Dangerous Kerberos Delegation
The Kerberos protocol, which is central to Active Directory security, permits select servers to reuse user credentials. If an attacker compromises one of these servers, they could steal these credentials and use them to authenticate on other resources.
This critical-level IoE reports all accounts with delegation attributes and excludes disabled accounts. Privileged users should not have delegation attributes. To protect these user accounts, add them to the "Protected Users" group or mark them as "Account is sensitive and cannot be delegated".
To add the account to the "Protected Group":
-
In Tenable Identity Exposure, click Indicators of Exposure in the navigation pane to open it.
By default, Tenable Identity Exposure shows only the IoEs that contain deviant objects.
-
Click on the tile for the Dangerous Kerberos Delegation IoE.
The Indicator details pane opens.
-
Hover over and click on the deviant object to show its details, note the domain name and the account. (In this example: Domain = OLYMPUS.CORP and account = adm-t0)
-
In Remote Desktop Manager (or similar tool), locate the domain name and navigate to the domain and account that Tenable Identity Exposure flagged.
Required permission: You must have an administrator account on the domain to perform the procedure.
-
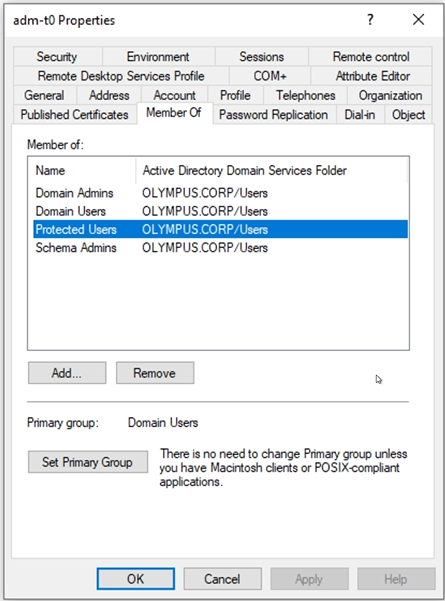
Click on the account name to open its Properties dialog box and select the Member Of tab.
-
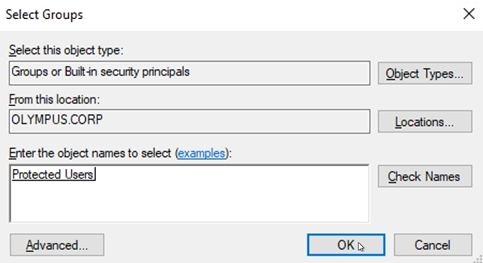
From the member list, click Add.
The Select Groups dialog box appears.
-
Enter the object name "Protected Users" and click Check Names.
-
Click OK to close the dialog box.
-
In the Properties dialog box, click Apply.
The new group appears on the member list.
-
Click OK to close the dialog box.
- In Tenable Identity Exposure, return to the Indicator details pane and refresh the page.
The deviant object no longer appears in the list.
To set the account as "cannot be delegated":
-
In Remote Desktop Manager, locate the domain name and navigate to the domain and account that Tenable Identity Exposure flagged.
Required permission: You must have an administrator account on the domain to perform the procedure.
-
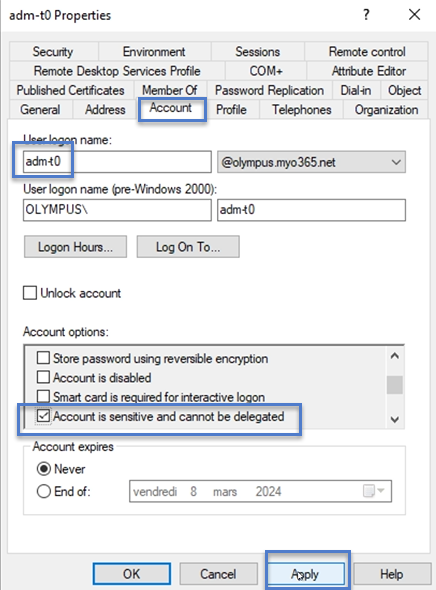
Click on the account name to open its Properties dialog box and select the Account tab.
-
From the list of account options, select "Account is sensitive and cannot be delegated" and click Apply.
-
Click OK to close the dialog box.
- In Tenable Identity Exposure, return to the Indicator details pane and refresh the page.
The deviant object no longer appears in the list.