Indicators of Attack Deployment
Tenable Identity Exposure 's Indicators of Attack (IoA) give you the ability to detect attacks on your Active Directory (AD). Each IoA requires specific audit policies that the installation script automatically enables. For a complete list of Tenable Identity Exposure IoAs and their implementation, see the Tenable Identity Exposure Indicators of Attack Reference Guide in the Tenable downloads portal.
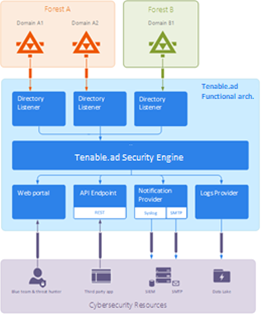
Tenable Identity Exposure works as a non-intrusive solution that monitors an Active Directory infrastructure without deploying agents and with minimal configuration change in your environment.
Tenable Identity Exposure uses a regular user account with no administrative permissions to connect to standard APIs for its security monitoring feature.
Tenable Identity Exposure uses the Active Directory replication mechanisms to retrieve the relevant information, which incurs only limited bandwidth costs between each domain’s PDC and Tenable Identity Exposure’s Directory Listener.
To detect efficiently security incidents using indicators of attack, Tenable Identity Exposure uses the Event Tracing for Windows (ETW) information and the replication mechanisms available on each Domain Controller. To collect this set of information, you deploy a dedicated Group Policy Object (GPO) using a script from Tenable Identity Exposure as described in Install Indicators of Attack.
This GPO activates an event logs listener using Windows EvtSubscribe APIs on all domain controllers which writes to the system volume (SYSVOL) to benefit from the AD replication engine and Tenable Identity Exposure’s ability to listen to SYSVOL events. The GPO creates a file in SYSVOL for each domain controller and flushes its contents periodically.
To initiate security monitoring, Tenable Identity Exposure must contact standard directory APIs from Microsoft.
Domain Controller
Tenable Identity Exposure only requires communication with the Primary Domain Controller emulator (PDCe) using the network protocols described in the Network Flow Matrix.
In the case of multiple monitored domains or forests, Tenable Identity Exposure must reach each domain's PDCe. For best performance, Tenable recommends that you host Tenable Identity Exposure on a physical network close to the PDCe to monitor.
User Account
Tenable Identity Exposure authenticates to the monitored infrastructure using a non-administrator user account to access the replication flow.
A simple Tenable Identity Exposure user can access all collected data. Tenable Identity Exposure does not access secret attributes such as credentials, password hashes, or Kerberos keys.
Tenable recommends that you create a service account that is a member of the group “Domain Users” as follows:
-
The service account is on the main monitored domain.
-
The service account is in any Organizational Unit (OU), preferably where you create other security service accounts.
-
The service account has standard user group membership (such as member of the Domain Users AD default group).
-
Review the limitations and potential impacts of installing IoAs, as described in Technical Changes and Potential Impact.
-
Check that the DC has the PowerShell modules for Active Directory and GroupPolicy installed and available.
-
Check that the DC has the Distributed File System Tools feature RSAT-DFS-Mgmt-Con enabled so that the deployment script can check for replication status because it cannot create a GPO while the DC is replicating.
-
Tenable Identity Exposure recommends that you install/upgrade IoAs during off-peak hours to limit disruptions to your platform.
-
Check permissions — To install IoAs, you must have a user role with the following permissions:
-
In Data Entities, "Read" access for:
-
All Indicators of Attack
-
All domains
-
-
In Interface Entities, access for:
-
Management > System > Configuration
-
Management > System > Configuration > Application Services > Indicators of Attack
-
Management > System > Configuration > Application Services > Indicators of Attack > Download installation file
-
-
For more information about role-based permissions, see Set Permissions for a Role.
See also
- Indicators of Attack Installation Script
- Technical Changes and Potential Impact
-
Install Microsoft Sysmon, a Windows system tool that some of Tenable Identity Exposure’s indicators of attack require to get relevant system data.