Real-Time Plugin Examples
Failed Telnet Login Plugin
The easiest way to learn about Tenable Nessus Network Monitor real-time plugins is to evaluate some of those included by Tenable. Below is a plugin that detects a failed Telnet login to a FreeBSD server.
# Look for failed logins into an FreeBSD telnet server
id=79400
hs_sport=23
dependency=1903
realtimeonly
name=Failed login attempt
description=Tenable Nessus Network Monitor detected a failed login attempt to a telnet server
risk=LOW
match=Login incorrect
This plugin has many of the same features as a vulnerability plugin. The ID of the plugin is 79400. The high-speed port is 23. We need to be dependent on plugin 1903 (which detects a Telnet service). The realtimeonly keyword tells Tenable Nessus Network Monitor that if it observes this pattern, then it should alert on the activity, but not record any vulnerability.
In Tenable Security Center, events from Tenable Nessus Network Monitor are recorded alongside other IDS tools.
Finger User List Enumeration Plugin
The finger daemon is an older Internet protocol that allowed system users to query remote servers to get information about a user on that box. There have been several security holes in this protocol that allowed an attacker to elicit user and system information that could be useful to attackers.
id=79500
dependency=1277
hs_sport=79
track-session=10
realtimeonly
name=App Subversion - Successful finger query to multiple users
description=A response from a known finger daemon was observed which indicated that the attacker was able to retrieve a list of three or more valid user names.
risk=HIGH
match=Directory:
match=Directory:
match=Directory:
This plugin looks for these patterns only on systems where a working finger daemon has been identified (dependency #1277). However, the addition of the track-session keyword means that if this plugin is launched with a value of 10, the session data from the next 10 packets is tracked and logged in either the SYSLOG or real-time log file.
During a normal finger query, if only one valid user is queried, then only one home directory is returned. However, many of the exploits for finger involve querying for users such as NULL, .., or 0. This causes vulnerable finger daemons to return a listing of all users. In that case, this plugin would be activated because of the multiple “Directory:” matches.
Unix Password File Download Web Server Plugin
This plugin below looks for any download from a web server that does not look like HTML traffic, but does look like the contents of a generic Unix password file.
id=79300
dependency=1442
hs_sport=80
track-session=10
realtimeonly
name=Web Subversion - /etc/passwd file obtained
description=A file which looks like a Linux /etc/passwd file was downloaded from a web server.
risk=HIGH
match=!<HTML>
match=!<html>
match=^root:x:0:0:root:/root:/bin/bash
match=^bin:x:1:1:bin:
match=^daemon:x:2:2:daemon:
The plugin is dependent on Tenable Nessus Network Monitor ID 1442, which detects web servers. In the match statements, we attempt to ignore any traffic that contains valid HTML tags, but also has lines that start with common Unix password file entries.
Generic Buffer Overflow Detection on Windows Plugin
One of Tenable Nessus Network Monitor’s strongest intrusion detection features is its ability to recognize specific services, and then to look for traffic occurring on those services that should never occur unless they have been compromised. Since Tenable Nessus Network Monitor can keep track of both sides of a conversation and make decisions based on the content of each, it is ideal to look for Unix and Windows command shells occurring in services that should not have those command shells in them. Here is an example plugin:
# look for Windows error when a user tries to
# switch to a drive that doesn't exist
id=79201
include=services.inc
trigger-dependency
track-session=10
realtimeonly
name=Successful shell attack detected - Failed cd command
description=The results of an unsuccessful attempt to change drives on a Windows machine occurred in a TCP session normally used for a standard service. This may indicate a successful compromise of this service has occurred.
risk=HIGH
pmatch=!>GET
pregexi=cd
match=!>550
match=^The system cannot find the
match=specified.
This plugin uses the include keyword that identifies a file that lists several dozen Tenable Nessus Network Monitor IDs, which identify well known services such as HTTP, DNS, and NTP. The plugin is not evaluated unless the target host is running one of those services.
The keyword trigger-dependency is needed to ensure the plugin is evaluated even if there is only one match in the services.inc file. Otherwise, Tenable Nessus Network Monitor evaluates this plugin only if the target host was running all Tenable Nessus Network Monitor IDs present in the services.inc file. The trigger-dependency keyword says that at least one Tenable Nessus Network Monitor ID must be specified by one or more dependency or include rules must be present.
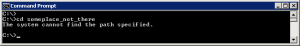
Finally, the logic of plugin detection looks for the following type of response on a Windows system:
In this case, a user has attempted to use the cd command to change directories within a file system and the attempt was not allowed. This is a common event that occurs when a remote hacker compromises a Windows 2000 or Windows 2003 server with a buffer overflow. The Tenable Nessus Network Monitor plugin looks for a network session that should not be there.
In the plugin logic, there are pmatch and pregexi statements that attempt to ensure that the session is not an HTTP session, and that the previous side of the session contains the string cd.
Tip: The pregexi statement could be expanded to include the trailing space after the “d” character and also the first character.
The plugin then looks for the expected results of the failed cd command. The first match statement makes sure this pattern is not part of the FTP protocol. Looking for “cd” in one side of a session and the error of attempting to change to a directory in an FTP session causes false positives for this plugin. Adding a rule to ignore if a line starts with “550” avoids this. While writing and testing this plugin, Tenable considered having a different set of plugins just for FTP, but the additional filter statement took care of any false positives. Finally, the last two match statements look for the results of the failed change directory attempt. They are spread across two match statements and could have been combined into one regular expression statement, but there was enough content in the basic message to split them into higher-speed matching.