Analyzing Events
A wide variety of Tenable Log Correlation Engine analysis and reporting tools are available to Tenable Security Center users. These users can make use of any Tenable Log Correlation Engine event that intersects with their range of managed IP addresses. All analysis and reporting options are described in the Tenable Security Center User Guide.
Identifying Vulnerabilities
Tenable Log Correlation Engine can leverage log data to find vulnerabilities. The Tenable plugins that report this information will have the plugin ID range of 800,000 - 899,999.
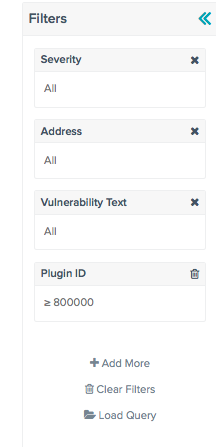
You can filter for the vulnerabilities identified by Tenable Log Correlation Engine in Tenable Security Center by using the “Filters” and selecting “Plugin ID”, then selecting “≥” and then entering “800000.” The filter setting is pictured below:
TASL Scripts
After PRM processing normalizes an event, the event is submitted to the Tenable Log Correlation Engine TASL engine for advanced processing by TASL scripts. TASL scripts are used for many types of detection events such as thresholds, successful attack detection, and alerting. By default, all TASL scripts are enabled in the Tenable Log Correlation Engine server; however they can be disabled manually in the “TASL and Plugins” section of the Tenable Log Correlation Engine interface described in detail earlier in this document. For more information regarding TASL scripts review the Tenable Log Correlation Engine TASL Reference Guide.