CIS Control 1: Inventory and Control of Hardware Assets
Control 1 helps the CIS to actively manage (inventory, track, and correct) all hardware devices on the network. This ensures only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.
“Attackers, who can be located anywhere in the world, are continuously scanning the address space of target organizations, waiting for new and possibly unprotected systems to be attached to the network. They are particularly interested in devices which come and go off of the enterprise’s network such as laptops or Bring-Your-Own-Device (BYOD) which might be out of synchronization with security updates or might already be compromised. Attacks can take advantage of new hardware that is installed on the network one evening but not configured and patched with appropriate security updates until the following day. Even devices that are not visible from the Internet can be used by attackers who have already gained internal access and are hunting for internal pivot points or victims. Additional systems that connect to the enterprise’s network (e.g., demonstration systems, temporary test systems, guest networks) should also be managed carefully and/or isolated in order to prevent adversarial access from affecting the security of enterprise operations.”
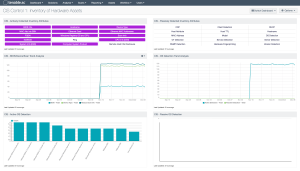
Any journey begins with single step, and the journey of implementing the CIS Controls begins with inventory of hardware assets. A hardware asset is any device that operates at the Datalink layer (Layer 2) or the Network layer (Layer 3). These devices, whether they are connected to the network or not, can store or provide access to sensitive data. Therefore, their risk must be identified. By discovering assets within the organization, the CISO can begin to establish an inventory and can then begin assessing and mitigating associated risks to the asset. To accomplish this, though, our first priority is to discover the assets. The CIS Control 1 Dashboard provides information to assist in identifying assets collected during a vulnerability scan.
For more information about the CIS Control 1 dashboard, see CIS Control 1: Inventory of Hardware Assets.
The Discover step helps organizations identify and map every asset across any computing environment. In this phase, Tenable Security Center Continuous View allows the CISO to detect assets through active scanning, passive network analysis, and event log discovery. By utilizing these three methods of discovery, the CISO can build a more complete list of hardware assets and begin to understand a clearer picture of risk on the network.
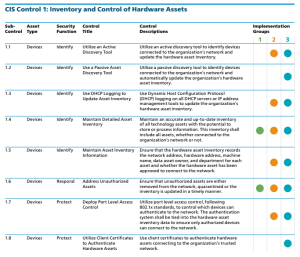
The CAS provides guidance on how to assess the organization's progress in this journey. This guide illustrates how the CISO can effectively measure progress. Shown below are the CIS Control 1 IG levels and requirements.
As shown above, the IG1 organization is required to implement Sub-Controls 1.4 - Maintain Detailed Asset Inventory and 1.6 - Address Unauthorized Assets. Some useful methods to collect data to meet these requirements include:
Active Scanning and passive Scanning, specifically:
-
ICMP/TCP/SYN/ACK identification
-
OS fingerprinting
-
Passive scanning/listening for talkers
- Pulling data from switches and routers regarding connected devices
All devices that have an IP address (whether they are wired/wireless and/or physical/virtual) are to be included in the asset inventory.