Assets
Tenable Security Center assets are lists of devices (for example, laptops, servers, tablets, or phones) within a Tenable Security Center organization. Assets can be shared with one or more users based on local security policy requirements.
You can add an asset to group devices that share common attributes. Then, you can use the asset during scan configuration to target the devices in the asset. Examples of common attributes include:
-
IP address ranges
-
hardware types
-
vulnerabilities
-
outdated software versions
-
operating systems
Tenable Security Center supports template-based and custom assets. For more information, see Add a Template-Based Asset and Add a Custom Asset. To view details for any of your assets, see View Asset Details.
To view details about individual hosts that appear in your assets, see
Note: When a scan import completes, it queues a job to calculate all dynamic and combination assets for the import repository. The next scan import does not begin until the previous scan import asset job completes. Usually the asset job runs quickly, but delays can occur due to extremely large repositories, a large quantity of assets, a backlogged job queue, or other system issues. This does not affect running scans.
Asset lists are calculated for each repository, and updating one repository does not affect other repositories.
Tenable provides asset templates that you can customize for your environment. Tenable-provided asset templates are updated via the Tenable Security Center feed and visible depending on other configurations.
Tenable Security Center supports the following custom assets types: Static assets are lists of IP addresses. You can use static assets immediately after configuration., Option,
Static assets are lists of IP addresses. You can use static assets immediately after configuration.
For example, if your organization assigns laptops within a defined IP address range, you can create a custom static asset for laptops using that IP address range.
|
Option |
Description |
|---|---|
|
Name |
A name for the asset. |
|
Description |
A description for the asset. |
|
Tag |
A tag for the asset. For more information, see Tags. |
|
IP Addresses |
IP addresses to include within the asset (
|
Note: You cannot select an LDAP query asset as the target of an agent scan or an agent synchronization job.
The LDAP query asset type appears if your organization includes a configured LDAP server.
|
Option |
Description |
|---|---|
|
Name |
A name for the asset. |
|
Description |
A description for the asset. |
|
LDAP Server |
The LDAP server where you want to perform the query. Note: If the LDAP server uses a different DNS server than Tenable Security Center, Tenable Security Center cannot resolve hostnames retrieved from the LDAP server. Note:Tenable Security Center cannot retrieve more than one page of LDAP results. If Tenable Security Center asset or user authentication queries are not retrieving all expected results, consider modifying your LDAP pagination control settings to increase the results per page. |
|
Search Base |
The LDAP search base used as the starting point to search for specific LDAP data. |
|
Search String |
Modify this string to create a search based on a location or filter other than the default search base or attribute. |
|
Generate Preview |
Click to display a preview query in the Results Preview section. The preview lists the LDAP data that matches the defined search string. |
Combination assets allow you to create an asset based on existing assets and the AND, OR, and NOT operators.
Combination assets can include agent IDs if the asset contains exclusively dynamic assets. You may experience unexpected asset behavior if your combination asset contains other asset types and interacts with agent repository data.
|
Option |
Description |
|---|---|
|
Name |
A name for the asset. |
|
Description |
A description for the asset. |
|
Combination |
This option accepts multiple existing assets utilizing the operators AND, OR, and NOT. You can use these operators and multiple existing assets to create new unique assets. If the source assets change, the Combination asset updates to match the new conditions. To configure the query:
Tip: A red border around a combination option indicates there is a problem in the query logic. |
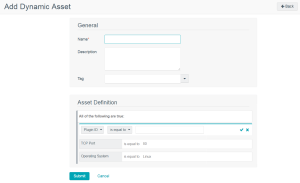
Dynamic assets are flexible groups of condition statements that Tenable Security Center uses to retrieve a list of devices meeting the conditions. Tenable Security Center refreshes dynamic asset lists using the results from Tenable Security Center scans. You cannot use dynamic assets until after Tenable Security Center performs an initial discovery scan and retrieves a list of devices.
Note: Before a scan can target a dynamic asset list, you must first run a host discovery scan in the associated repository. For more information, see the troubleshooting article.
Dynamic assets can include agent IDs.
For example, in the asset above, Tenable Security Center retrieves a list of Linux systems listening on TCP Port 80. For more information about using dynamic asset conditions, see Dynamic assets are flexible groups of condition statements that Tenable Security Center uses to retrieve a list of devices meeting the conditions. Tenable Security Center refreshes dynamic asset lists using the results from Tenable Security Center scans. You cannot use dynamic assets until after Tenable Security Center performs an initial discovery scan and retrieves a list of devices..
|
Option |
Description |
|---|---|
|
Name |
A name for the asset. |
|
Description |
A description for the asset. |
|
Asset Definition |
Defines the rules for creating a dynamic asset list. Hover over an existing rule to display the options to add, edit, or delete a group or a rule. |
Dynamic Asset Rule Logic
|
Valid Operators |
Effect |
|---|---|
|
Plugin ID |
|
|
is equal to |
Value must be equal to value specified. |
|
not equal to |
Value must be not equal to value specified. |
|
is less than |
Value must be less than the value specified. |
|
is greater than |
Value must be greater than the value specified. |
|
Plugin Text |
|
|
is equal to |
Value must be equal to value specified. |
|
not equal to |
Value must be not equal to value specified. |
|
contains the pattern |
Value must contain the text specified (for example, ABCDEF contains ABC). |
|
Posix regex |
Any valid Posix regex pattern contained within “/” and “/” (example: /.*ABC.*/). |
|
Perl compatible regex |
Any valid Perl compatible regex pattern. |
|
Operating System |
|
|
is equal to |
Value must be equal to value specified. |
|
not equal to |
Value must be not equal to value specified. |
|
contains the pattern |
Value must contain the text specified (for example, ABCDEF contains ABC). |
|
Posix regex |
Any valid Posix regex pattern contained within “/” and “/” (for example, /.*ABC.*/). |
|
Perl compatible regex |
Any valid Perl compatible regex pattern. |
|
IP Address |
|
|
is equal to |
Value must be equal to value specified. |
|
not equal to |
Value must be not equal to value specified. |
|
DNS, NetBIOS Host, NetBIOS Workgroup, MAC, SSH v1 Fingerprint, SSH v2 Fingerprint |
|
|
is equal to |
Value must be equal to value specified. |
|
not equal to |
Value must be not equal to value specified. |
|
contains the pattern |
Value must contain the text specified (for example, 1.2.3.124 contains 124). |
|
Posix regex |
Any valid Posix regex pattern contained within “/” and “/” (for example, /.*ABC.*/). |
|
Perl compatible regex |
Any valid Perl compatible regex pattern. |
|
Port, TCP Port, UDP Port |
|
|
is equal to |
Value must be equal to value specified. |
|
not equal to |
Value must be not equal to value specified. |
|
is less than |
Value is less than value specified. |
|
is greater than |
Value is greater than the value specified. |
|
Days Since Discovery, Days Since Observation |
|
|
is equal to |
Value must be equal to value specified (maximum 365). |
|
not equal to |
Value must be not equal to value specified (maximum 365). |
|
is less than |
Value is less than value specified (maximum 365). |
|
is greater than |
Value is greater than the value specified (maximum 365). |
|
where Plugin ID is |
Any valid plugin ID number. You can enter multiple plugin IDs using a range or comma-separated plugin IDs (for example, 3, 10189, 34598, 50000-55000, 800001-800055). |
|
Severity |
|
|
is equal to |
Value must be equal to value specified: Info, Low, Medium, High, or Critical. |
|
not equal to |
Value must be not equal to value specified: Info, Low, Medium, High, or Critical. |
|
is less than |
Value must be less than the value specified: Info, Low, Medium, High, or Critical. |
|
is greater than |
Value must be greater than the value specified: Info, Low, Medium, High, or Critical. |
|
where Plugin ID is |
Any valid plugin ID number. You can enter multiple plugin IDs using a range or comma-separated plugin IDs (for example, 3, 10189, 34598, 50000-55000, 800001-800055). |
|
Exploit Available |
|
|
Is |
Click True or False in the drop-down box. |
|
Exploit Frameworks |
|
|
is equal to |
Value must be equal to value specified. |
|
Is not equal to |
Value must not be equal to value specified. |
|
contains the pattern |
Value must contain the pattern entered. |
|
XRef |
|
|
Value must be in the XRef option. |
|
You can use a watchlist asset to maintain lists of IPs that are not in the user’s managed range of IP addresses. You can filter for IPs from a watchlist regardless of your IP address range configuration to help analyze event activity originating outside of the user’s managed range. For example, if a block of IP addresses is a known source of malicious activity, you could add it to a Malicious IPs watchlist and added to a custom query.
Note: Watchlists only use event data to create the asset list.
|
Option |
Description |
|---|---|
|
Name |
A name for the asset. |
|
Description |
A description for the asset. |
|
IP Addresses |
IP addresses to include within the asset list (20,000 character limit). You can enter one address, CIDR address, or range per line. Click Choose File to import a list of IP addresses from a saved file. |