Configure Tenable Nessus Manager with HashiCorp Vault (Database)
In Tenable Nessus Manager, you can integrate with HashiCorp Vault using database credentials. Complete the following steps to configure Tenable Nessus Manager with HashiCorp Vault for database credentials. You can Enable Database Plugins in the scanner to display them in the output.
Requirements
Required User Role: Standard, Administrator, or System Administrator
- Tenable Nessus Manager account
- HashiCorp Vault account
To integrate Tenable Nessus Manager with HashiCorp Vault using database credentials:
-
Log in to Tenable Nessus Manager.
-
Click Scans.
The My Scans page appears.
-
Click + New Scan.
The Scan Templates page appears.
-
Select a scan template.
The selected scan template Settings page appears.
-
In the Name box, type a name for the scan.
- In the Targets box, type an IP address, hostname, or range of IP addresses.
- (Optional) Add a description, folder location, scanner location, and specify target groups.
-
Click the Credentials tab.
The Credentials options appear. By default, the Categories drop-down box displays Host.
-
In the Categories drop-down box, select Database.
The Database options appear below.
-
In the Categories list, click Database.
The Database options appear.
-
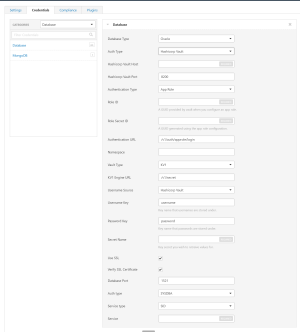
In the Database section, click the Database Type drop-down box.
The Database options appear.
-
In the Database Type drop-down box, click your preferred database: PostgreSQL, DB2, MySQL, SQL Server, Oracle, or Sybase ASE.
The selected Database options appear.
-
In the Auth Type drop-down box, click Hashicorp.
The HashiCorp Vault options appear.
-
Configure the Database credentials.
Option Description Required
Hashicorp Vault host The Hashicorp Vault IP address or DNS address.
Note: If your Hashicorp Vault installation is in a subdirectory, you must include the subdirectory path. For example, type IP address or hostname / subdirectory path.
yes Hashicorp Vault port The port on which Hashicorp Vault listens. yes Authentication Type Specifies the authentication type for connecting to the instance: App Role or Certificates.
If you select Certificates, additional options for Hashicorp Client Certificate and Hashicorp Client Certificate Private Key appear. Select the appropriate files for the client certificate and private key.
yes Role ID The GUID provided by Hashicorp Vault when you configured your App Role. yes Role Secret ID The GUID generated by Hashicorp Vault when you configured your App Role.
yes Authentication URL The path/subdirectory to the authentication endpoint. This is not the full URL. For example:
/v1/auth/approle/login
yes
Namespace The name of a specified team in a multi-team environment. no Vault Type The HashiCorp Vault version: KV1, KV2, AD, or LDAP. For additional information about HashiCorp Vault versions, see the HashiCorp Vault documentation.
yes KV1 Engine URL (KV1) The URL HashiCorp Vault uses to access the KV1 engine.
Example: /v1/path_to_secret. No trailing /
yes, if you select the KV1 Vault Type KV2 Engine URL (KV2) The URL HashiCorp Vault uses to access the KV2 engine.
Example: /v1/path_to_secret. No trailing /
yes, if you select the KV2 Vault Type AD Engine URL (AD) The URL HashiCorp Vault uses to access the active directory engine.
Example: /v1/path_to_secret. No trailing /
yes, if you select the AD Vault Type LDAP Engine URL (LDAP) The URL HashiCorp Vault uses to access the LDAP engine.
Example: /v1/path_to_secret. No trailing /
yes, if you select the LDAP Vault Type Username Source (KV1 and KV2) A drop-down box to specify whether the username is input manually or pulled from Hashicorp Vault. yes Username Key (KV1 and KV2) The name in Hashicorp Vault that usernames are stored under. yes Password Key (KV1 and KV2) The key in Hashicorp Vault that passwords are stored under. yes Secret Name (KV1, KV2, and AD) The key secret you want to retrieve values for. yes Use SSL If enabled, Tenable Nessus Manager uses SSL for secure communications. Configure SSL in Hashicorp Vault before enabling this option. no Verify SSL Certificate If enabled, Tenable Nessus Manager validates the SSL certificate. You must configure SSL in Hashicorp Vault before enabling this option. no Database Port The port on which Tenable Nessus Manager communicates with the database. yes Auth Type The authentication method for the database credentials. Oracle values include:
- SYSDBA
- SYSOPER
- NORMAL
yes Service Type (Oracle databases only) Valid values include: SID and SERVICE_NAME. yes Service (Oracle database only) A specific field for the configuration for the database. yes - Click Save.