Example Load Balancing Deployment
This section demonstrates an example of NNM running on two virtual machines functioning as NAT gateways within a Microsoft Azure Virtual Network using a Load Balancer. The NAT gateways also serve as the back end pool for the load balancer.
In the examples used in the instructions for setting up a NAT gateway with load balancing, the Virtual Network pvsVNet was created, which has the network range 10.240.0.0/16. Additionally, two virtual machine instances were created to function as NAT gateways. The NAT gateways provide a connection to the Internet for hosts behind the NAT. They also function as the backend pool for the load balancer. When a web request is made, the load balancer will distribute the traffic between the two NAT gateways. The NAT gateways have IP tables rules to forward the web request to the web server behind them.
In this example, there are four virtual machine instances within pvsVNet. The diagram shows two additional instances to indicate that normally there would be additional hosts behind the NAT:
| VM Instance Name | Internal IP | Has External IP? |
|---|---|---|
| pvsNatGateway | 10.240.0.4 | Yes |
| pvsNatGateway2 | 10.240.1.4 | Yes |
| Web server | 10.240.2.4 | No |
| Web server 2 | 10.240.3.4 | No |
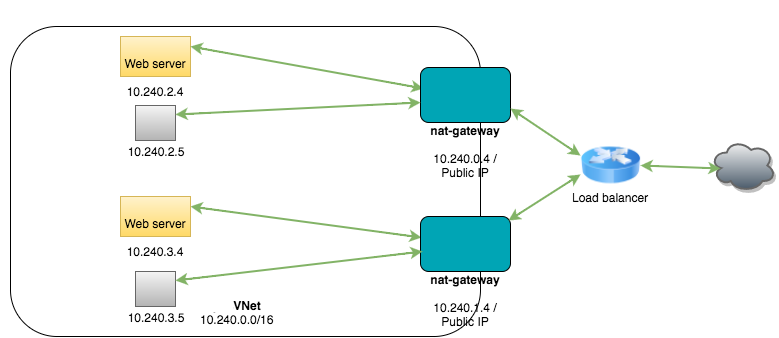
NNM is running on the NAT gateways at 10.240.0.4 and 10.240.1.4 and has the following configuration:
| Configuration Parameter | Value |
|---|---|
| Monitored Network Interfaces | eth0 |
| Monitored Network IP Addresses and Ranges | 10.240.0.0/16 |
With this configuration, NNM will monitor traffic
- from the internal virtual machine instances to the Internet,
- between the NAT gateway and the internal virtual machine instances,
- from the Internet to internal virtual machine instances if you have enabled port forwarding on the NAT gateway to make them Internet accessible,
-
and between the NAT gateway and the Internet.
Note: Azure policy prevents interfaces from operating in promiscuous mode. As a result, NNM can't monitor traffic between other virtual instances.