Configure Tenable Vulnerability Management for Lieberman Database
Tenable Vulnerability Management provides full database support for Lieberman. Enable the plugins in the scanner to display them in the output.
What role is required to perform this configuration?
To configure Lieberman database integration:
-
Log in to Tenable Vulnerability Management.
-
Click Scans.
The My Scans page appears.
-
Click + New Scan.
The Scan Templates page appears.
-
Click a Scan Template. For example, this procedure walks through the Advanced Network Scan template.
The Scan Configuration page appears.
- In the Name box, type a name for the scan.
- In the Targets box, type an IP address, hostname, or range of IP addresses.
- (Optional) You can add a description, folder location, scanner location, and specify target groups.
-
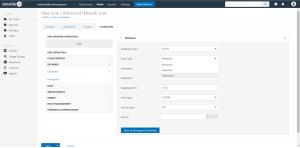
Click the Credentials tab.
The Credentials options appear.
- In the Add Credentials section, expand the Database section.
-
Click the Database option.
The Database options appear.
- Click the Database Type drop-down box.
- Click Oracle
- Click the Auth Type drop-down box.
-
Click Lieberman.
The Lieberman options appear.
-
Configure each option for the Database authentication.
Option Description Required
Username The target system’s username. yes Lieberman host The Lieberman IP/DNS address.
Note: If your Lieberman installation is in a subdirectory, you must include the subdirectory path. For example, type IP address or hostname / subdirectory path.
yes Lieberman port The port on which Lieberman listens. yes Lieberman user The Lieberman explicit user for authenticating to the Lieberman API. yes Lieberman password The password for the Lieberman explicit user. yes Use SSL If Lieberman is configured to support SSL through IIS, check for secure communication.
no Verify SSL Certificate If Lieberman is configured to support SSL through IIS and you want to validate the certificate, check this option. Refer to Custom CA documentation for how to use self-signed certificates.
no
System Name In the rare case your organization uses one default Lieberman entry for all managed systems, enter the default entry name. no Database Port The port on which Tenable Vulnerability Management communicates with the database. yes Database Name (PostgreSQL and DB2 databases only) The name of the database. no - Click Save.