Configure Rule-Based Scanning
You can initiate a scan against source or destination IP addresses whenever the rule gets triggered. You can create different types of rules or can update the existing rule and update the rule response to save the IP addresses in the Tenable reference sets. Whenever that rule gets triggered it will add source/destination IP address in the reference set named Tenable Security Center scan IP and Tenable Vulnerability Management scan IP. A background script runs periodically, and it launches a scan against all the IP addresses from the reference set. The default periodic time is 1200 seconds.
To create a rule:
-
On the IBM QRadar SIEM console, click the
 menu button.
menu button.The Menu options appear.
-
Click Offenses.
The Offenses menu appears.
-
In the Offenses menu, click Rules.
The Rules page appears.
-
In the Rules menu, click Actions.
A drop-down box appears.
Note: (Optional) You can also select conditions for your rule according to your needs.
-
Select one of the New Rule options.
The Rule Wizard window appears.
-
Click Next.
Note: If you experience difficulties with user interface elements, problems may exist with your browser. Try again from a different browser.
-
Select the source where the rules are generated.
-
Click Next.
The Rule Wizard: Rule Response window appears.
Rule Wizard: Rule Response Configuration
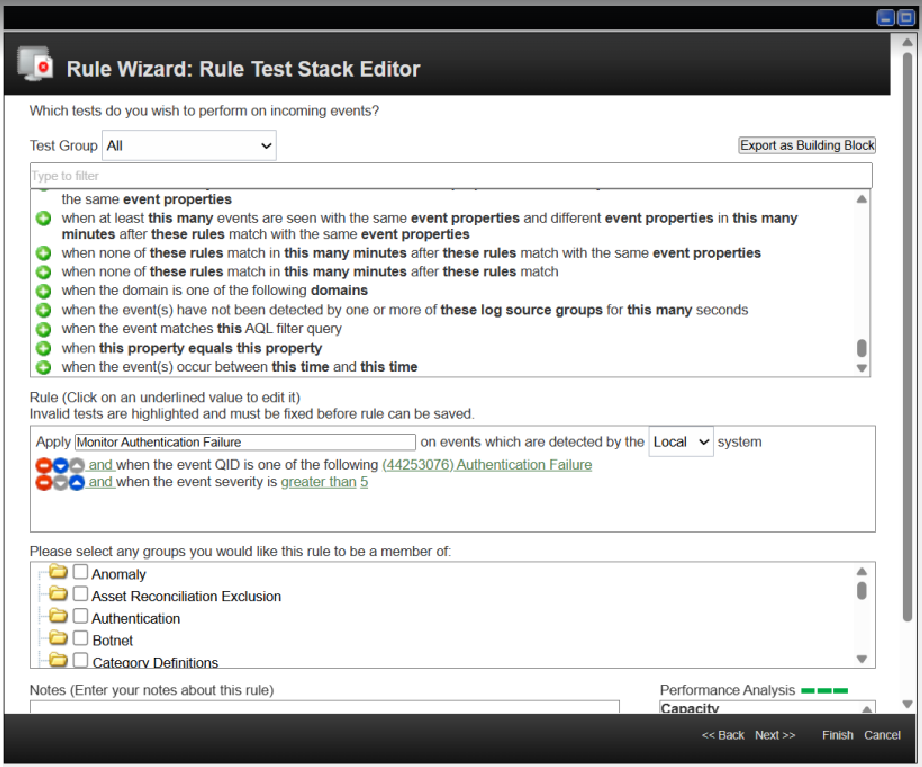
There are many options to generate a rule. You can add the rule name and rule conditions based on your needs. The rule conditions should be customized according to the specific use case. For instance, if the objective is to monitor authentication failure events and subsequently scan the source IPs in Tenable, you can configure the conditions as shown in the following example image.
Note: This rule condition is just an example. You need to create your own rule conditions based on your requirement.
-
(Optional) You can add the Rule Action of your choice.
-
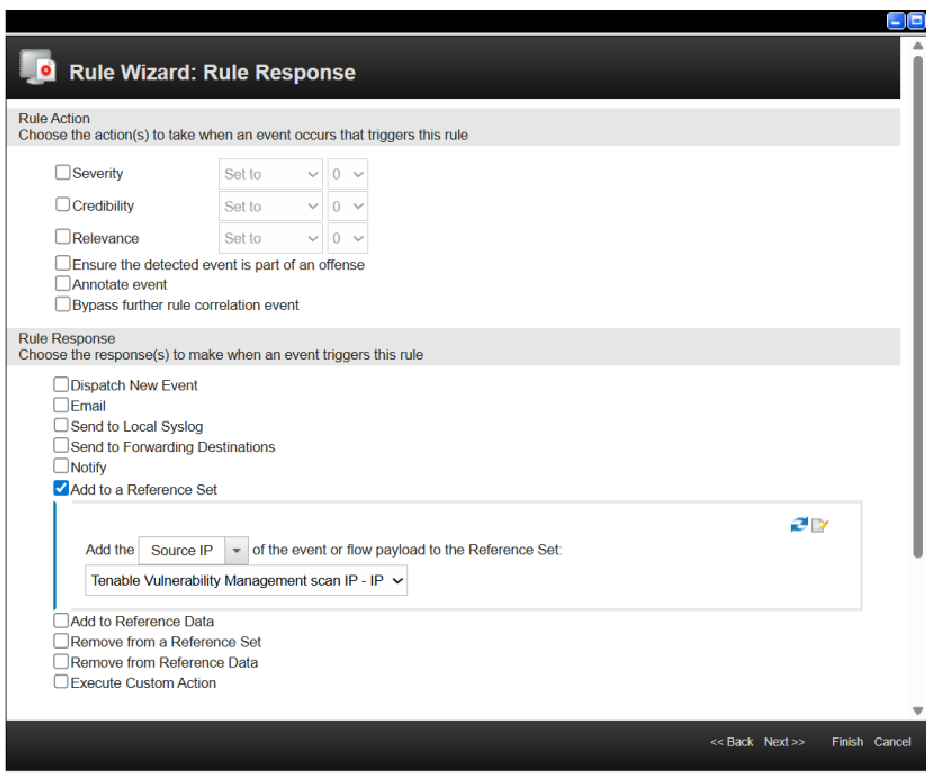
In the Rule Response section, select Add to a Reference set checkbox.
A drop-down appears.
-
In the dropdown (located between Add the ” - “ of the events or flow payload to the Reference set.) select Source IP or Destination IP based on the requirement.
-
In the Reference set dropdown select Tenable Vulnerability Management scan IP (if using Tenable Vulnerability Managementcredentials) or select the Tenable Security Center scan IP (if using Tenable Security Center credentials).
Note: If the Tenable Vulnerability Management scan IP and Tenable Security Center scan IP reference sets are not visible in the dropdown, click the refresh icon on the right side.
-
After you make your rules selections, click Finish.
Caution: Without the Ensure the detected event is part of an offense and Add to a Reference Set settings enabled, QRadar cannot create an event in the All Offenses category of the Offenses tab of the dashboard. The All Offenses category is where you can review the vulnerabilities you set the rules for.
Tip: You can check your active scans launched from the IBM QRadar SIEM integration in the Tenable App Dashboard tab in the QRadar user interface.
Final Checks
If you select Source IP in the first dropdown and Tenable Security Center scan IP in the second dropdown, then whenever this rule gets triggered it adds Source IP in the Tenable Security Center scan IP reference set. A background script launches the scan against that IP address on the Tenable Security Center portal.
If you want to launch a scan for source IP and destination for both Tenable Vulnerability Management and Tenable Security Center, you must create four rules:
- Scan source IP with Tenable Vulnerability Management
- Scan source IP with Tenable Security Center
- Scan destination IP with Tenable Vulnerability Management
- Scan destination IP with Tenable Security Center.
After a rule is created, if there is any new event or flow that matches the criteria of that rule, then the rule is triggered, and it creates an offense and adds an IP address in the reference set.