CIS Control 9: Limitation and Control of Network Ports, Protocols, and Services
The focus of this control is to manage (track/control/correct) the ongoing operational use of ports, protocols, and services on networked devices in order to minimize windows of vulnerability available to attackers. A common denominator is that attackers will always search for, and attempt to exploit, accessible and vulnerable network services. The most common attacks are generally against hosts such as web servers, mail servers, file and printer servers, etc.
The CIS states this Control is critical:
“Attackers search for remotely accessible network services that are vulnerable to exploitation. Common examples include poorly configured web servers, mail servers, file and print services, and DNS servers installed by default on a variety of different device types, often without a business need for the given service. Many software packages automatically install services and turn them on as part of the installation of the main software package without informing a user or administrator that the services have been enabled. Attackers scan for such services and attempt to exploit these services, often attempting to exploit default user IDs and passwords or widely available exploitation code.”
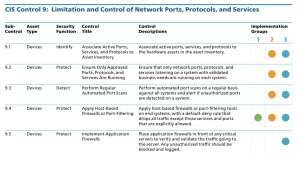
The journey of implementing the Foundational CIS Controls continues with CIS Control 9 Limitation and Control of Network Ports, Protocols, and Services. The full CIS 9 Control evolves around organizations ensuring that only those ports, protocols, and services with a validated business requirement are open/running on each system. Organizations are also directed to perform automated scans on a regular basis against all systems to ensure that unauthorized ports/services are detected. The specific sub-controls that are part of Implementation Group 1 (IG1) are:
-
9.4 Apply Host-Based Firewalls or Port-Filtering