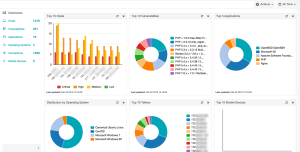
Monitoring Page
The Monitoring page provides a centralized view of vulnerabilities discovered by Tenable Nessus Network Monitor. On this page, vulnerabilities may be viewed in several categories, including Dashboards, Hosts, Vulnerabilities, Applications, Operating Systems, Connections, and Mobile Devices. The results may also be exported in different formats for use in other programs.
Across all of the viewable methods available on the Monitoring page, filter options are available to increase granularity when viewing results. Click the heading of a column to sort items within that section of the Monitoring page in ascending or descending order.
The Actions drop-down box allows you to export results, delete results, or launch a Tenable Nessus scan.
Note: After deleting results, you must restart Tenable Nessus Network Monitor to see the most up-to-date information.
The Filter <section name> box allows for quick filtering of the Monitoring page. To view a list of filterable plugin attributes, click the down arrow for any quick filter box. Results appear based on a match of Any or All filters. The search box contains example hints when empty, but if an incorrect filter value is introduced, the box displays a red border.
Note: The Filter <section name> box is not available in the Dashboards section.
Filter Text
|
Name |
Description |
|---|---|
|
Bugtraq ID |
Filter the results of discovered vulnerabilities based on their Bugtraq identifications. |
|
CPE |
Filter the results of discovered vulnerabilities based on their CPE identifiers. |
|
CVE |
Filter the results of discovered vulnerabilities based on their CVE identifiers. |
|
CVSS Base Score |
Filter the results of discovered vulnerabilities based on the base CVSS score as reported by vulnerability plugins. |
|
CVSS Temporal Score |
Filter the results of discovered vulnerabilities based on the temporal CVSS score as reported by vulnerability plugins. |
|
CVSS Temporal Vector |
Filter the results of discovered vulnerabilities based on the CVSS temporal vector as reported by vulnerability plugins. |
|
CVSS Vector |
Filter the results of discovered vulnerabilities based on the CVSS vector as reported by vulnerability plugins. |
|
CVSS v3.0 Base Score |
Filter the results of discovered vulnerabilities based on the CVSS v3.0 base score as reported by vulnerability plugins. |
|
CVSS v3.0 Temporal Score |
Filter the results of discovered vulnerabilities based on the temporal CVSS v3.0 score as reported by vulnerability plugins. |
|
CVSS v3.0 Temporal Vector |
Filter the results of discovered vulnerabilities based on the temporal CVSS v3.0 vector as reported by vulnerability plugins. |
|
CVSS v3.0 Vector |
Filter the results of discovered vulnerabilities based on the CVSS v3.0 vector as reported by vulnerability plugins. |
|
Host |
Filter the results of discovered vulnerabilities based on the discovered IP address of the device. |
|
IAVA ID |
Filter the results of discovered vulnerabilities based on the IAVA IDs of the vulnerabilities. |
|
IAVB ID |
Filter the results of discovered vulnerabilities based on the IAVB IDs of the vulnerabilities. |
|
IAVT ID |
Filter the results of discovered vulnerabilities based on the IAVT IDs of the vulnerabilities. |
|
OSVDB ID |
Filter the results of discovered vulnerabilities based on the discovered OSVDB identifiers. |
|
Plugin Description |
Filter the results of discovered vulnerabilities based on text available in the descriptions of the vulnerabilities. |
|
Plugin Family |
Filter the results of discovered vulnerabilities based on a family of discovered vulnerabilities. |
|
Plugin ID |
Filter the results of discovered vulnerabilities based on the IDs of the plugins that identified the vulnerabilities. |
|
Plugin Name |
Filter the results of discovered vulnerabilities based on text available in the names of the plugins that identified the vulnerabilities. |
|
Plugin Output |
Filter the results of discovered vulnerabilities based on text contained in the output of the plugin that discovered the vulnerability. |
|
Port |
Filter the results of discovered vulnerabilities based on the port on which the vulnerability was discovered. |
|
Protocol |
Filter the results of discovered vulnerabilities based on the detected protocol: tcp, udp, or icmp. |
|
STIG Severity |
Filter the results of discovered vulnerabilities based on STIG severity level of the plugin. |
|
See Also |
Filter the results of discovered vulnerabilities based on the text available in the See Also box of the plugin. |
|
Severity |
Filter the results of discovered vulnerabilities based on the identified severity. |
|
Solution |
Filter the results of discovered vulnerabilities based on text available in the solution section of the plugin. |
|
Synopsis |
Filter the results of discovered vulnerabilities based on text available in the synopsis section of the plugin. |
|
System Type |
Filter the results of discovered vulnerabilities based on the system type of the device. |
|
VLAN ID |
Filter the results of discovered vulnerabilities based on the VLAN ID of the device. |