AUDIT_USER_TIMESTAMPS
This check queries for inactive accounts by looking at the user timestamps.
Usage
<custom_item>
type: AUDIT_USER_TIMESTAMPS
description: "Users not logged in past 7 or more days."
value_type: POLICY_DAY
value_data: "7"
timestamp: "LogonTime"
ignore_users: "Admin*,foo"
check_type: CHECK_GREATER_THAN_OR_EQUAL
</custom_item>
The keyword timestamp allows following values:
LogonTimeLogoffTimeKickoffTimePassLastSetPassCanChangePassMustChangeACB
Considerations:
- By default, accounts that are disabled, or those for which passwords cannot change or never expire are excluded from the result. They can be included as follows:
include_users: "password never expires" || "cannot change password" || "disabled" -
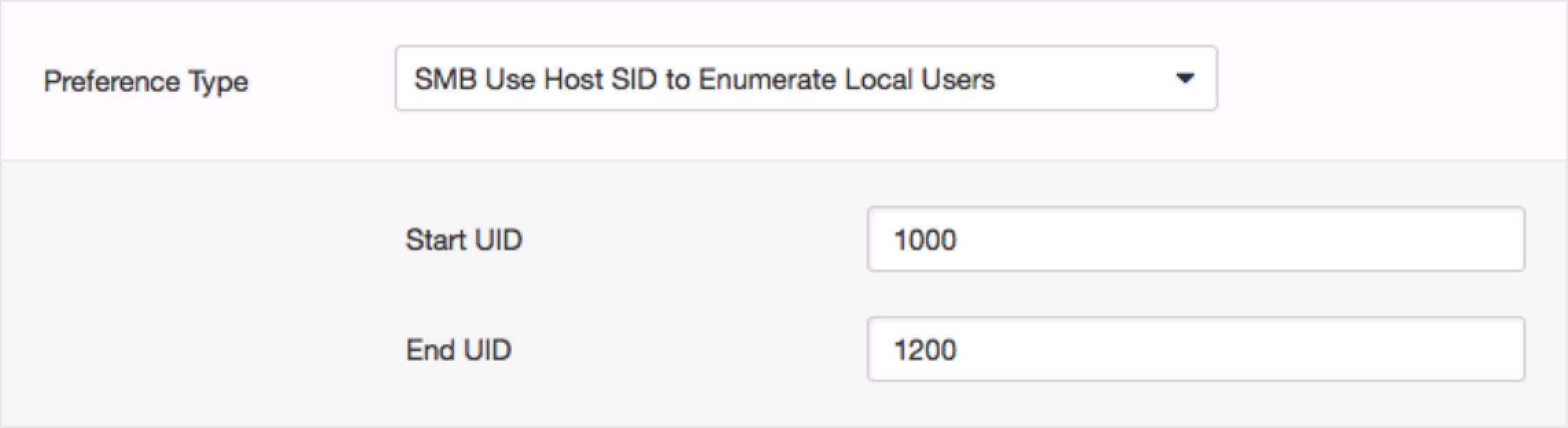
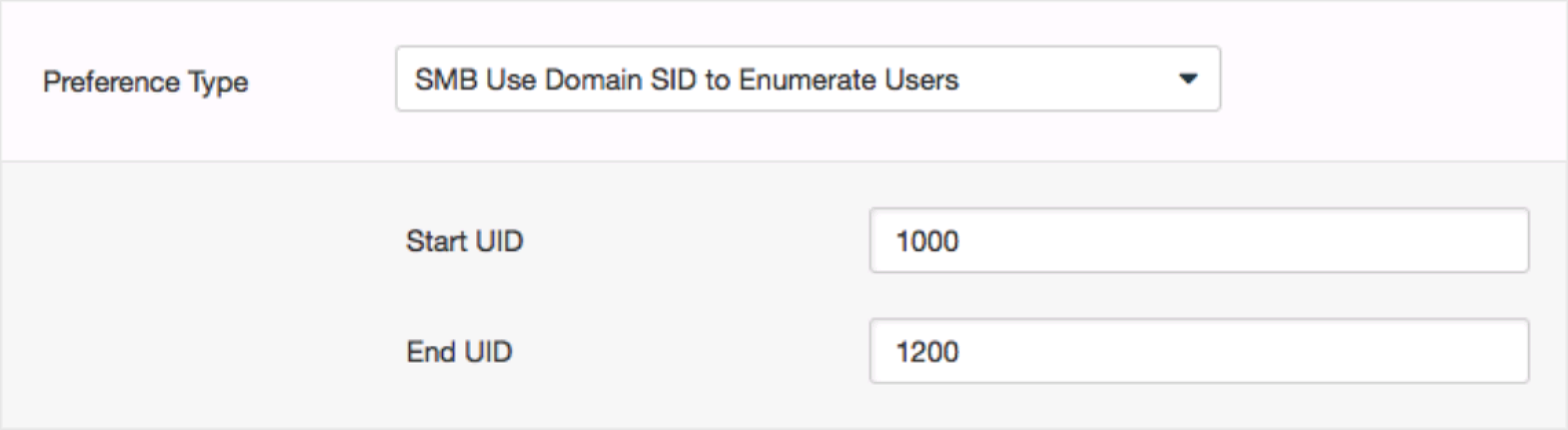
By default only those users with SID ranges within “SMB Use Host SID to Enumerate Local Users/SMB Use Domain SID to Enumerate Users” preference range.
Examples
The check also has the capability to exclude certain users from the result via the ignore_users directive:
<custom_item>
type: AUDIT_USER_TIMESTAMPS
description: "Password not changed in last 90 days"
value_type: POLICY_DAY
value_data: "90"
timestamp: "PassLastSet"
ignore_users: "Admin*,foo"
check_type: CHECK_GREATER_THAN_OR_EQUAL
</custom_item>