AUDIT_REPORTS
One of the nice features of a Palo Alto Firewall is that it continuously profiles its network, generating over 40 predefined reports on a daily basis. Reports such as Top Applications, Top Attackers, and Spyware Infected Hosts. Administrators can also generate dynamic reports at their discretion (e.g., the last-hour). Nessus can now directly query these reports, and include them in a Nessus report.
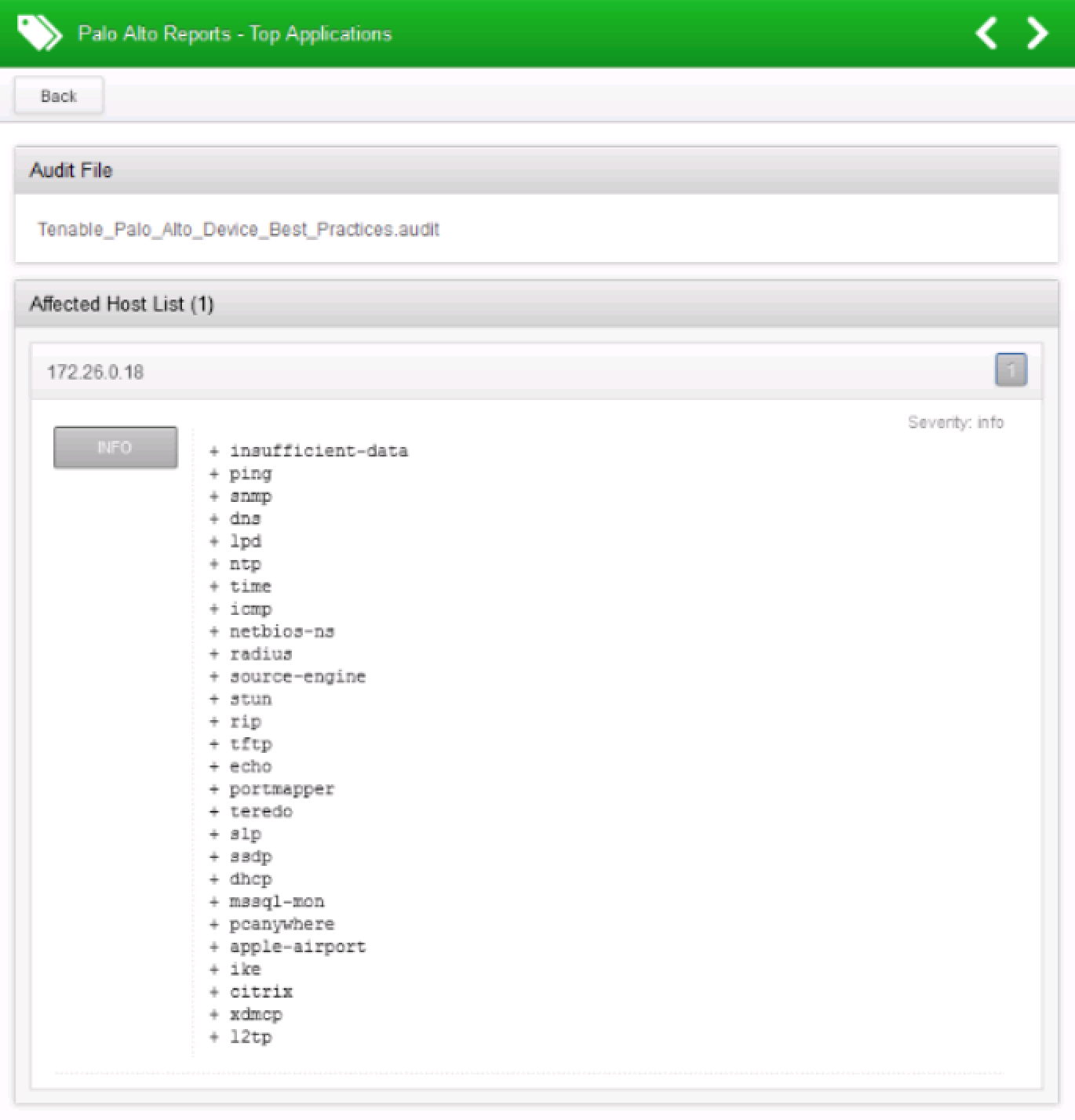
This feature has two benefits. First, users do not have to traverse different interfaces to get the same data. Second, this gives us the ability to audit the report. For example, if you do not want Facebook to be an application used within the network, then administrators can generate a failed report if Facebook shows up on the Top Applications report. For example:
<custom_item>
type: AUDIT_REPORTS
description: "Palo Alto Reports - Top Applications"
request: "&reporttype=predefined&reportname=top-applications"
xsl_stmt: "<xsl:template match=\"result\">"
xsl_stmt: "<xsl:for-each select=\"entry\">"
xsl_stmt: "+ <xsl:value-of select=\"name\"/>"
xsl_stmt: "</xsl:for-each>"
check_option: CAN_BE_NULL
</custom_item>
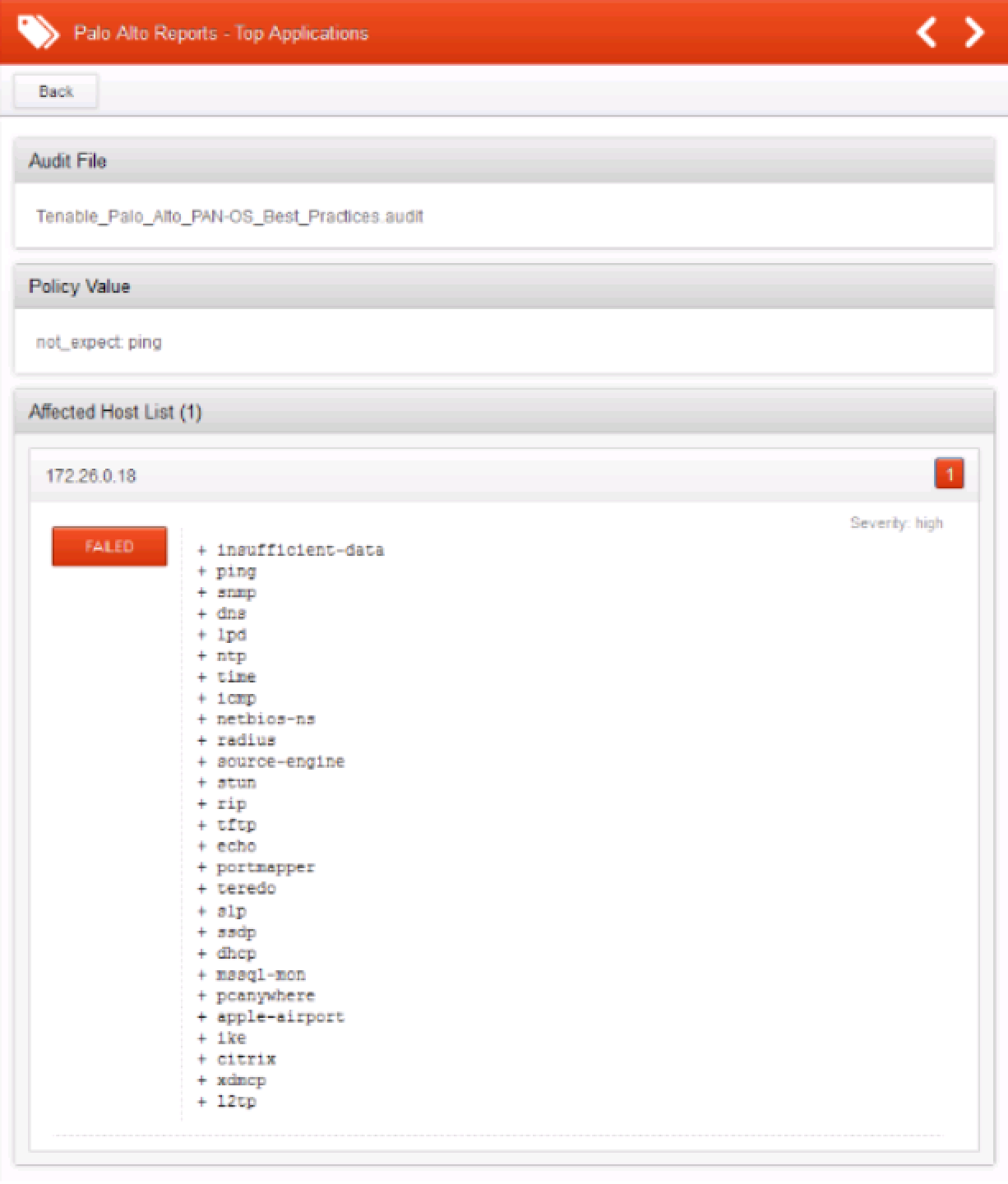
This report can be modified to use a not_expect keyword:
<custom_item>
type: AUDIT_REPORTS
description: "Palo Alto Reports - Top Applications"
request: "&reporttype=predefined&reportname=top-applications"
xsl_stmt: "<xsl:template match=\"result\">"
xsl_stmt: "<xsl:for-each select=\"entry\">"
xsl_stmt: "+ <xsl:value-of select=\"name\"/>"
xsl_stmt: "</xsl:for-each>"
not_expect: "ping"
check_option: CAN_BE_NULL
</custom_item>
The first example will return a report like this:
The second example will return a report that fails: