Connect to an Event Log Collector
You can configure Tenable Identity Exposure to send notifications, such as alerts or security offenses, to an event log collector. Tenable Identity Exposure also allows you to redirect a subset of the traffic flows to a collector for further correlation.
The following illustration shows an integrated process managing Security Information and Event Management (SIEM) events.
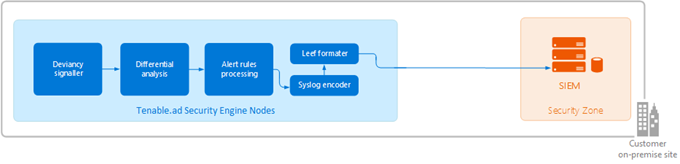
Tenable Identity Exposure uses the Syslog protocol to carry messages in LEEF format.
Tenable Identity Exposure supports most SIEMs or event log collectors. Tenable Identity Exposure supports the following event collectors:
-
IBM QRadar
-
Splunk
-
RSA Netwitness
-
LogRhythm
-
Micro Focus ArcSight
-
Tibco Loglogic
-
McAfee Enterprise Security Manager