AdminCount Attribute Set on Standard Users
The adminCount attribute on a user account indicates its past membership in an administrative group and does not get reset when the account leaves the group. As a result, even old administrative accounts have this attribute, which blocks the inheritance of Active Directory permissions. While originally intended to protect administrators, it can create challenging permission issues.
This medium-level IoE only reports on active user accounts and groups with this attribute and excludes privileged groups with legitimate members that have the adminCount attribute set to 1.
To remediate a deviant object from the AdminCount Attribute Set on Standard Users IoE:
-
In Tenable Identity Exposure, click Indicators of Exposure in the navigation pane to open it.
By default, Tenable Identity Exposure shows only the IoEs that contain deviant objects.
-
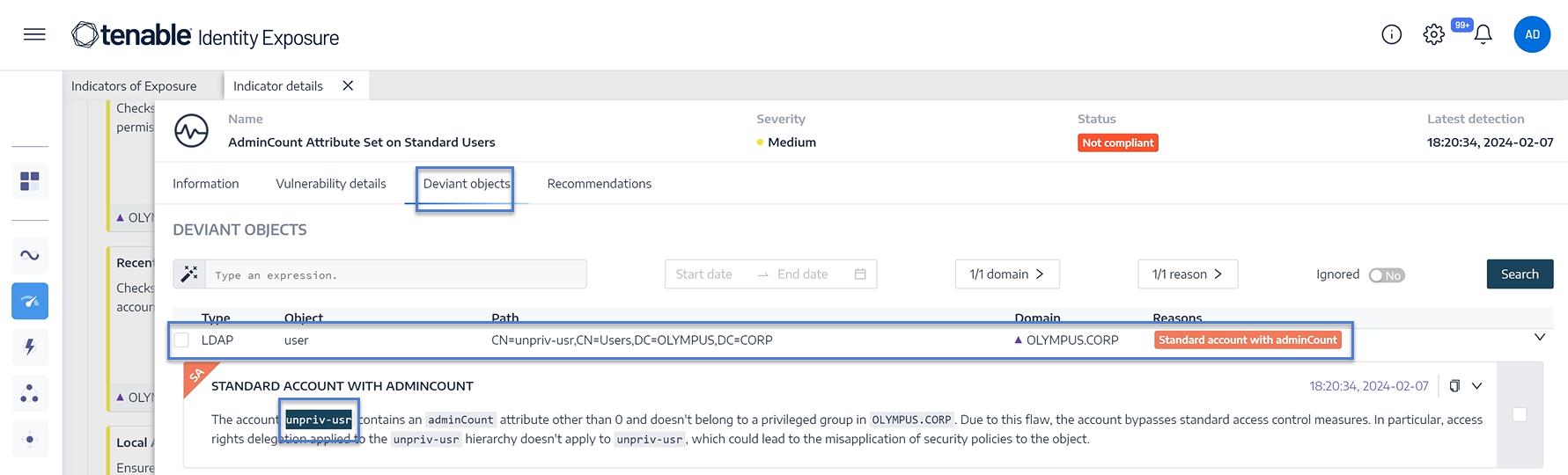
Click on the tile for the AdminCount Attribute Set on Standard Users IoE.
The Indicator details pane opens.
-
Hover over and click on the deviant object to show its details, and note the domain name and the account. (In this example: Domain = OLYMPUS.CORP and the standard account is unpriv-usr)
-
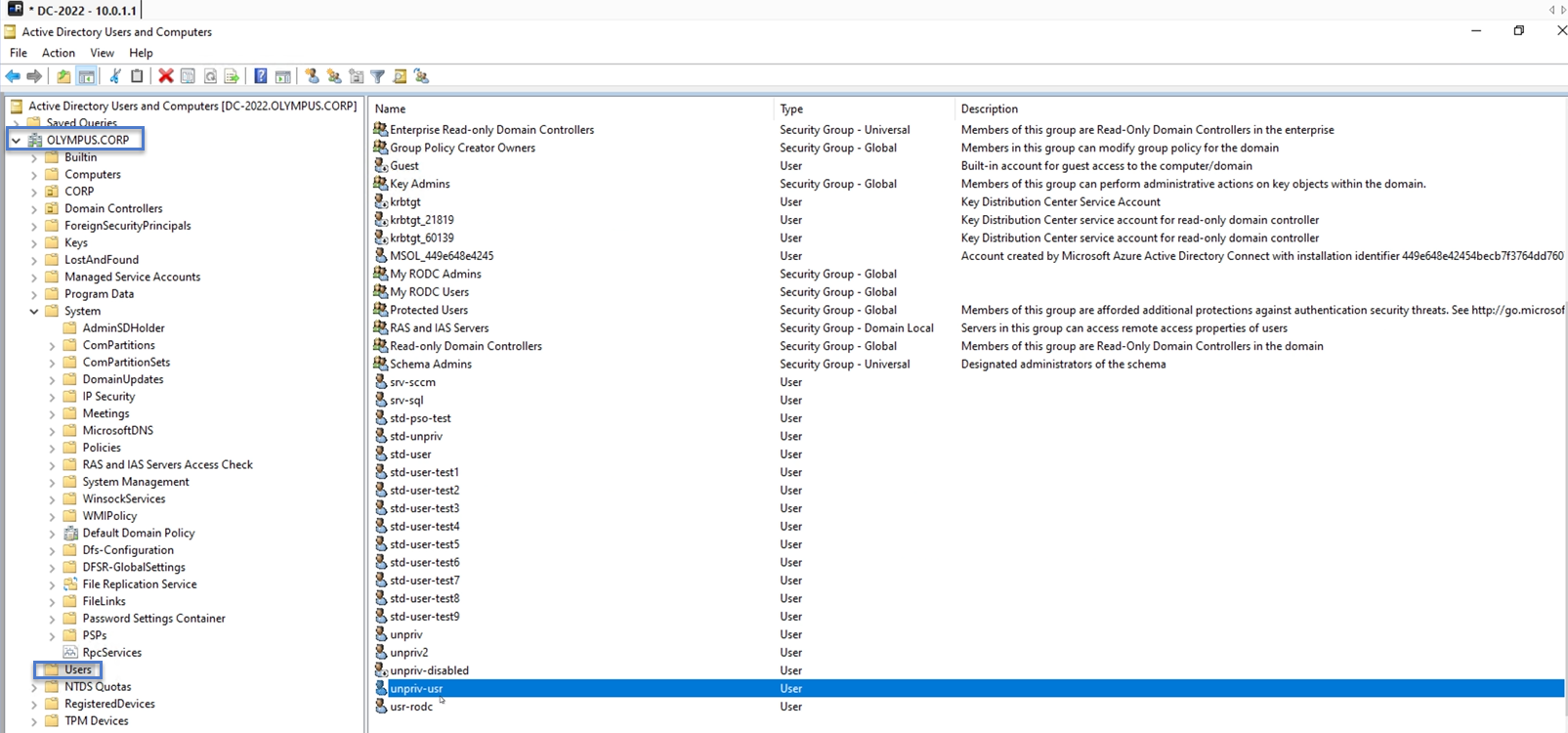
In Remote Desktop Manager (or similar tool), locate the domain name and navigate to Users and the account that Tenable Identity Exposure flagged.
Required permission: You must have an administrator account on the domain to perform the procedure.
-
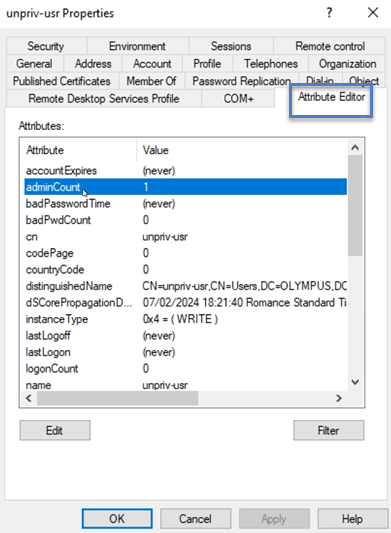
Click on the account name to open its Properties dialog box and select the Attribute Editor tab.
-
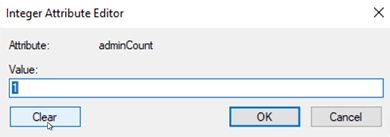
From the list of attributes, click on adminCount to open the Integer Attribute Editor dialog box.
-
In the dialog box, click Clear and OK.
- In Tenable Identity Exposure, return to the Indicator details pane and refresh the page.
The deviant object no longer appears in the list.