CIS Control 2: Inventory and Control of Software Assets
The focus of this control is to actively manage (inventory, track, and correct) software installed on systems within the organization. A fundamental aspect of risk management is discovering risk by tracking software present on information systems. Ensuring only authorized software is used by the organization will increase the effectiveness of risk management efforts. Being able to quickly identify unauthorized and unmanaged software can prevent security breaches and increase the productivity of users.
The CIS states this control is critical:
“Attackers continuously scan target organizations looking for vulnerable versions of software that can be remotely exploited. Some attackers also distribute hostile web pages, document files, media files, and other content via their own web pages or otherwise trustworthy third-party sites. When unsuspecting victims access this content with a vulnerable browser or other client-side program, attackers compromise their machines, often installing backdoor programs and bots that give the attacker long-term control of the system. Some sophisticated attackers may use zero-day exploits, which take advantage of previously unknown vulnerabilities for which no patch has yet been released by the software vendor. Without proper knowledge or control of the software deployed in an organization, defenders cannot properly secure their assets.
Poorly controlled machines are more likely to be either running software that is unneeded for business purposes (introducing potential security flaws), or running malware introduced by an attacker after a system is compromised. Once a single machine has been exploited, attackers often use the compromised system as a staging point for collecting sensitive information from the compromised system and from other accessible systems connected to it. In addition, compromised machines are used as a launching point for movement throughout the network and partnering networks. In this way, attackers may quickly turn one compromised machine into many. Organizations that do not have complete software inventories are unable to find systems running vulnerable or malicious software to mitigate problems or root out attackers.
Managed control of all software also plays a critical role in planning and executing system backup, incident response, and recovery.”
The journey of implementing the CIS Controls continues with inventory of software assets. Software assets are any application or program used by the organization, including operating systems. By discovering software assets, the CISO can begin to establish an inventory and can then begin assessing and mitigating the associated risks. Tenable Security Center allows the CISO to use active and passive methods to collect the software inventories. The CIS Control 2 Dashboard provides information to assist in identifying unwanted or potentially dangerous applications, therefore enabling an efficient vulnerability management program.
For more information about the CIS Control 2 dashboard, see CIS Control 2: Inventory and Control of Software Assets.
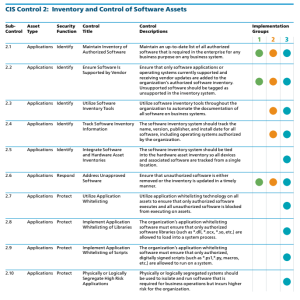
In the discovery phase Tenable Security Center Continuous View provides the CISO with the ability to detect assets through active scanning and passive network analysis. Utilizing these methods, the CISO is already transitioning from the IG1 to IG2, and is building a more complete list of software assets, and is able to better understand the current risk in the network. The CAS provides guidance on how to assess the organization's progress in this journey. Shown below is the CIS Control 1 IG levels and requirements.
As shown above, the IG1 organization is required to implement Sub-Controls 2.1 - Maintain Inventory of Authorized Software, 2.2 - Ensure Software is Supported by Vendor, and 2.6 - Address Unapproved Software. Some useful methods to collect data to meet these requirements include:
Active Scanning and passive Scanning, specifically:
-
Identify installed/detected software/applications
-
Identify software/applications that are installed on hosts
-
Identify patching/version information on detected software/applications