Benefits and Limitations
Agent scans and network scans each have their own benefits and limitations when discovering assets and analyzing vulnerabilities on your network.
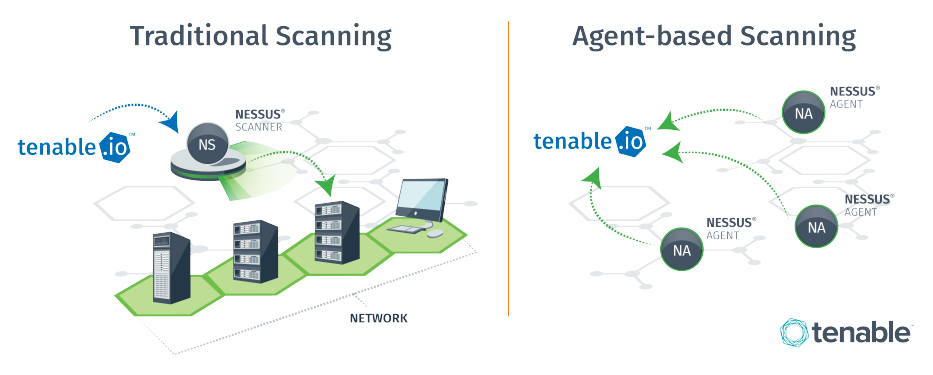
In a nutshell, network scans originate from a Tenable Nessus scanner that reaches out to the hosts targeted for scanning, while agent scans run on hosts regardless of network location or connectivity and then report the results back to the manager (for example, Tenable Nessus Manager or Tenable Vulnerability Management) when network connectivity resumes.
If network scanning is adequate for your environment and requirements, you may not need to use agents. However, for most organizations, Tenable recommends a combination of agents and network scanning to ensure full visibility into the entire network.
As you design the optimal scanning strategy for your organization's technology infrastructure, it is important to understand the differences between each scanning technology available to you. The following sections describe the benefits and limitations of each scanning method:
Non-credentialed Network Scans
A non-credentialed network scan, also known as an unauthenticated scan, is a common method for assessing the security of systems without system privileges. Non-credentialed scans enumerate a host's exposed ports, protocols, and services and identifies vulnerabilities and misconfigurations that could allow an attacker to compromise your network
Benefits
- Ideal for large-scale assessments in traditional enterprise environments.
- Discovers vulnerabilities that an outside attacker can use to compromise your network (provides a malicious adversary's point of view).
- Runs network-based plugins that an agent is restricted from performing.
- Can perform targeted operations like the brute forcing of credentials.
Limitations
- Can be disruptive; that is, can sometimes have a negative effect on the network, device, or application you are testing.
- Misses client-side vulnerabilities such as detailed patch information.
- Can miss transient devices that are not always connected to the network.
Credentialed Network Scans
A credentialed network scan, also known as an authenticated scan, provides a deeper insight than a non-credentialed scan. The scan uses credentials to log into systems and applications and can provide a definitive list of required patches and misconfigurations.
Because a credentialed scan looks directly at the installed software, including at the version numbers, it can assess items such as:
- Identifying vulnerabilities in the software.
- Evaluating password policies.
- Enumerating USB devices.
- Checking anti-virus software configurations.
It performs all these tasks with minimal to no impact on the device.
Benefits
- Consumes far fewer resources than non-credentialed scanning because the scan executes on hosts themselves rather than across the network.
- Non-disruptive; that is, does not have a negative effect on the network, device, or application you are testing.
- Provides more accurate results—a complete enumeration of software and patches installed on the host.
- Uncovers client-side software vulnerabilities.
Limitations
- Requires credentials management for each scanned host.
- Large organizations can potentially struggle with creating service accounts with the proper rights and access needed to safely conduct a credentialed scan.
- Password rotation requirements can add to management complexity.
Note:Tenable integrates with leading password vaults and password managers to alleviate this limitation for credentialed network scanning. - Misses transient devices that are not always connected to the network.
Agent Scans
Tenable Agent scans use lightweight, low-footprint programs that you install locally on hosts. Tenable Agents collect vulnerability, compliance, and system data, and report that information back to Tenable Nessus Manager or Tenable Vulnerability Management for analysis. Tenable Agents are designed to have minimal impact on the system and the network, giving you the benefit of direct access to all hosts without disrupting your end users.
Benefits
- Provides extended scan coverage and continuous security:
- Can deploy where it’s not practical or possible to run network-based scans.
- Can assess off-network assets and endpoints that intermittently connect to the internet (such as laptops). Tenable Agents can scan the devices regardless of network location and report results back to the manager.
- Eliminates the need for credential management:
- Doesn't require host credentials to run, so you don't need to update scan configuration credentials manually when credentials change, or share credentials among administrators, scanning teams, or organizations.
- Can deploy where remote credentialed access is undesirable, such as Domain Controllers, DMZs, or Certificate Authority (CA) networks.
- Efficient:
- Can reduce your overall network scanning overhead.
- Relies on local host resources, where performance overhead is minimal.
- Reduces network bandwidth need, which is important for remote facilities connected by slow networks.
- Removes the challenge of scanning systems over segmented or complex networks.
- Minimizes maintenance, because Tenable Agents can update automatically without a reboot or end-user interaction.
- Large-scale concurrent agent scans can run with little network impact.
- Easy deployment and installation:
- You can install and operate Tenable Agents on all major operating systems.
- You can install Tenable Agents anywhere, including transient endpoints like laptops.
- You can deploy Tenable Agents using software management systems such as Microsoft’s System Center Configuration Manager (SCCM).
Limitations
Agents are not designed to perform network checks, so certain plugins items cannot be checked or obtained if you deploy only agent scans. Combining network scans with agent-based scanning eliminates this gap.
- Agents miss things that can only be performed through remote connectivity, such as logging into a DB server, trying default credentials (brute force), or traffic-related enumeration.
-
In situations where the agent is not allowed sufficient time for plugin updates to finish before a scan (for example, if the agent host is turned off), the agent can run scans with a dated plugin set. This is because a scheduled scan can take priority over plugin updates if it has started before the plugin update completes.