Example: "Jun 7 05:37:03" |
| 2 |
Hostname — The hostname of your application. Example: "customer.tenable.ad" |
| 3 |
Product Name — The name of the product that triggered the deviance. Example: "TenableAD", "AnotherTenableADProduct" |
| 4 |
PID — The product (Tenable Identity Exposure) ID. Example: [4] |
| 5 |
Tenable Msg Type — The identifier of event sources. Example: "0" (= On each deviance), "1" (= On changes), "2" (= On each attack) |
| 6 |
Tenable Alert ID — The unique ID of the alert. Example: "0", "132" |
| 7 |
Forest Name — The forest name of the related event. Example: "Corp Forest" |
| 8 |
Domain Name — The domain name related to the event. Example: "tenable.corp", "zwx.com" |
| 9 |
Tenable Codename — The code name of the Indicator of Exposure (IoE) or Indicator of Attack (IoA). Examples: "C-PASSWORD-DONT-EXPIRE", "DC Sync". |
| 10 |
Tenable Severity Level — The severity level of the related deviance. Example: "critical", "high", "medium" |
IoE Specific Elements
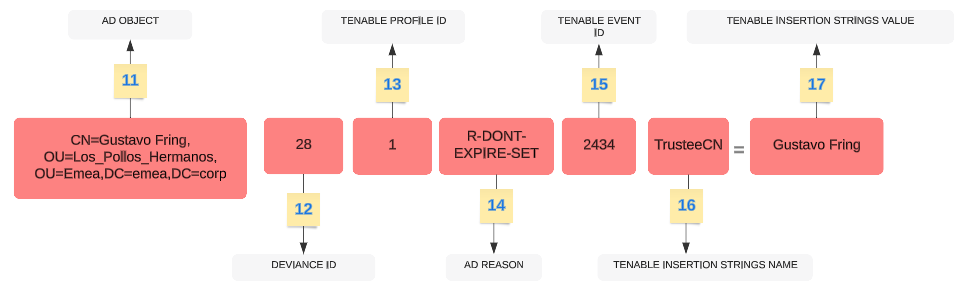
| Part | Description |
|---|---|
| 11 |
AD Object — The Distinguished Name of the deviant object. Example: "CN=s_infosec.scanner,OU=ADManagers,DC=domain,DC=local" |
| 12 |
Tenable Deviance ID — The ID of the deviance. Example: "24980", "132", "28" |
| 13 |
Tenable Profile ID — The ID of the profile on which Tenable Identity Exposure triggered the deviance. Example: "1" (Tenable), "2" (sec_team) |
| 14 |
AD Reason Codename — The code name of the deviance reason. Example: "R-DONT-EXPIRE-SET", "R-UNCONST-DELEG" |
| 15 |
Tenable Event ID — The ID of the event that the deviance triggered. Example: "40667", "28" |
| 16 |
Tenable Insertion Strings Name — The attribute name that the deviant object triggered. Example: "Cn", "useraccountcontrol", "member", "pwdlastset" |
| 17 |
Tenable Insertion Strings Value — The value of the attribute that the deviant object triggered. Example: "s_infosec.scanner", "CN=Backup Operators,CN=Builtin,DC=domain,DC=local" |
IoA Specific Elements
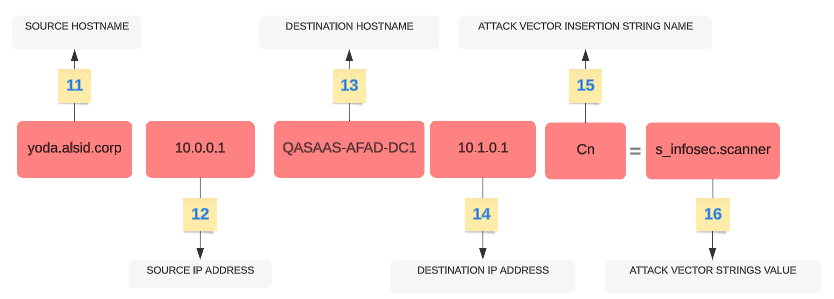
| Part | Description |
|---|---|
| 11 |
Source hostname — The hostname of the attacking host. Value can also be "Unknown". |
| 12 |
Source IP Address — The IP address of the attacking host. Values can be IPv4 or IPv6. |
| 13 |
Destination Hostname — The hostname of the attacked host. |
| 14 |
Destination IP Address — The IP address of the attacked host. Values can be IPv4 or IPv6. |
| 15 |
Attack Vector Insertion Strings Name — The attribute name that the deviant object triggered. |
| 16 |
Attack Vector Insertion Strings Value — The value of the attribute that the deviant object triggered. |
Examples
This example shows the source for the event (5). You set this parameter in the Syslog configuration page. For more information, see Syslog Alerts.