Activity Logs
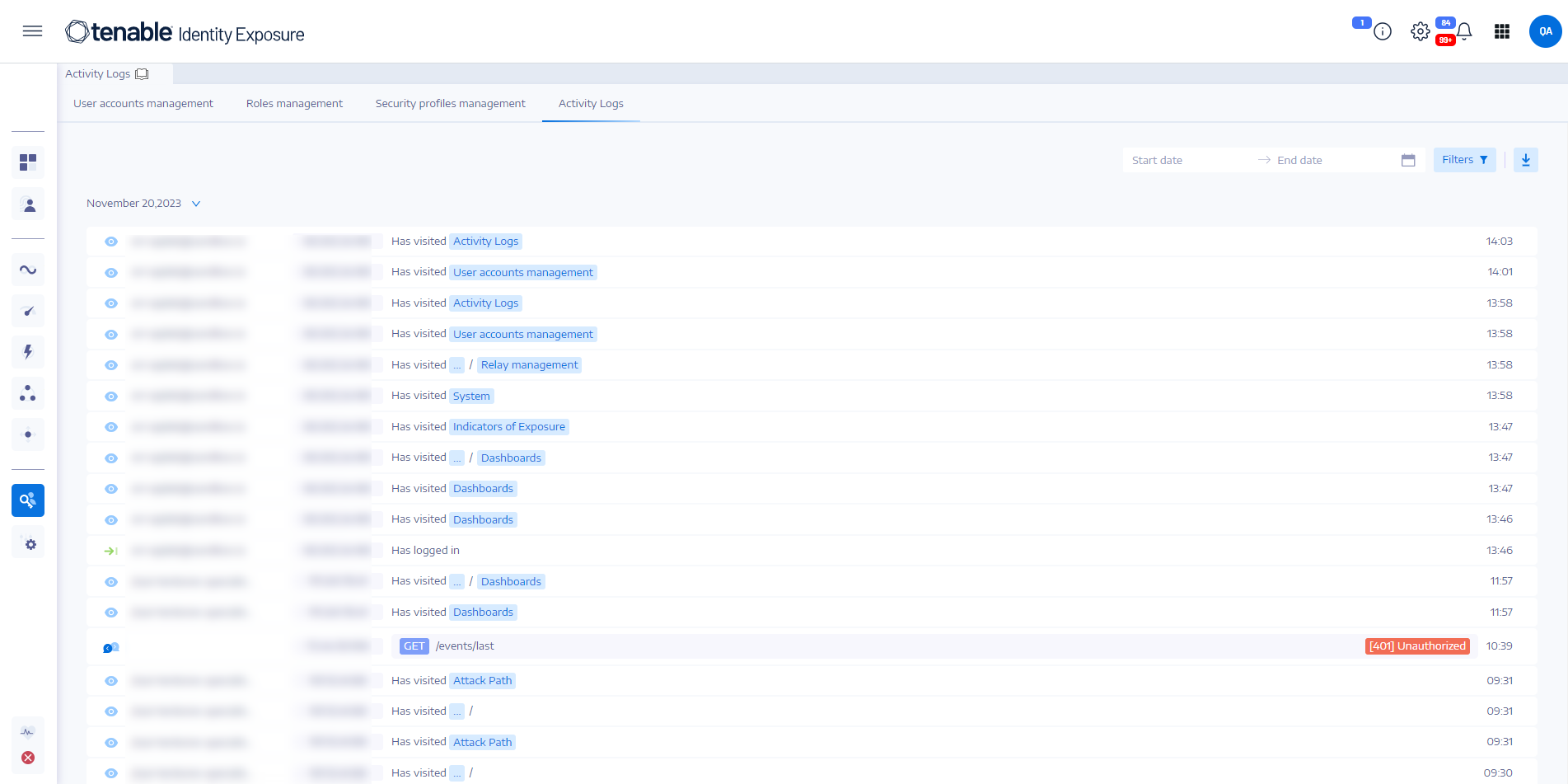
The activity logs in Tenable Identity Exposure allow you to view the traces of all activities that occurred on the Tenable Identity Exposure platform related to specific IP addresses, users, or actions.
To view the activity logs:
-
In Tenable Identity Exposure, click on the Accounts
 icon in the left navigation menu.
icon in the left navigation menu.The User account management pane appears.
-
Select the Activity Logs tab.
The Activity Logs pane opens.
To display activity logs for a specific time frame:
-
At the top of the activity log pane, click on the date picker.
-
Select a start date and an end date for the period that you want.
-
(Optional) Use the scroll bar to select the time (default: current time)
-
Click OK.
Tenable Identity Exposure shows the activity log for that time period.
To filter activity logs:
-
At the top of the activity log pane, click the
 button.
button.The Filters pane appears.
-
Click > in the following boxes:
-
IP Address
-
User
-
Action
-
-
Click Validate.
Tenable Identity Exposure shows the activity log for the filter you defined.
To clear filters:
-
At the bottom of the Filters pane, click Erase filters.
Tenable Identity Exposure shows the unfiltered activity log.
To export the activity logs:
-
At the top of the activity log pane, click the
 icon.
icon.Tenable Identity Exposure downloads the activity log in CSV format to your computer.
SAML Authentication and Impersonation Entries
Because Tenable Identity Exposure uses SAML authentication to connect with Tenable Cloud, actions performed by Tenable Identity Exposure are logged as impersonation events.
Each request that Tenable Identity Exposure sends to Tenable Cloud appears in the Activity Logs as if it were performed by the service account established for the SAML connection.
In these entries:
-
Actor – the Tenable Cloud account used to log into Tenable Identity Exposure through the target account
-
Target – shows the account associated with the SAML redirection
As a result, the Activity Logs may display a large number of impersonation events. This behavior is expected and reflects how the SAML integration manages authentication, not an issue with account security.