Search Deviant Objects
You can search for deviant objects manually or using the wizard.
Wizard Search
The search wizard allows you to create query expressions.
-
When you use frequent expressions in the search box, you can add them to a list of bookmarks for later use.
-
When you enter an expression in the search box, it Tenable Identity Exposure saves this expression in its History pane for you to reuse.
To search for a deviant object using the wizard:
-
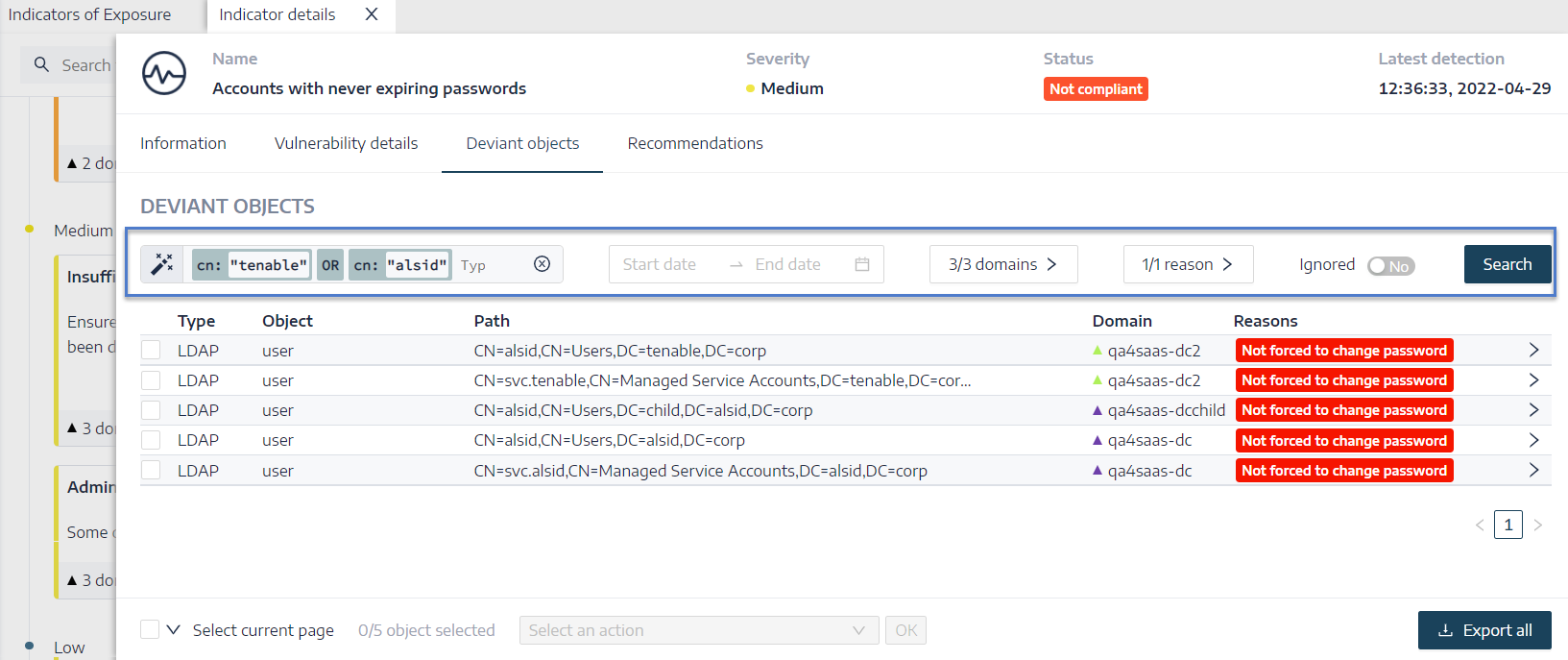
Display the list of Deviant Objects
-
Click on the
 icon.
icon.The Edit Query Expression pane opens.
-
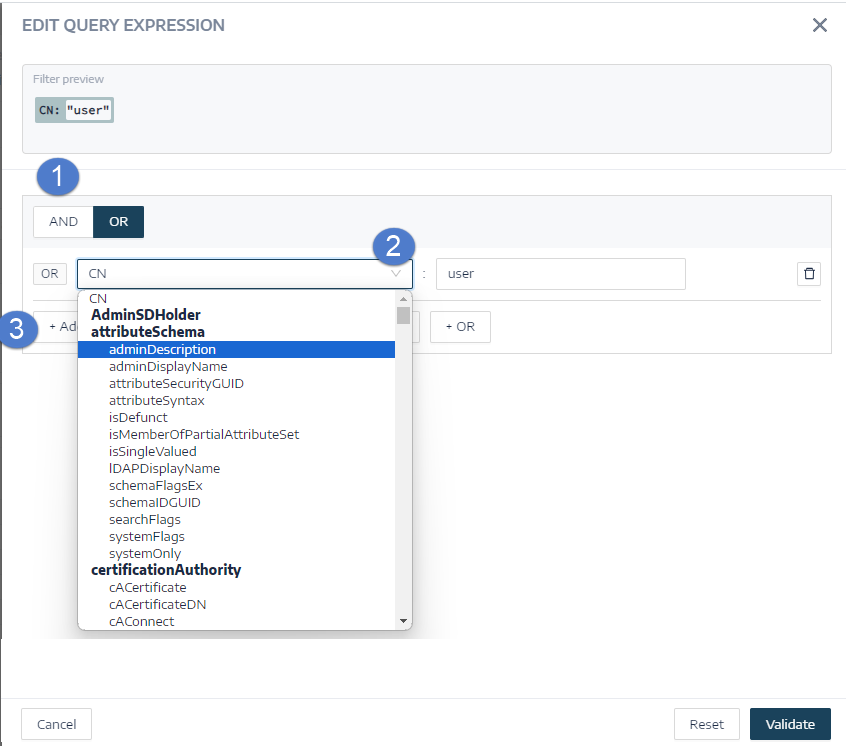
To define the query expression in the panel, click on the AND or the OR operator button (1) to apply to the first condition.
-
Select an attribute from the drop-down menu and enter its value (2).
-
Do any of the following:
-
To add an attribute, click + Add a new rule (3).
-
To add another condition, click Add a new condition+AND or +OR operator. Select an attribute from the drop-down menu and enter its value.
-
To restrict the search to deviant objects, click the Deviant only toggle to allow. Select the +AND or +OR operator to add the condition to the query.
-
To delete a condition or rule, click the
 icon.
icon.
-
-
Click Validate to run the search or Reset to modify your query expressions.
Manual Search
To filter deviant objects that match specific character strings or patterns, you can type an expression in the search box to refine results using the Boolean operators *, AND, and OR. You can encapsulate OR statements with parentheses to modify search priority. The search looks for any specific value in an Active Directory attribute. To search the Trail Flow manually:
To search for a deviant object manually:
-
Display the list of Deviant Objects.
-
In the Search box, type a query expression.
-
You can filter the search results as follows:
-
Click on the Calendar box to select a start date and an end date.
-
Click on n/n Domains to select forests and domains.
-
-
Click Search.
Tenable Identity Exposure updates the list with the results matching your search criteria.
Grammar and Syntax
A manual query expression uses the following grammar and syntax:
-
Grammar: EXPRESSION [OPERATOR EXPRESSION]*
-
Syntax: __KEY__ __SELECTOR__ __VALUE__
where:
-
__KEY__ refers to the AD object attribute to search (such as CN, userAccountControl, members, etc.)
- __SELECTOR__ refers to the operator: :, >, <, >=, <=.
-
__VALUE__ refers to value to search for.
You can use more keys to look for specific content:
-
isDeviant looks for events that created a deviance.
-
You can combine multiple Trail Flow query expressions using the AND and OR operators.
Examples:
-
Look for all objects containing the string alice into the common name attribute: cn:"alice"
-
Look for all objects containing the string alice in the common name attribute and which created a specific deviance: isDeviant:"true" and cn:"alice"
-
Look for a GPO named Default Domain Policy: objectClass:"groupPolicyContainer" and displayname:"Default Domain Policy"
-
Look for all deactivated accounts with a SID containing S-1-5-21: userAccountControl:"DISABLE" and objectSid:"S-1-5-21"
-
Look for all script.ini files in SYSVOL: globalpath:"sysvol" and types:"SCRIPTSini"
Note: Here, types refers to the object attribute and not the column header.
See also