Install Indicators of Attack
Tenable Identity Exposure's Indicators of Attack (IoA) module requires you to run a PowerShell installation script with an administrative account that can create and link a new Group Policy Object (GPO) to an organizational unit (OU). You can run this script from any machine joined to your Active Directory domain that Tenable Identity Exposure monitors and that can reach domain controllers via the network.
You only have to execute this installation script once for each AD domain, since the GPO created automatically deploys the event listener to all existing and new domain controllers (DCs).
Moreover, enabling the "Automatic Updates" option avoids having to re-execute the installation script, even if you change the IoA configuration.
-
In Tenable Identity Exposure, click System on the left menu bar and the Configuration tab.
The Configuration pane appears.
-
Click Indicators of Attack.
The IoA configuration pane appears.
-
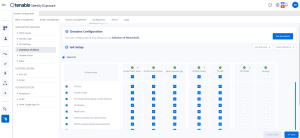
In (1) Domains Configuration, click See Procedure.
A procedure window opens.
-
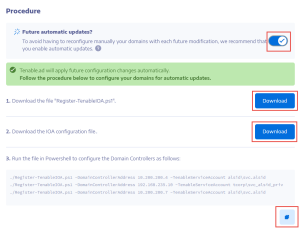
Under Future automatic updates?:
-
The default option Enable allows Tenable Identity Exposure to update automatically your IoA configuration whenever you modify it in Tenable Identity Exposure in the future. This also ensures continuous security analysis.
-
If you turn off this option, a message asks you to turn it on to get automatic future updates. Click See procedure and toggle to Enable.
-
-
Click Download to download the script to run for each domain (Register-TenableIOA.ps1).
-
Click Download to download the configuration file for the domains (TadIoaConfig-AllDomains.json).
-
Click
 to copy the Powershell command to configure your domains.
to copy the Powershell command to configure your domains.
-
Click outside the procedure window to close it.
-
Open a PowerShell terminal with administrative rights and run the commands to configure your domain controllers for IoAs.
Note: The service account you use to install IoAs and to query the domains must have write permissions in Tenable Identity Exposure (formerly known as Tenable.ad) GPO folder. The installation script adds this permission automatically. If you remove this permission, Tenable Identity Exposure shows an error message and automatic updates no longer work. For more information, see Indicators of Attack Installation Script.
-
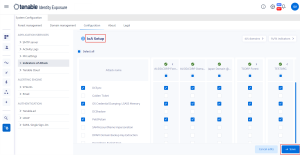
In the IoA configuration pane, under IoA Setup, select the IoAs you want in your configuration.
Tip: The Zerologon Exploitation Indicator of Attack (IoA) dates from 2020. If all of your domain controllers (DCs) received updates within the past three years, they are protected from this vulnerability. To determine the required patches for securing your DCs against this vulnerability, consult the information in Netlogon Elevation of Privilege Vulnerability from Microsoft. Once you've confirmed your DCs' security, you can safely deactivate this IoA to avoid unnecessary alerts. -
Click Save.
-
If you enabled Future automatic updates, Tenable Identity Exposure saves and automatically updates your new configuration. Allow a few minutes for this update to take effect.
-
If you did not enable Future automatic updates, a procedure window appears to guide you To configure domains for IoAs:
-
-
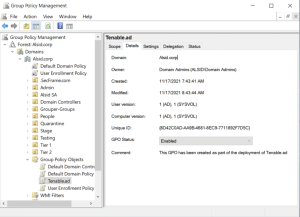
In the file manager, go to \\<DNS-NAME>\sysvol\<DNS-NAME>\Policies\{<GPO-ID>}\Machine\.
-
Right-click on the "IOA" folder and select Properties.
-
Select the Security tab and click Advanced.
-
Click the Effective Access tab.
-
Click Select a user.
-
Type <TENABLE-SERVICE-ACCOUNT-NAME> and click OK.
-
Click on View effective access.
-
Check that the "Write" permission is activated.
Alternately, you can use Powershell:
-
Run the following commands:
CopyInstall-Module -Name NTFSSecurity -RequiredVersion 4.2.3
CopyGet-NTFSEffectiveAccess -Path \\<DNS-NAME>\sysvol\<DNS-NAME>\Policies\{<GPO-ID>}\IOA\ -Account <TENABLE-SERVICE-ACCOUNT-NAME>
To avoid false positive attacks or lack of detection of legitimate attacks, you must calibrate your IoAs according to your environment by adapting them to the size of your Active Directory, whitelisting known tools, etc.
-
See the Tenable Identity Exposure Indicators of Attack Reference Guide for information about the options and recommended values to select.
-
In the security profile, apply the options and values to each IoA as described in Customize an Indicator.
The following error messages can appear during the deployment:
| Message | Remediation |
|---|---|
| "Tenable Identity Exposure cannot write to the configuration file because the target folder <targetFolder> does not exist. This indicates that the IoA module deployment may have failed." | Uninstall the script and click "See procedure" for instructions to re-install the script. |
| "Tenable Identity Exposure could not write to the configuration file located on <targetFile> to update it. This can be due to another process locking the file or permission changes." |
|
| "The target folder <targetFolder> contains a version of Tenable Identity Exposure that cannot run automatic updates." | The currently installed script is an old version using WMI. Uninstall the current version, download a new installation script, and run this script. |
| "The configuration file deployment ran into an unexpected error." | Uninstall the script and click "See procedure" for instructions to re-install the script. If this does not work, contact your customer support representative. |
For more information, see: