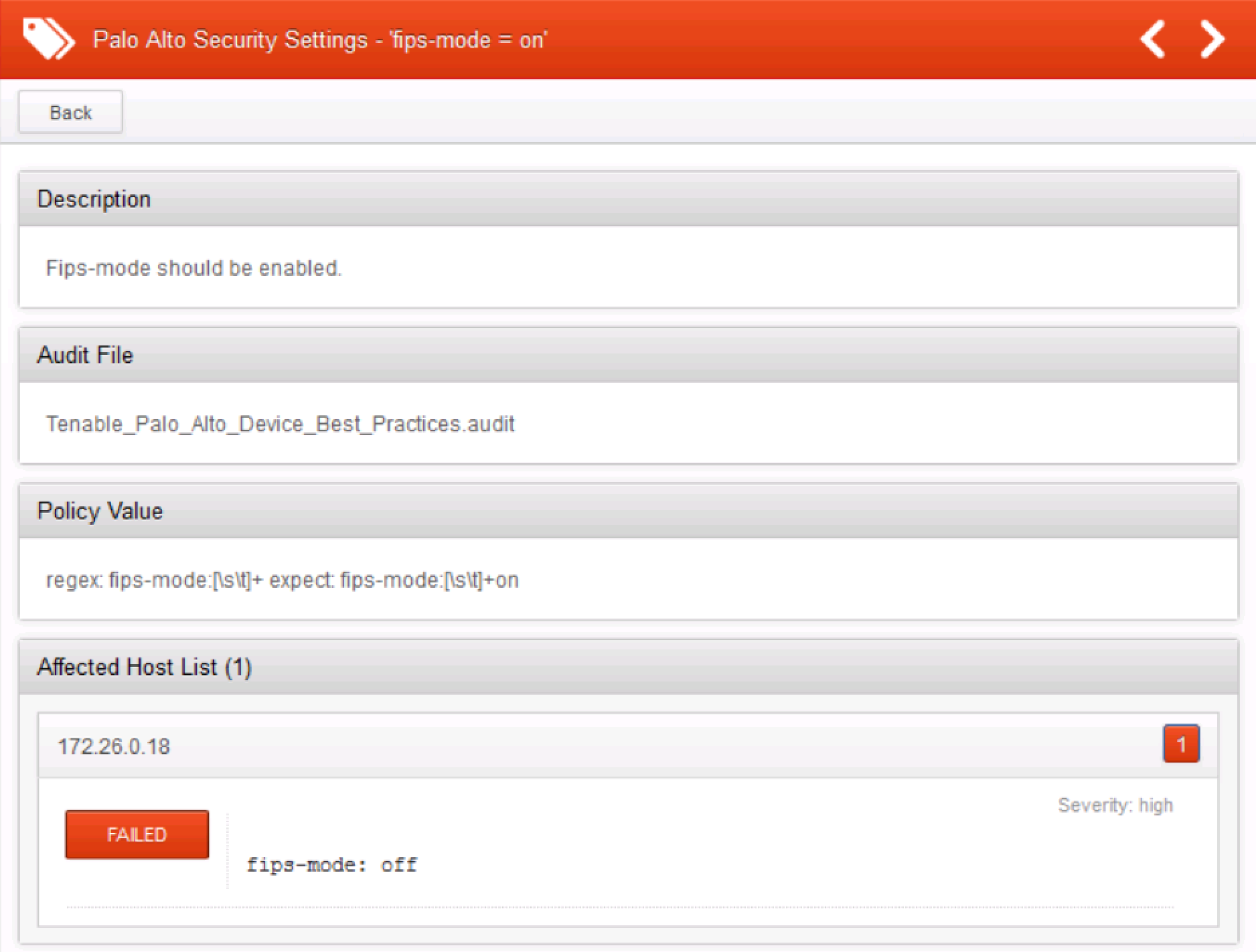
AUDIT_XML
The following is an example of a Palo Alto AUDIT_XML check:
<custom_item>
type: AUDIT_XML
description: "Palo Alto Security Settings - 'fips-mode = on'"
info: "Fips-mode should be enabled."
api_request_type: "op"
request: "<show><fips-mode></fips-mode></show>"
xsl_stmt: "<xsl:template match=\"/\">"
xsl_stmt: " <xsl:apply-templates select=\"//result\"/>"
xsl_stmt: "</xsl:template>"
xsl_stmt: "<xsl:template match=\"//result\">"
xsl_stmt: "fips-mode: <xsl:value-of select=\"text()\"/>"
regex: "fips-mode:[\\s\\t]+"
expect : "fips-mode:[\\s\\t]+on"
</custom_item>
There are four basic parts to this audit:
- The
typedescribes the type of audit (in this case it audits the XML) and a description of the audit. Theinfokeyword provides a way to include relevant text in the report. - The
api_request_typedescribes the type of request (op == operational config), and the request is the actual request we end up running. Currently, this is the only type of request supported. - The
xsl_stmtkeyword gives us a way to define the XSL Transform we are going to apply on the XML returned after running the API request. - Finally, the
regexandexpectkeywords allow us to do compliance/configuration auditing.
The example check above will generate the following report in Nessus: