Assets
The following feature is only available in Tenable FedRAMP Moderate environments.
The Assets page provides insight into your organization's assets and their vulnerabilities.
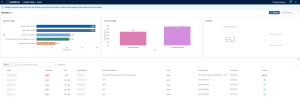
This page contains top-level widgets that provide a snapshot of the asset scanning status, and a table that lists assets scans have identified in your network. The top-level widgets include:
| Widget | Description |
|---|---|
| Asset by Tags | This widget lists the top 5 tags applied to the highest number of assets. For more information, see Tags. |
| Asset Coverage |
This widget summarizes how thoroughly your scans assessed your environment during the past 90 days.
For more information, see Discovery Scans vs. Assessment Scans. |
| Statistics | This widget summarizes any licensed asset (in that Tenable Vulnerability Management scanned the asset in the last 90 days). |
For more information, see the following topics:
About Assets
Tenable Vulnerability Management includes the ability to track assets that belong to your organization. Assets are entities of value on a network that can be exploited. This includes laptops, desktops, servers, routers, mobile phones, virtual machines, software containers, and cloud instances. By providing comprehensive information about the assets that belong to your organization, Tenable Vulnerability Management helps to eliminate potential security risks, identify under-utilized resources, and support compliance efforts.
Tenable Vulnerability Management automatically creates or updates assets when a scan completes or scan results are imported. Tenable Vulnerability Management attempts to match incoming scan data to existing assets using a complex algorithm. This algorithm looks at attributes of the scanned hosts and employs various heuristics to choose the best possible match. If Tenable Vulnerability Management cannot find a match, the system assumes this is the first time Tenable Vulnerability Management has encountered the asset and creates a new record for it. Otherwise, if Tenable Vulnerability Management finds a matching asset, the system updates any properties that have changed since the last time Tenable Vulnerability Management encountered the asset.
In addition to vulnerability information, Tenable Vulnerability Management also attempts to gather various other information about the asset, including:
- Interfaces (IP address and MAC address)
- DNS Names
- NetBIOS Name
- Operating System
- Installed Software
- UUIDS (Tenable, ePO, BIOS)
- Whether an agent is present