CIS Control 10: Data Recovery Capabilities
The focus of this control is to ensure that the processes and tools used to properly back up critical information are in place within the organization and a proven methodology for timely recovery of data exists.
The CIS states this Control is critical:
“When attackers compromise machines, they often make significant changes to configurations and software. Sometimes attackers also make subtle alterations of data stored on compromised machines, potentially jeopardizing organizational effectiveness with polluted information. When the attackers are discovered, it can be extremely difficult for organizations without a trustworthy data recovery capability to remove all aspects of the attacker’s presence on the machine.”
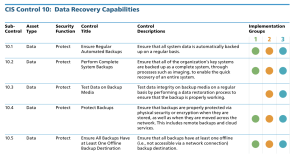
The journey of implementing the CIS Controls continues with data recovery capabilities. This control addresses the importance of backing-up and protecting an organization's system data. Organizations which implement sound data backup strategies ensure their ability to recover lost data or data that has been tampered-with quickly and efficiently. Properly archiving key system data, periodic integrity testing, and having at least one offline backup destination are all crucial in restoring systems and resuming service with the least amount of downtime. This control helps to guide the organization through this review process. The four specific sub-controls that are part of Implementation Group 1 (IG1) are:
-
10.1: Ensure Regular Automated Backups
-
10.2: Perform Complete System Backups
-
10.4: Protect Backups
-
10.5: Ensure All Backups Have at Least One Offline Backup Destination
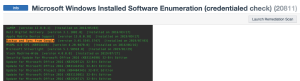
The organization should take their time during this process, being sure to review all the back-up policies and conduct integrity tests on randomly selected backups, at random intervals. Tenable Security Center can assist in some areas as there are many active plugins such as 20175 Veritas Backup Agent Detection, and passive detections such as 6575 Carbonite 'Cloud' Backup Service User-Agent Detection that can assist in determining if back-up software/services are detected. Using previous methods, plugin 20811 Windows Software Enumeration can be used to determine if any backup client is installed on endpoints. However, most of the work within this CIS control comes from testing and validation tasks.
As shown above, using Nessus plugin 20811 to enumerate installed software on an endpoint, we are able to determine that a cloud backup solution is installed. However, you must manually test and validate the process.