Advanced Configuration
The Advanced configuration section is used to fine tune your Tenable Log Correlation Engine server configuration. Each section that is changed in the Advanced section will require that the Update button is selected before the updates are completed. Select Cancel to clear any unwanted updates.
The Advanced configuration section includes the following groups of settings:
- Storage
- Tenable Log Correlation Engine Web Server
- Sensor Names
- Clients
- User Tracking
- Host Discovery and Vulnerabilities
- Statistical Alerts
- Resource Usage and Performance
- DNS Caching
- Data Forwarding
- TCP Syslog
- Encrypted TCP Syslog
- Correlation
- TASL and Plugins
- Event Rules
The options available under the Storage subsection are Store Unnormalized Logs and Disk Alert Percentage. These options are described in the table below.
| Option | Description |
|---|---|
|
Store Unnormalized Logs |
If enabled, then Tenable Log Correlation Engine will store logs that cannot be normalized by existing Tenable Log Correlation Engine plugins. These logs will have the type and event set to unnormalized and will still be available for text, IP, and sensor-based searches. |
|
Disk Alert Percentage |
When filesystem usage exceeds the specified percentage (from 1 to 99 percent), an alert is generated so that you can take action to ensure the Tenable Log Correlation Engine server does not exhaust disk space for log storage. The default value is 75 percent. |
Tenable Log Correlation Engine Web Server
The Tenable Log Correlation Engine Web Server section allows you to specify parameters governing login parameters for user access. These options are described in the table below.
| Option | Description |
|---|---|
|
Login Banner |
Banner to display prior to login, requiring users to positively acknowledge a customized statement or warning. Up to 1300 characters. |
|
Enforce Complex Passwords |
Require web server user passwords to have at least 1 uppercase, 1 lowercase, 1 number, and 1 special character. |
|
Min Password Length |
Minimum length of a password for a web server user login. This limit only applies to passwords that are created after this option is modified. |
|
Idle Session Timeout |
Idle login sessions will be logged out after the amount of time specified in minutes. To disable the timeout, set the value to 0. |
|
Web Server Port |
Specifies the port used to access the Tenable Log Correlation Engine interface. By default, port 8836. |
|
Enable SSL for Web Server |
When enabled, the engine will require SSL protection for connections to the web server. If this setting is changed, users are disconnected and must log back into the server again. |
|
Enable SSL Client Certificate Authentication |
If the web_UI__login__client_CA_cert_path configuration attribute is set, the web server will only accept SSL client certificates for user authentication. By default, this option is disabled and the web server allows login only with a username and password. |
This option allows you to override the discovered name of a syslog sensor with a name that is more identifiable in the environment. For example if the host is syslogserver06.example.com but that server resides in the research area of the environment, you can set a name that is more identifiable, such as research_syslog.
Normally, the sensor name is set to one of the following:
- The source of the log
- The sensor name set on the client itself
- The syslog source
- The plugin that normalizes the log
If you specify a sensor name using the Tenable Log Correlation Engine interface, that name will always be applied to the sensor that corresponds to the IP address. When creating new sensor names, values must be set for both the Sensor Name and IP Address.
| Option | Description |
|---|---|
|
Sensor Name |
Sensor name to be used within the Tenable Security Center logs. Note: The sensor name can be a maximum of 128 characters. |
|
IP Address |
The IP address of the configured client or syslog source. |
This section of the Advanced Configuration is used to further define how clients are able to connect to the Tenable Log Correlation Engine, and how they are named when viewed in the Event section of Tenable Security Center. The configurations are Public Server Address, Auto Authorize Clients, Use Client Network Address, and Override Sensor Name, described in the table below.
| Option | Description |
|---|---|
|
Public Server Address |
If the server is run from behind a device performing Network Address Translation (NAT), and the Tenable Log Correlation Engine clients that the server manages are on the public side of the device, the Public Server Address box must be set to the NAT address so that the managed clients can communicate with the server. The Tenable Log Correlation Engine server will listen for clients based on, in order of preference, the Public Server Address setting, the Server Address setting, or the first IP that it finds Tenable Log Correlation Engine using that is not 127.0.0.1. Caution: When a Public Server Address is specified, all clients on either side of the NAT device must use this address to connect. |
|
Auto Authorize Clients |
Specifies the number of minutes after the Tenable Log Correlation Engine server starts that clients will be automatically authorized. For example, if the value is set to 10, any clients that attempt to connect to the server within ten minutes of it starting will be automatically authorized. |
|
Use Client Network Address |
Override private client IP in events with the NAT / public network peer IP. |
|
Override Sensor Name |
Prefer configured name over discovered name. |
The Client Assignment Rules section allows for specific policies to be applied to specific client ranges. When a client assignment rule is created, a text box appears in the Policies column. In the text box, specify the filenames of the policies that you want applied to clients that fall in the range defined by the rule.
Policies are matched by operating system. If there are multiple policies for a particular operating system, the first applicable policy that is specified for that operating system will be assigned. If none of the specified policies are applicable to a client in the network, the default policy for that operating system will be used.
If Auto Authorize is enabled, clients that are discovered in the range defined by the rule will be automatically authorized.
| Option | Description |
|---|---|
|
Client Network |
A network range in CIDR notation |
|
Auto Authorize |
If enabled, clients discovered in the network range are automatically authorized. |
Users of the Tenable Log Correlation Engine server are tracked by their username. These options set restrictions on which usernames are considered valid. Any usernames failing to match the specified criteria are disregarded and the user is reported as invalid for the associated log entries.
| Option | Description |
|---|---|
|
User Tracking Plugins |
Only Plugin IDs in this list are used to apply user tracking. Other plugins will normalize usernames, but no tracking is performed based on the source and destination IP addresses. Only usernames normalized by these plugins are subject to the additional user tracking restrictions in this section. If a username is normalized by these plugins but does not meet the additional restrictions it will not be associated with the log and will not be associated with the subsequent logs from that IP address. Some IDs of plugins that can be specified for User Tracking Plugins are:
Note: Tenable Log Correlation Engine login-failure plugins do not normalize usernames because those logs are not assured to provide a valid username, and it would contaminate the username database. Additionally, it is advised never to add a login-failure plugin ID into the list of User Tracking Plugins. Doing so would invalidate user tracking for hosts that triggered the plugin. |
|
Accept Letters |
If enabled, the Tenable Log Correlation Engine server will allow usernames to contain letters. |
|
Accept Numbers |
If enabled, the Tenable Log Correlation Engine server will allow usernames to contain numbers. |
|
Valid Username Characters |
Specifies which special characters are considered valid for usernames. By default, the following characters are considered valid: For example, the following username would be considered valid based on the default value: b.j-smith@a_b.com Note: You cannot specify the semicolon character, “;” for this option. |
|
Max Username Length |
The maximum number of characters considered valid for usernames normalized by the server. |
|
Untracked Usernames |
These users are not tracked. The usernames are normalized and will appear with their associated logs, but no alert is generated when the username switches from one IP to another. Example:
|
Host Discovery and Vulnerabilities
This section defines the parameters used by Tenable Log Correlation Engine to send vulnerability information to Tenable Security Center, as described in the table below.
| Option | Description |
|---|---|
|
Enable Host Discovery |
This option enables or disables host discovery. When set to yes, new hosts on the network will be discovered and reported based on log data. |
|
Report Interval |
The interval, in minutes, in which the report file will be generated and updated on disk. The default is 60 minutes. |
|
Report Lifetime |
The lifetime of a report in days. The report will be cleared after this amount of time. The default is 7 days. |
|
Learning Period |
This option determines how many days a host has not been seen before an alert will be generated. A setting of at least 1 or 2 days is recommended. After that, any host that was not discovered during the period will be alerted on as new. Without this setting, Tenable Log Correlation Engine will repeatedly discover all of your hosts that are currently running, and not accurately identify hosts that are actually new. |
|
Reporter Port |
The port used by Tenable Security Center to retrieve host and vulnerability reports from Tenable Log Correlation Engine. |
|
Reporter Username |
The username used by both Tenable Security Center, and Tenable Log Correlation Engine to exchange vulnerability information. |
|
Reporter Password |
The password used by Tenable Security Center and Tenable Log Correlation Engine to exchange vulnerability information. |
|
Verify Reporter Password |
This field is used for password verification. |
Each statistical anomaly is triggered based on a number of deviations. There are multiple Statistical anomalies that can occur on a network. Some examples are Social Network, Login Failure, DNS, Virus, and Database anomalies. The Tenable Log Correlation Engine stats daemon can track these anomalies, and provide feedback when a specific threshold is reached.
Each statistical anomaly is triggered based on a number of deviations. The table below shows what number of standard deviations needs to occur before a statistical anomaly is triggered along with an example event name as it would be seen in the Events section of Tenable Security Center.
| Type | Minimum number of standard deviations from the mean | Maximum number of standard deviations from the mean | Example |
|---|---|---|---|
|
Minor Anomaly |
1.0 |
5.99 |
Statistics-Login_Minor_Anomaly |
|
Anomaly |
6.0 |
9.99 |
Statistics-USB_Anomaly |
|
Medium Anomaly |
10.0 |
99.99 |
Statistics-SPAM_Medium_Anomaly |
|
Large Anomaly |
100.00 |
999999.99 |
Statistics-Intrusion_Large_Anomaly |
| Option | Description |
|---|---|
|
Min Standard Deviation |
This specifies the minimum standard deviation that must occur for an event before an alert will be generated for it. The higher this number, the more statistically significant a sequence of events needs to be before an alert is raised. |
|
Min Number of Standard Deviations |
If an event occurs more or less than 5.0 standard deviation units, an alert will be generated. Setting this value higher will cut down on any sequence of events that occur close to the standard deviation. |
|
Min Statistical History |
This specifies the number of iterations (days) per-event are required before alerts will be generated. If a large amount of Tenable Log Correlation Engine data is already present, set this number to a low value or even to zero. The stats daemon can be started to read in all or just part of the existing Tenable Log Correlation Engine data. If you have no Tenable Log Correlation Engine data, leave this value around 7 so the stats daemon will not alert on anything until it has 7 days of event data. |
|
Max Occurrence Frequency |
If an event occurs more or less than 5.0 standard deviation units, an alert will be generated. Setting this value higher will cut down on any sequence of events that occur close to the standard deviation. |
|
Syslog Alerts |
The statistics engine will send anomaly alerts to the syslog servers in this list. It is recommended to include 127.0.0.1 for the local Tenable Log Correlation Engine service. |
Resource Usage and Performance
This section of the Tenable Log Correlation Engine Advanced Configuration is used to tune the performance of the Tenable Log Correlation Engine server.
| Option | Description |
|---|---|
|
Log Processors |
This option leverages multicore processors and determines how many threads will be dedicated to log processing.
It is recommended that this setting be no higher than the number of CPU cores in the Tenable Log Correlation Engine host system.
|
|
Sampleable TASLs |
Sampleable TASL scripts may be skipped to alleviate processor load when the TASL queue is full. |
When a log message is defined in a plugin, Tenable Log Correlation Engine provides the option to specify a hostname instead of an IP address for the srcip and dstip fields. In this case, Tenable Log Correlation Engine automatically attempts to resolve the provided hostname to an IP address using DNS. Since the same hostname is typically encountered multiple times, caching the results of lookups can greatly increase performance. These options configure DNS caching in Tenable Log Correlation Engine.
A particular hostname or all domain names with a certain extension can be excluded using the Always Resolve section. In this case, the matching hosts are looked up at every occurrence. The Always Resolve section can be used to maintain a more extensive list of domains to exclude when DNS caching is utilized. The host contained in the Always Resolve section of DNS Caching is read when Tenable Log Correlation Engine starts up, but changes to the list can be made at any time. If changes are made to the section the Update button at the bottom of the Advanced Configuration section of the Tenable Log Correlation Engine interface will need to be selected.
| Option | Description |
|---|---|
|
Max Memory for DNS Cache |
Tenable Log Correlation Engine will maintain a cache of hostname-to-IP addresses rather than performing the lookup repeatedly, limited to this amount of memory [MB]. The Max Memory for DNS Cache option can go up to 360K domain names. |
|
DNS Cache Period |
The DNS Cache Period option specifies the number of days to cache a hostname-to-IP mapping before updating the result with a new lookup. This value can be set between 1 and 30 days. |
|
Always Resolve |
If a host ends with an extension listed here, it will be resolved each time it is encountered rather than being cached. List each host or extension on a new line. A particular hostname or all domain names with a certain extension can be excluded using the Always Resolve section. In this case, the matching hosts are looked up at every occurrence. The Always Resolve section can be used to maintain a more extensive list of domains to exclude when DNS caching is utilized. The hosts contained in the Always Resolve section of DNS Caching are read when Tenable Log Correlation Engine starts up, but changes to the list can be made at any time. If changes are made to the section the Update button at the bottom of the Advanced Configuration section of the Tenable Log Correlation Engine interface will need to be selected. |
|
Cache at Startup |
Hosts listed in the Cache at Startup are resolved at startup and cached immediately to reduce runtime DNS resolutions and improve performance. The format for these entries is one hostname per line. |
Data Forwarding
See Data Forwarding.
TCP Syslog and Encrypted TCP Syslog
See Receiving Encrypted Syslog.
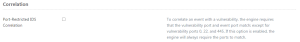
Tenable Log Correlation Engine normally matches the vulnerability port with the port given in the normalized event to correlate an event with vulnerability. If this option is disabled, Tenable Log Correlation Engine will ignore this requirement if the vulnerability port is 0, 22, or 445.
TASL and Plugins
See TASL and Plugins.
Event Rules
See Event Rules.