Configuring Okta as an Identity Provider
In addition to supporting Active Directory, Tenable Identity Exposure now integrates with Okta as an Identity Provider (IdP), extending visibility into modern, cloud-based identity platforms. This integration introduces new Indicators of Exposure tailored to Okta-specific risks.
This guide provides step-by-step instructions to connect your Okta environment with Tenable Identity Exposure. By enabling this integration, Tenable can collect identity-related metadata from Okta, helping you uncover potential vulnerabilities and strengthen your overall identity security posture.
To integrate Okta with Tenable Identity Exposure, follow closely this on-boarding process:
You must have a Tenable Cloud account to log in to “cloud.tenable.com” and use the Okta support feature.
This Tenable Cloud account is the same email address used for your Welcome email. If you do not know your email address for "cloud.tenable.com," please contact Support.
All customers with a valid license (On-Premises or SaaS) can access the Tenable Cloud at “cloud.tenable.com”. This account allows you to configure Tenable scans for your Okta and collect the scan results.
License Count
Tenable does not count duplicate identities against the license only when the Tenable Cloud sync feature is enabled. Without this feature, it cannot match accounts from Okta and Active Directory, causing it to count each account separately.
-
Without Tenable Cloud sync: A single user with both an AD account and an Okta account count as two separate users against the license.
-
With Tenable Cloud sync enabled: The system consolidates multiple accounts into a single identity, ensuring that a user with multiple accounts is counted only once.
Note: Okta is a third-party service, and its interface or configuration process may change over time. For the most accurate and up-to-date instructions, always refer to Okta’s official documentation.
Use the following procedures (adapted from the Okta documentation) to configure all required settings in Okta.
-
 Add an API token
Add an API token
-
Log in to Okta with an "Admin" account.
-
Navigate to the Admin Console.
-
Navigate to Security/API.
-
Click on the Tokens tab -> Create Token (e.g. https://youroktaorg.okta.com/admin/access/api/tokens).
-
Name your token – Enter a descriptive name to help you identify the purpose of this token later.
-
Define token usage restrictions – Specify the IP ranges or locations from which API calls using this token are allowed.
-
Click Create Token – This generates a new API token.
A message confirms that the "Token created successfully" appears.
-
Copy the token and securely store the token value, as it will only be shown once. You’ll need it later when configuring Tenable Identity Exposure.
-
Verify the token – The newly created token should now be listed on your Tokens page.
-
-
 Create credentials
Create credentials
-
After you configure all the required settings in Okta: In Tenable Vulnerability Management, create a new credential of type "Okta Cloud Identity."
-
Select the "Key" authentication method.
-
Type a name and description in the required boxes.
-
Under Settings, type your organization URL and the token value that you retrieved from the previous procedure.
-
-
To use Okta, you must activate the feature in Tenable Identity Exposure settings.
-
See Identity 360, Exposure Center, Okta, and Microsoft Entra ID Support Activation for instructions.
Adding a tenant links Tenable Identity Exposure with the Okta tenant to perform scans on that tenant.
-
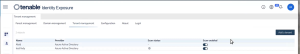
In the Configuration page, click on the Identity Providers tab.
The Tenant Management page opens.
-
Click on Add a tenant.
The Add a tenant page opens.
-
In the Provider drop-down list box, select Okta.
-
In the Name of the tenant box, type a name.
-
In the Credentials box, click the drop-down list to select a credential.
-
If your credential does not appear in the list, you can either:
-
Create one in Tenable Vulnerability Management (Tenable Vulnerability Management > Settings > Credentials). For more information, see the procedure to create an Azure-type credential in Tenable Vulnerability Management.
-
Check that you have the "Can use" or "Can edit" permission for the credential in Tenable Vulnerability Management. Unless you have these permissions, Tenable Identity Exposure does not show the credential in the drop-down list.
-
-
Click Refresh to update the drop-down list of credentials.
-
Select the credential you created.
-
Click Add.
A message confirms that Tenable Identity Exposure added the tenant, which now appears in the list on the Tenant Management page.
Note: Tenant scans do not occur in real time and require at least one hour. Okta data is visible in the Identity Explorer, depending on the tenant size.
-
Select a tenant on the list and click the toggle to Scan enabled.
Tenable Identity Exposure requests a scan on the tenant and the results appear in the Indicator of Exposure page.
Note: The mandatory minimum time delay between two scans is 30 minutes and occurs at least once per day. Depending on the tenant size, most customers' data refresh multiple times per day.
Troubleshoot the configuration
-
After configuration, check the scan status of the Okta Identity Provider in the Tenable Identity Exposure > Identity Providers section.The status should display green
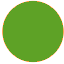 a few minutes after a successful scan.
a few minutes after a successful scan.
-
Additionally, you can verify that Okta resources (users, roles, apps, groups.) begin to appear across the various Tenable Identity Exposure screens.
-
If the status remains red or no data is ingested:
-
Double-check the credentials (Org URL / Token).
-
Review scope permissions.
-
Confirm network access and API rate limits on the Okta side.
-
-
Double-check your configuration values. Typos in the domain or token are common mistakes. You can find the correct values in your Okta Developer Console.