CIS Control 8: Malware Defenses
The focus of this control is to control the installation, spread, and execution of malicious code at multiple points in the enterprise, while optimizing the use of automation to enable rapid updating of defense, data gathering, and corrective action.
The CIS states this Control is critical:
“Malicious software is an integral and dangerous aspect of Internet threats, as it is designed to attack your systems, devices, and your data. It is fast-moving, fast-changing, and enters through any number of points like end-user devices, email attachments, web pages, cloud services, user actions, and removable media. Modern malware is designed to avoid defenses, and attack or disable them. Malware defenses must be able to operate in this dynamic environment through large-scale automation, rapid updating, and integration with processes like incident response. They must also be deployed at multiple possible points of attack to detect, stop the movement of, or control the execution of malicious software. Enterprise endpoint security suites provide administrative features to verify that all defenses are active and current on every managed system.”
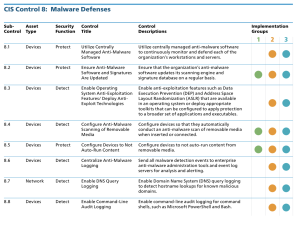
The journey of implementing the Foundational CIS Controls continues with CIS Control 8 Malware Defenses. Organizations are directed to ensure that the scanning engine and signature database are updated on a regular basis for all anti-malware software. Ideally, only the latest version should be used. Organizations are also directed to configure devices so that they automatically conduct an anti-malware scan of removable media when inserted or connected. Finally, as part of the IG1 set of controls, organizations are advised to configure devices to not auto-run content from removable media. The specific sub-controls that are part of Implementation Group 1 (IG1) are:
-
8.2 Ensure Anti-Malware Software and Signatures are Updated
-
8.4 Configure Anti-Malware Scanning of Removable Media
-
8.5 Configure Devices to Not Auto-Run Content