SYSVOL Hardening Interference with Tenable Identity Exposure
SYSVOL is a shared folder located on each Domain Controller (DC) in an Active Directory domain. It stores the folders and files for Group Policies (GPOs). The content of SYSVOL replicates across all DCs, and is accessed via Universal Naming Convention (UNC) paths such as \\<example.com>\SYSVOL or \\<DC_IP_or_FQDN>\SYSVOL.
SYSVOL hardening refers to the use of the UNC Hardened Paths parameter, also known as “UNC hardened access”, “hardened UNC paths”, “UNC path hardening”, or “hardened paths”, etc. This feature came about to respond to the MS15-011 (KB 3000483) vulnerability in Group Policy. Many cybersecurity standards such as CIS Benchmarks mandate the enforcement of this feature.
When you apply this hardening parameter on Server Message Block (SMB) clients, it actually increases the security of the domain-joined machines to ensure that the GPO content they retrieve from SYSVOL is free from tampering by an attacker on the network. But in certain situations, this parameter can also interfere with Tenable Identity Exposure’s operation.
Follow the guidance in this troubleshooting section if you notice that hardened UNC paths are disrupting the connectivity between Tenable Identity Exposure and the SYSVOL share.
Affected environments
The following Tenable Identity Exposure deployment options may experience this issue:
-
On-Premises
-
SaaS with Secure Relay
This deployment option is not affected:
-
SaaS with VPN
SYSVOL hardening is a client-side parameter, which means that it operates on the machines that connect to the SYSVOL share and not on the Domain Controllers.
Windows enables this parameter by default, and it can interfere with Tenable Identity Exposure.
Some organizations also want to ensure the activation of this parameter and enforce it by using the related GPO setting or by setting the corresponding registry key directly.
-
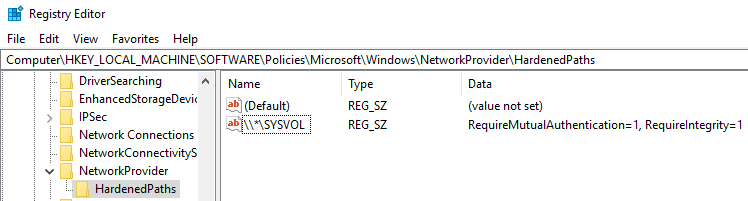
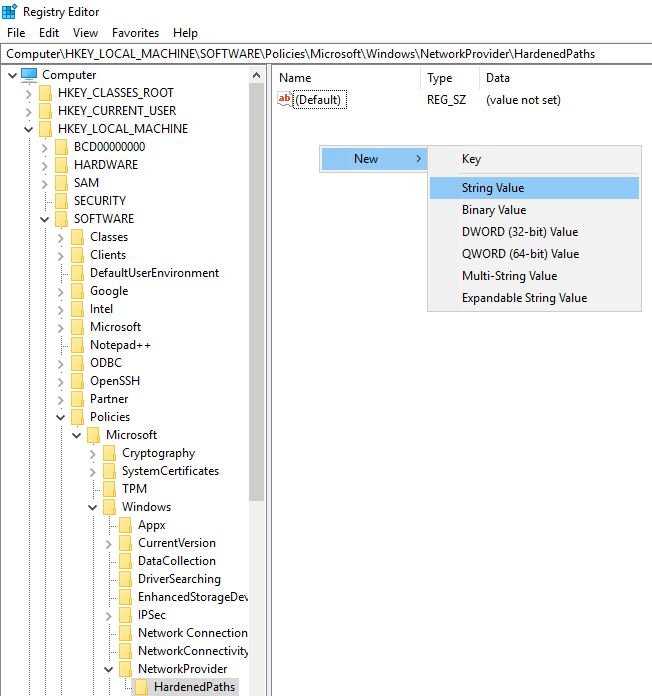
You can find the registry keys related to UNC hardened paths under “HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths”:
-
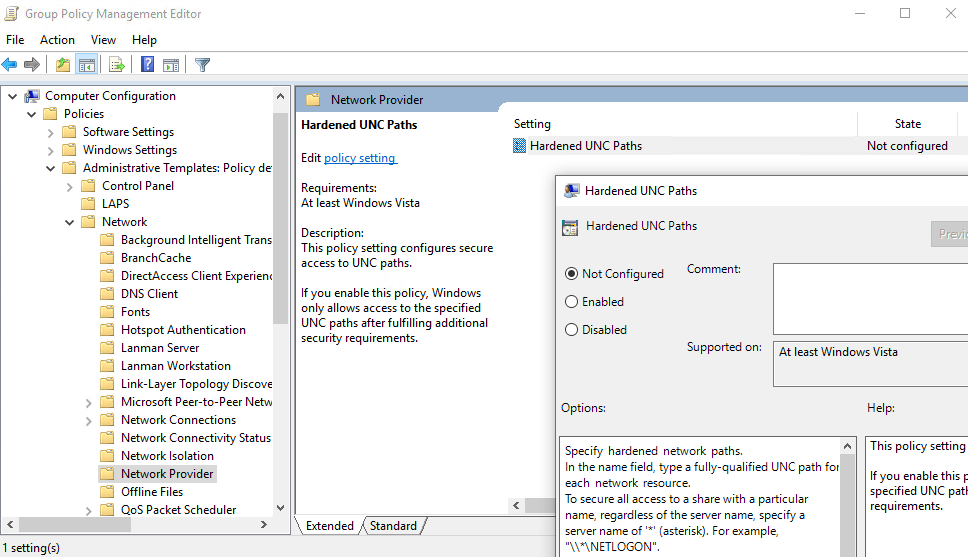
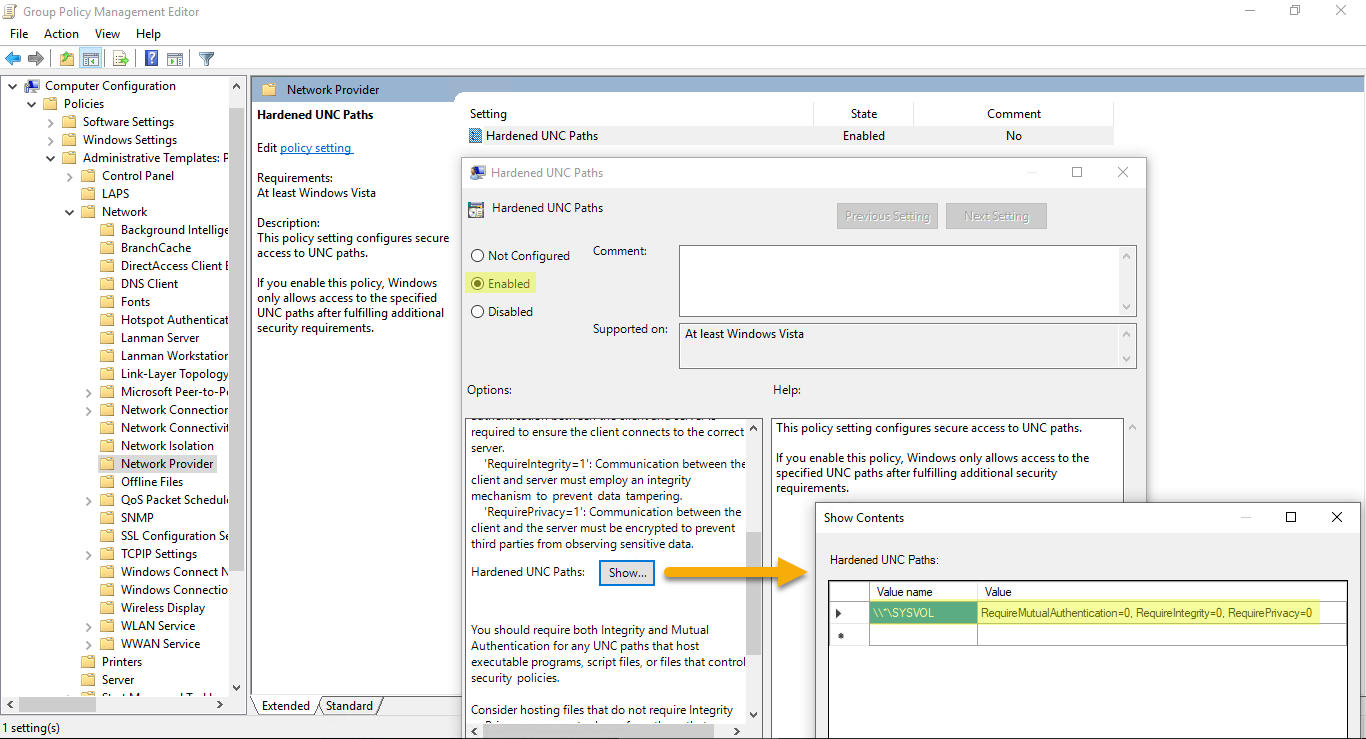
You can find the corresponding GPO setting under “Computer Configuration/Administrative Templates/Network/Network Provider/Hardened UNC paths”:
SYSVOL hardening enforcement occurs when a UNC path referring to SYSVOL – for example “\\*\SYSVOL” – has the parameters “RequireMutualAuthentication” and “RequireIntegrity” set to the value “1”.
Signs of SYSVOL Hardening Issues
When you suspect that SYSVOL hardening interferes with Tenable Identity Exposure, check for the following:
To check for hardening issues:
-
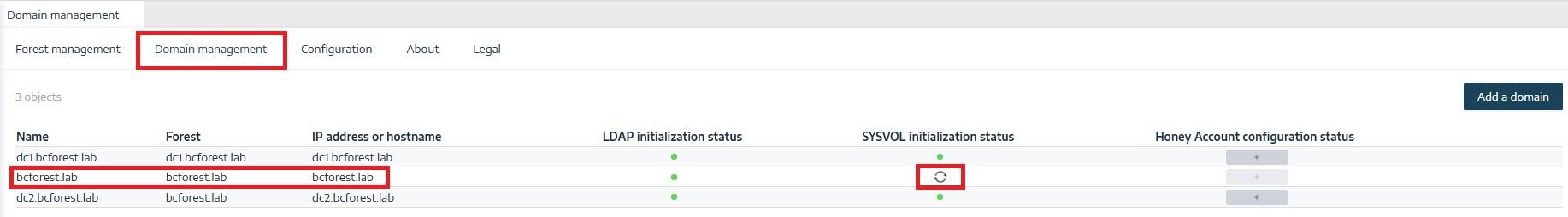
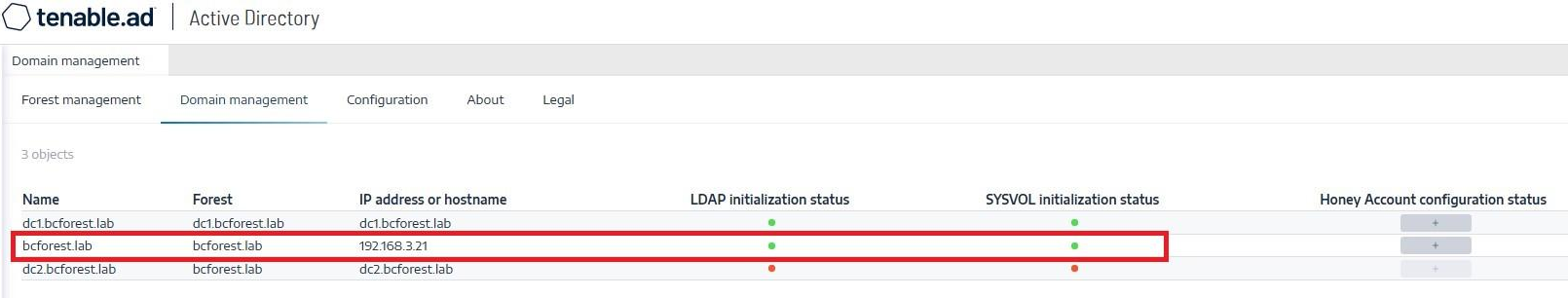
In Tenable Identity Exposure, go to System > Domain Management to view the LDAP and SYSVOL initialization status for each domain.
A domain with normal connectivity shows a green indicator, while a domain with connectivity issues can show a crawling indicator that continues endlessly.
-
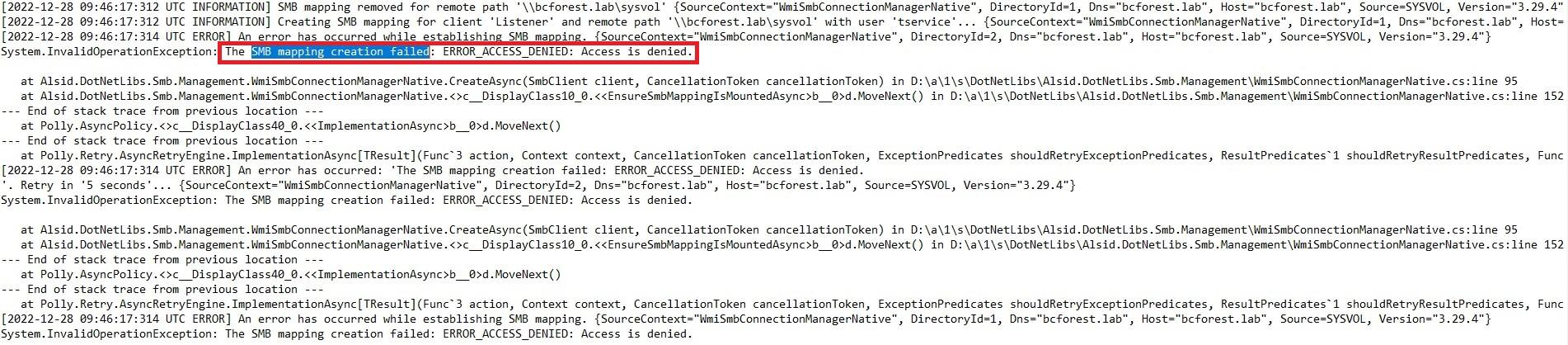
On the Directory Listener or Relay machine, open the logs folder: <Installation Folder>\DirectoryListener\logs.
-
Open the Ceti log file and search for the string "SMB mapping creation failed" or “Access is denied”. Error logs containing this phrase indicate that UNC hardening is likely in place on the Directory Listener or Relay machine.
Remediation Options
There are two possible remediation options: Switching to Kerberos authentication or Disabling SYSVOL hardening.
Switching to Kerberos authentication
This is the preferred option since it avoids disabling the hardening feature.
It is only when connecting to the monitored Domain Controller(s) using NTLM authentication that SYSVOL hardening interferes with Tenable Identity Exposure. This is because NTLM is not compatible with the “RequireMutualAuthentication=1” parameter. Tenable Identity Exposure also supports Kerberos. It is not necessary to disable SYSVOL hardening if you configure and use Kerberos properly. For more information, see Kerberos Authentication
Disabling SYSVOL hardening
If you cannot switch to Kerberos authentication, you also have the option of disabling SYSVOL hardening.
Windows enables SYSVOL hardening by default, so it is not sufficient to remove the registry key or the GPO setting. You must explicitly disable it and apply this change only on the machine hosting the Directory Listener (on-premises) or the Relay (SaaS with Secure Relay). This does not affect other machines, and you never need to disable SYSVOL hardening on the Domain Controllers themselves.
The Tenable Identity Exposure installers used on the machine hosting the Directory Listener (on-premises) or Relay (SaaS with Secure Relay) already disable SYSVOL hardening locally. However, a GPO or a script in your environment may remove or overwrite the registry key.
There are two possible cases:
-
If the Directory Listener or Relay machine is not domain-joined — You cannot use a GPO to configure the machine. You must disable SYSVOL hardening in the registry (see Registry: Graphic User Interface or Registry:PowerShell).
-
If the Directory Listener or Relay machine is domain-joined (which Tenable Identity Exposure does not recommend) — You can either apply the setting directly either in the registry (see Registry: Graphic User Interface or Registry:PowerShell) or using a GPO. Using any of these methods, you must ensure that a GPO or a script does not overwrite the registry key. You can do this in either way:
-
Carefully review all the GPOs that apply on this machine.
-
Apply the change and wait a bit, or force the GPOs application with “gpupdate /force”, and check that the registry key kept its value.
-
After you restart the Directory Listener or Relay machine, the crawling indicator on the modified domain should change to a green indicator:
Registry: Graphic User Interface
To disable SYSVOL hardening in the Registry using the GUI:
-
Connect to the Directory Listener or Relay machine with administrative rights.
-
Open the Registry Editor and navigate to: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths.
-
Create a key named “\\*\SYSVOL” if it doesn’t already exist, as follows:
-
Double-click the “\\*\SYSVOL” key (newly created or previously existing) to open the Edit String window.
-
In the Value data field, enter the following value: RequireMutualAuthentication=0, RequireIntegrity=0, RequirePrivacy=0
-
Click Save.
The result should appear as follows:
-
Restart the machine.
Registry:PowerShell
To disable SYSVOL hardening in the registry using PowerShell:
-
Collect the current values of the UNC hardened paths registry keys for reference using this PowerShell command:
CopyGet-Item -Path "HKLM:\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths" -
Set the recommended value:
CopyNew-ItemProperty -Path "HKLM:\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths" -Name "\\*\SYSVOL" -Value "RequireMutualAuthentication=0, RequireIntegrity=0, RequirePrivacy=0" -
Restart the machine.
GPO
Prerequisite: You must connect as an Active Directory user with the rights to create GPOs on the domain and to link them to the Organizational Unit that contains the Tenable Identity Exposure Directory Listener or Relay machine.
To disable SYSVOL hardening using a GPO:
-
Open the Group Policy Management console.
-
Create a new GPO.
-
Edit the GPO and browse to the following location: Computer Configuration/Administrative Templates/Network/Network Provider/Hardened UNC paths.
-
Enable this setting and create a new Hardened UNC Path with:
-
Value name = \\*\SYSVOL
-
Value = RequireMutualAuthentication=0, RequireIntegrity=0, RequirePrivacy=0
The result should appear as follows:
-
-
Click OK to confirm.
-
Link this GPO to the Organizational Unit that contains theTenable Identity Exposure Directory Listener or Relay machine. You can also use the security group filters GPO feature to ensure that this GPO applies only to this machine.
Specific UNC path exceptions
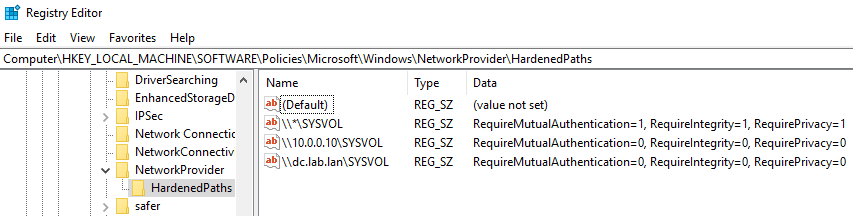
The previous procedures disable SYSVOL hardening using a wildcard UNC path: “\\*\SYSVOL”. You can also disable it only for a specific IP address or FQDN. This means that you can keep the UNC hardened paths settings enabled (with value “1”) for “\\*\SYSVOL”, and have an exception corresponding to each IP address or FQDN of a Domain Controller configured in Tenable Identity Exposure.
The following image shows an example of SYSVOL hardening enabled for all servers (“*”), except for “10.0.0.10” and “dc.lab.lan”, which are domain controllers that we configured in Tenable Identity Exposure:
You can add these additional settings using the registry or GPO methods described above.
Risks When Disabling SYSVOL Hardening
SYSVOL hardening is a security feature and disabling it can raise valid concerns.
-
Non-domain-joined machines — There is no risk in disabling SYSVOL hardening. Since these machines do not apply GPOs, they do not get content from the SYSVOL share to execute it.
-
Domain-joined machines (Directory Listener or Relay machine) which Tenable Identity Exposuredoes not recommend — If there is a potential risk of having an attacker in a “Man-in-the-Middle” situation between the Directory Listener or Relay machine and the Domain Controllers, it is unsafe to disable SYSVOL hardening. In this case, Tenable Identity Exposure recommends that you switch to Kerberos authentication instead.
The scope of this deactivation is only on the Directory Listener or Relay machine and not other domain computers, and never the Domain Controllers.