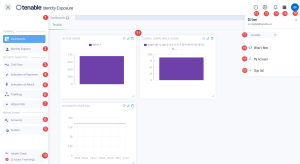
Navigate Tenable Identity Exposure
After you log in to Tenable Identity Exposure, the home page opens, as shown in this example.
To expand or collapse the side navigation bar:
-
To expand: click the
 menu at the top left of the window.
menu at the top left of the window. -
To collapse: click the X at the top left of the window.
| # | What it is | What it does |
|---|---|---|
| 1 | Dashboards | Dashboards allow you to manage and monitor efficiently and in a visual way security in an Active Directory infrastructure. |
| 2 | Identity Explorer | Tenable Identity Exposure's Identity Explorer view unifies identities across both Active Directory and Microsoft Entra ID. This view shows the Identity Risk Score (beta) for each listed asset and the potential reach of compromised identities. |
| 3 | Trail Flow | The Trail Flow shows the real-time monitoring and analysis of events affecting your Active Directory. |
| 4 | Indicators of Exposure | Tenable Identity Exposure uses Indicators of Exposure (IoEs) to measure the security maturity of your Active Directory and assign severity levels (Critical, High, Medium, or Low) to the flow of events that it monitors and analyzes. |
| 5 | Indicators of Attack | Through Indicators of Attack, Tenable Identity Exposure can detect attacks in real time. |
| 6 | Topology | The Topology page gives an interactive graph visualization of your Active Directory. It shows the forests, domains, and trust relationships that exist between them. |
| 7 | Attack Path |
The Attack Path pages give graphical representations of Active Directory relationships:
|
| 8, 9 |
Management Required User Role: Organizational User with appropriate permissions.
|
This section allows you to configure the following:
For more information, see the Tenable Identity Exposure Administrator Guide. |
| 10 | Health Checks | Health checks provide you with real-time visibility into the configuration of your domains and service accounts in one consolidated view from which you can drill down for more detailed information. |
| 11 | Widgets | Widgets are customizable datasets on a dashboard. They can contain bar charts, line charts, and counters. |
| 12 | Product Updates | Information about the latest product features. |
| 13 | Settings | Access to system configuration, forest and domain management, license, user and role management, profiles, and activity logs. |
| 14 | Notifications (Bell) | A bell icon and badge counts notify you of attack alerts and/or exposure alerts waiting for your acknowledgment. |
| 15 | Application Switcher | Click this icon to switch between applications from the Tenable workspace. |
| 16, 19 | User profile icon (User Preferences) | Click this icon to access a submenu to security profiles, release notes, activity logs, preferences, or sign out. |
| 17 | Security Profiles | Security Profiles allow different types of users to review security analysis from different reporting angles. |
| 18 | What's New | Click to open the release notes for the most recent version of Tenable Identity Exposure. |
| 20 | Sign out | Click to sign out of Tenable Identity Exposure. |