Preface on Sub-Control 11.4
Tenable Security Center provides innovative ways to find vulnerabilities for network devices using different attributes, such as the Common Platform Enumeration (CPE). Tenable Security Center uses CPE strings “bluecoat, brocade, check_point, checkpoint, cisco, citrix, dell, f5, fortinet, hp, huawei, juniper, netapp, netgear, paloaltonetworks, pfsense, sonicwall, ssh, veritas, vmware, websense” to locate vulnerabilities that are likely related to network devices. These vulnerabilities help support CIS sub control 11.4: Install the Latest Stable Version of Any Security Related Updates on All Network Devices. Components include trend lines which are calculated over 3 months, and that use the Last Observed Filter set to “Within the Last Day”. This allows analysts to track changes from one day to the next, showing a more accurate change. If scans are run weekly, then a user should modify the field to 7 days, so the change from scan to scan is accurately measured.
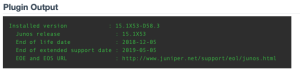
The ultimate goal of this sub-control is to have a score (or ratio) of zero (The number of network devices all have up to date software versions, i.e., there are no missing patches/updates). Using this method, we can easily identify unsupported versions of software on network devices. The following example from pluginID 55933 Juniper Junos Unsupported Version Detection uses the above listed filters as a base query.