Configure Tenable Vulnerability Management for Lieberman SSH
To integrate with SSH:
-
Log in to Tenable Vulnerability Management.
-
Click Scans.
The My Scans page appears.
-
Click + New Scan.
The Scan Templates page appears.
-
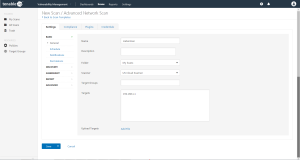
Select a Scan Template.
The Settings page for the selected scan appears.
- In the Name box, type a name for the scan.
-
In the Targets box, type an IP address, hostname, or range of IP addresses.
- (Optional) You can add a description, folder location, scanner location, and specify target groups.
-
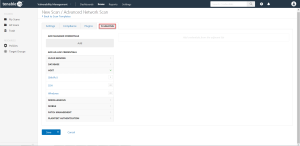
Click on the Credentials tab.
The Add Managed Credentials options appear.
-
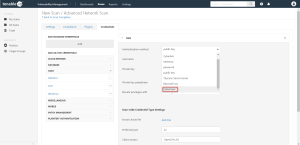
In the left-hand menu, select SSH.
The SSH options appear.
-
From the Authentication method drop-down, select Lieberman.
The Lieberman options appear.
-
Configure each field for SSH authentication.
Option Description Required Username The target system’s username. yes
Lieberman host The Lieberman IP/DNS address.
Note: If your Lieberman installation is in a subdirectory, you must include the subdirectory path. For example, type IP address or hostname / subdirectory path.
yes
Lieberman port The port on which Lieberman listens. yes
Lieberman API URL The URL Tenable Vulnerability Management uses to access Lieberman. no Lieberman user The Lieberman explicit user for authenticating to the Lieberman RED API. yes
Lieberman password The password for the Lieberman explicit user. yes
Lieberman Authenticator The alias used for the authenticator in Lieberman. The name should match the name used in Lieberman.
Note: If you use this option, append a domain to the Lieberman user option, i.e., domain\user.
no Lieberman Client Certificate The file that contains the PEM certificate used to communicate with the Lieberman host.
Note: If you use this option, you do not have to enter information in the Lieberman user, Lieberman password, and Lieberman Authenticator fields.
no Lieberman Client Certificate Private Key The file that contains the PEM private key for the client certificate. no Lieberman Client Certificate Private Key Passphrase The passphrase for the private key, if required. no Use SSL If Lieberman is configured to support SSL through IIS, check for secure communication.
no
Verify SSL Certificate If Lieberman is configured to support SSL through IIS and you want to validate the certificate, check this option. Refer to Custom CA documentation for how to use self-signed certificates.
no
System Name In the rare case your organization uses one default Lieberman entry for all managed systems, enter the default entry name. no
- Click Save.
What to do next:
-
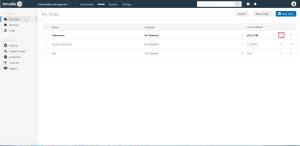
To verify the integration is working, click the Launch button to initiate an on-demand scan.
-
Once the scan has completed, select the completed scan and look for Plugin ID 97993 and the corresponding message - It was possible to log into the remote host via SSH using 'password' authentication. This validates that authentication was successful.